The Cloud Journey for Engineering Firms
A 3-part eBook series to future-proof your cloud journey
A 3-part eBook series to future-proof your cloud journey
For today’s hybrid-cloud enterprises, effective user management is critical. A robust user management system ensures the right people have the right access. As workplaces evolve with remote teams, SaaS sprawl, and tighter security needs, managing identities and permissions is more important than ever.
Let’s break down what is user management, why it matters now, and how modern user access control management can protect your data and drive operational efficiency.
Let’s jump in and learn:
User management is a system to handle activities related to individuals’ access to devices, software, and services. It focuses on managing permissions for access and actions as well as monitoring usage. From onboarding and authentication to auditing and offboarding, user management includes:
Together, these user management tools form the backbone of a secure, agile enterprise.
Cloud apps, remote connectivity, and evolving regulations have raised the stakes. Modern cloud environments demand visibility across multi-cloud deployments. As a result, centralized user identity management has become essential for reducing risk and streamlining operations.
Without an advanced user management system, organizations risk shadow IT, compliance failures, and breach exposures. A strategic system with automated provisioning, seamless role changes, and audit trails keeps environments secure while supporting rapid business growth.
Cloud applications and resources require extra vigilance when it comes to user management. IT departments need to create and manage more complex policies to address the proliferation of accounts and the distribution of users.
To add to this complicated function, IT teams must track what type of user management system the various cloud service providers use. This is because user management in the cloud is handled differently depending on the type of deployment and the service provider.
User management software supports the authentication of users and storage of their data based on permissions and roles. APIs for user management software facilitate integration and streamline users’ access to applications. The user registration process, user authentication, and password management can all be handled through APIs. IT can also use consoles to manage all aspects of users’ accounts, including:
User management software can also be used to manage third-party accounts. For instance, partner accounts can be created or temporary access granted to vendors.
For SaaS, user management plays a critical role. Users, roles, and permissions must be tracked and carefully managed so that access is granted according to the terms of engagement.
Today’s user management tools can sync with directories, automate account setup through SCIM, and apply consistent access rules across cloud and on-prem systems.
Provisioning and deprovisioning: Automate onboarding/offboarding with role- or attribute-based access
Single Sign-On (SSO) and MFA: Enhance security and user experience
API integration: Seamlessly connect with cloud and on-prem systems
Session control and access reviews: Enforce timeout policies and periodic entitlement audits
Audit logging and reporting: Support compliance with GDPR, CCPA, SOX
License usage tracking: Optimize software licenses and reduce cost
Access request workflows: Streamline approvals with transparency
Passwordless options: Improve security and user satisfaction
Automation now increasingly includes machine learning algorithms that detect unusual user behavior, flag risks in real time, and assist in fine-tuning access levels dynamically.
Technologies commonly used when automating user management include:
With each of these tools, user management can be automated, eliminating the need for cumbersome, error-prone manual systems. Some of the functionality that automated user management provides is:
Onboarding and offboarding users and roles
User management software can help organizations gain productivity, security, and cost savings. Finance, HR, and IT all benefit from fewer security gaps, faster onboarding, and cost control across license lifecycles.
Automating user management with software saves time and increases efficiency by replicating changes made (e.g., creating, updating, and removing users) across systems. It also expedites the process of setting up users, roles, and groups, reducing workloads for admin teams.
User management software facilitates tracking of software usage to ensure optimal licensing. Licenses that are no longer needed can be reassigned. Agreements for software that is no longer needed can be terminated. Visibility into how many devices a user has activated under their license helps organizations optimize license distributions. It also helps with planning for future software budgeting.
With user management software, organizations can ensure compliance with licensing agreements by tracking users and their usage. This also simplifies reporting in the case of an audit.
User management software provides significant security benefits. By supporting strict access controls, unauthorized access can be prevented. In addition, the ability to quickly lock down or remove users helps mitigate risks from insiders. User management software also supports forensic audits for proactive security efforts, root cause analysis, and remediation in the event of a data breach.
The ability to enforce user access control management policies across cloud and on-prem environments further strengthens the enterprise security posture.
Understanding what is user management and implementing the right tools is now a top priority for any enterprise. With the right user management system, you can enable security, ensure compliance, and optimize cost. Modern user management software elevates your identity infrastructure from an obstacle to a business enabler.
Egnyte’s governance suite integrates key components that support robust user oversight and user access control management:
These capabilities empower IT and security teams to prevent overprivileged access, minimize risk, and maintain compliance within Egnyte’s enterprise data governance framework.
Talk to our experts to learn how Egnyte can centralize user lifecycle, shield sensitive data, and streamline admin operations without introducing unnecessary complexity.
Microsoft Active Directory is a widely used user management system. It lets organizations manage user identities, assign permissions, and control access to devices and applications across networks.
User role management assigns access based on someone’s job or responsibilities. Instead of setting permissions one by one, it groups users by role, like admin or editor, so they only see the tools and data they need. For example, a manager might have access to more features or data than a regular employee.
User management in a website controls how people sign up, log in, and interact with content. It sets rules for what each user can see or do, like viewing pages, posting comments, or managing their account settings.
A user management API helps developers handle tasks like sign-up, login, and role changes within their apps. It saves time by providing ready-made functions and ensures users get the right access across all connected systems.

Find everything you need to manage users in Egnyte—from admin vs. non-admin roles, integrations, and ...

Manage Egnyte users on the go—add, edit, or update roles directly from the mobile app.

Create tailored roles to let Power Users handle specific admin tasks without full admin access. Simplify ...
You’ve secured your networks, trained your employees, and installed the latest security tools. But here’s the reality: most breaches don’t happen because systems fail. They happen when sensitive information slips through everyday channels or gets mishandled by someone in your organization with good intentions.
That’s where true sensitive information protection starts. Not with checklists, but with awareness.
Today’s breaches bring more than just technical headaches; they lead to significant fines, legal repercussions, and long-term damage to a brand's reputation. And with regulations only getting stricter, the cost of getting it wrong continues to rise.
Sensitive information protection isn’t about ticking compliance boxes anymore. It’s about knowing where your data resides, implementing smart controls, and fostering a security culture that scales with your business.
Let’s jump in and learn:
Sensitive information refers to any type of data that could cause harm to individuals, organizations, or business operations if improperly handled or disclosed. This definition extends well beyond obvious examples, such as credit cards or Social Security numbers.
Your organization likely handles numerous types of data that require varying levels of protection based on their potential impact.
The key to effective sensitive information protection lies in understanding context. Information sensitivity often depends on factors like industry regulations, contractual obligations, competitive implications, and potential harm to individuals or the organization.
When evaluating whether information qualifies as sensitive, consider these critical factors:
Building effective protection strategies requires understanding these nuances rather than applying comprehensive security measures. The goal is to create proportional responses that match the actual risk level of different types of information.
Personal information represents one of the most regulated categories of sensitive data. Traditional Personally Identifiable Information (PII) includes obvious identifiers, but the scope has expanded dramatically with digital transformation and evolving privacy regulations.
Classic sensitive information examples include well-known data elements like Social Security numbers, financial account details, physical addresses, medical records, and educational history. However, modern personal information extends far beyond these traditional examples.
Digital interactions create new categories of identifying information that require protection. Digital identifiers such as IP addresses, device fingerprints, and login credentials can link activities to specific individuals. Behavioral data, including browsing patterns, location history, and usage analytics, can create detailed profiles of individual preferences. Biometric information, such as fingerprints and facial recognition data, represents permanent characteristics that cannot be altered if compromised.
Sensitive information examples in the personal category now encompass financial records, health information, biometric data, racial or ethnic background, religious beliefs, and political affiliations. Organizations collecting such information must provide clear disclosure about its use and obtain appropriate consent before processing.
Business information represents the intellectual capital and operational knowledge that differentiates your organization in the marketplace. This category often receives insufficient attention because its value may not be immediately apparent to all stakeholders.
Critical business information requiring protection includes strategic intelligence such as merger and acquisition plans, market expansion strategies, and competitive analysis. Financial data, including revenue forecasts, pricing models, and cost structures, provides competitors with valuable insights. Intellectual property, such as trade secrets, proprietary algorithms, and research data, represents core competitive advantages that require the highest level of protection.
Many professionals use the terms "confidential" and "sensitive" interchangeably, but understanding their distinct meanings is crucial for implementing appropriate protection measures and access controls.
Understanding confidential vs sensitive information influences access control design, storage requirements, handling procedures, and incident response protocols. Confidential information requires stricter authorization mechanisms, enhanced encryption standards, special transmission methods, and more severe response protocols compared to general sensitive information.
Effective sensitive information protection requires a structured approach to categorizing information based on its sensitivity level and potential impact if disclosed. Most successful organizations implement a four-tier classification system that strikes a balance between security requirements and operational efficiency.
Public information includes data that can be shared openly without risk to the organization or individuals. This includes marketing materials, press releases, published research, and general company information intended for public consumption. While requiring no protection controls, organizations should maintain version control, ensure brand consistency, and conduct regular reviews to prevent accidental inclusion of sensitive details.
Internal information is intended for use within the organization but poses minimal risk if disclosed externally. This includes routine business communications, internal policies, organizational charts, and standard operating documents. Internal information requires basic access controls, standard backup procedures, and regular updates to remove outdated materials.
Confidential information requires careful access control and could cause significant harm if inappropriately disclosed. This category includes sensitive business strategies, detailed financial information, customer data, and proprietary processes. Protection requires role-based access controls, encryption for storage and transmission, comprehensive audit logging, and formal approval processes for external sharing.
Restricted information represents the highest-risk category, where unauthorized disclosure could result in severe consequences, including legal liability, major financial losses, or business failure. This requires multi-factor authentication, end-to-end encryption with robust key management, continuous monitoring with real-time alerting, and strict 'need-to-know' access principles.
Protecting sensitive information requires combining technical security measures with administrative controls and user awareness programs. Effective protection strategies address both external threats and internal risks while maintaining operational efficiency.
Technical controls form the backbone of any sensitive information protection strategy. These controls should work together to create a layered defense mechanism that protects data throughout its lifecycle.
Administrative controls establish the policies, procedures, and governance structures that guide organizational handling of sensitive information. These controls provide the framework within which technical measures operate.
Sustainable sensitive information protection requires ongoing commitment to security practices that evolve with changing business needs and threat landscapes. Effective protection strategies strike a balance between security requirements and operational efficiency, while maintaining long-term viability.
Implement automated tools that continuously scan systems to identify and classify sensitive information as it appears. Manual classification processes cannot keep pace with the rapid growth of modern data creation, making automation essential for comprehensive coverage.
Conduct periodic assessments that identify new threats, evaluate control effectiveness, and prioritize security investments based on actual risk levels. Risk assessments should consider both external threats and internal vulnerabilities while addressing changing business conditions.
Develop comprehensive training programs that enable employees to understand their responsibilities and make informed, security-conscious decisions. Training should be role-specific, regularly updated, and reinforced through ongoing communications.
Assist organizational cultures that prioritize security considerations in daily activities. This includes leadership commitment, clear expectations, and recognition programs that reward security-conscious behavior.
Implement security technologies that integrate seamlessly with existing business processes. Security solutions should enhance productivity while providing comprehensive protection, rather than hindering it.
Maintain robust incident response capabilities that can swiftly address security breaches while minimizing the impact on business operations. This includes regular testing, staff training, and coordination with external partners.
Protecting sensitive information requires more than implementing basic security measures or checking compliance boxes. It requires a comprehensive understanding of your data landscape, the thoughtful implementation of appropriate controls, and an ongoing commitment to security practices that evolve with your business.
Effective sensitive information protection starts with accurately identifying sensitive information examples within your specific environment and implementing proportional safeguards that address actual risks. This includes understanding the distinction between confidential vs sensitive information and applying appropriate controls based on these classifications.
Platforms like Egnyte can support these efforts by providing integrated solutions for data classification, access control, data governance solutions, and compliance management. These tools help organizations implement comprehensive protection strategies while maintaining the operational efficiency necessary for business success.
Any data that could harm your business, customers, or employees if disclosed. This includes customer records, financial data, employee information, business strategies, and intellectual property.
Confidential information causes significant harm if disclosed and needs strict access controls. Sensitive information requires protection, but may have broader access. Ask: "What's the worst-case impact?"
Start with basic controls like access restrictions, encryption, and employee training. You can add advanced tools as your program matures and budget allows.
Review access quarterly for most sensitive data, monthly for highly confidential information. Set up automated alerts when employees change roles or leave the company.
A: Trying to protect everything equally instead of focusing on truly critical data first. Start with your highest-risk information and build your program from there.

A quick overview of what qualifies as sensitive data and why organizations must protect it from ...

Connect SharePoint, OneDrive, or Exchange in minutes to begin automated sensitive data scanning.
Navigate to Content Classification to apply pre-configured policies aligned with global legal jurisdictions.
Unstructured data is a collection of different types of data stored in the original format created by users or systems, without a rigid, predefined schema. Usually text-heavy, unstructured data cannot be stored in spreadsheet rows and columns like CSV files. This includes content such as emails, documents, chat logs, images, audio, video, and IoT sensor feeds.
Let’s jump in and learn:
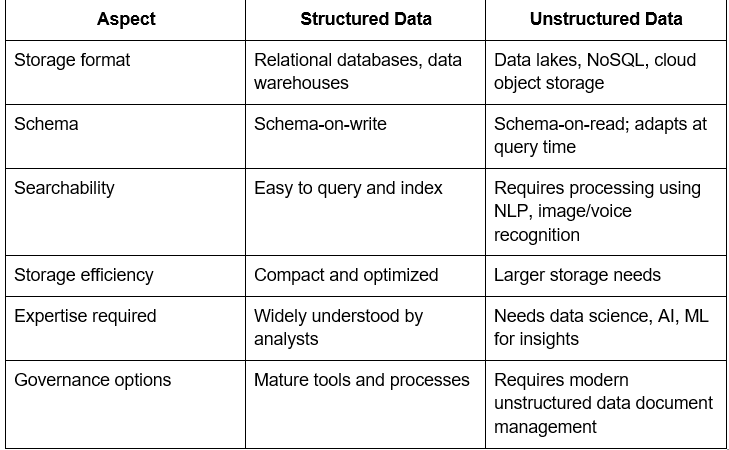
This table helps illustrate what are the characteristics of unstructured data, such as flexibility, scale, and complexity.
The types of unstructured data are broad and include both human- and machine-generated content, including:
Text files, reports, presentations
Enterprises tap into unstructured data for valuable insights. These applications of unstructured data show how it drives innovation across industries:
Regulatory and compliance audits by analyzing document metadata.
Unstructured data typically resides in:
These modern solutions provide scalable, cost-effective unstructured data storage and easy integration with analytics pipelines.
Extracting value from unstructured data begins with choosing the right analytics approach for the right problem. Each method answers a different business question and gives unique insights. These methods rely on key technologies like natural language processing (NLP), machine learning classifiers, semantic analysis, graph analytics, and neural embeddings.
Securing unstructured data is critical. Below are modern best practices, guidelines for a modern approach to unstructured data security and protection.
Effective unstructured data governance covers classification, retention, access, and deletion. Such governance ensures data privacy for unstructured data and reduces legal exposure. It includes:
Regular audits and analytics to ensure compliance and minimize risk.
Security, governance, and productivity converge under unified unstructured data document management. Organizations now rely on cloud-driven platforms offering unstructured data services such as:
The shift from rigid systems to dynamic, AI-powered content analysis changes how businesses compete. Making unstructured data manageable and secure leads to:
By understanding what is unstructured data, its formats, applications, and security requirements, organizations can transform untapped information into practical insights that drive real outcomes. With the right data governance tools and policies in place, unstructured data shifts from a governance liability to a strategic asset.
Egnyte helps make that shift possible. Our platform unifies unstructured data storage, real-time threat detection, AI-based classification, GDPR compliance, and robust document management into a single, easy-to-manage solution. This gives IT and compliance teams the visibility and control they need, without slowing down productivity.
Unstructured data is any information that doesn’t follow a set format or structure. It includes files like emails, videos, social media posts, and scanned documents. This data is usually stored as-is and can’t be easily organized in rows and columns.
No, a CSV file is structured data. It stores information in rows and columns, making it easy for both humans and machines to read and process.
JSON is considered semi-structured data. It has an internal structure that helps store information, but it doesn’t follow the strict table format of structured data found in databases or spreadsheets.
Understand the key differences between structured and unstructured data—and how organizations use both for analytics ...

Insider threats are rising. Learn how Egnyte protects sensitive content with continuous monitoring, smart permissions, and ...

Digital data management involves securing, storing, and organizing information to support business processes and regulatory compliance.
You plan for growth, performance, and customer success. But planning for disruption? That’s what separates resilient organizations from the rest. When systems fail or operations stall, your response doesn’t just shape recovery; it shapes how your business is perceived, trusted, and remembered.
Business continuity is about building that capability. It's not just a reactive plan for emergencies; it's a proactive approach to maintaining stable operations, minimizing disruptions, and preserving customer trust in times of uncertainty. For leaders and teams alike, it's the strategic framework that ensures the show goes on.
This guide serves as a clear and actionable introduction to business continuity. We’ll break down its essential elements, explain key roles and responsibilities, and help you understand how to create a robust plan that aligns with your organizational goals.
Let’s jump in and learn:
Business continuity is your organization’s ability to maintain essential operations during and after a disruption. To define business continuity in simple terms, it’s what ensures that critical functions, like customer support, transactions, or access to data, keep running even if your key systems go down or your teams can’t access the office.
Consider this scenario:
If one of your core business facilities experiences a power outage, a strategic business continuity plan enables you to shift operations to an alternate location, notify stakeholders, and maintain delivery timelines. Instead of reacting under pressure, you're executing a predefined response that limits downtime and protects revenue.
While disaster recovery focuses on restoring IT systems, business continuity takes a broader view. It aligns people, processes, infrastructure, and communication to help you respond effectively and maintain business as usual, even when circumstances are anything but.
The importance of having a business continuity plan cannot be overstated. Let’s explore why it matters to organizations:
A solid business continuity plan helps you ensure that your organization can continue critical operations even in times of crisis. By preparing ahead of time, you can minimize downtime and continue to deliver value to your customers. This is especially crucial for enterprise business continuity, where even brief disruptions can have significant, far-reaching effects.
A proactive continuity plan reduces the impact of disruptions by identifying vulnerabilities in advance and establishing response protocols. This minimizes the likelihood of extended outages and helps contain their fallout.
The financial consequences of downtime, ranging from lost revenue and compliance penalties to reputational damage, can be severe. A sound BCP helps mitigate these risks with predefined measures that accelerate recovery and reduce exposure.
Many industries, especially healthcare, finance, and manufacturing, have regulations requiring businesses to be able to demonstrate how they’ll continue operations during a crisis. A business continuity plan helps ensure compliance with these requirements.
Your customers expect consistency, even during disruptions. A visible, well-executed continuity plan builds trust by showing your organization is prepared, responsible, and focused on delivering uninterrupted service. This confidence can be a competitive differentiator, especially when your business operates in sectors where reliability and uptime are critical to customer success.
A Business Continuity Plan (BCP) is more than just a checklist of tasks. It is a detailed document that provides a clear strategy for maintaining operations during a crisis.
Let’s break down the essential components of a successful BCP:
This is the foundation of your plan. It defines the purpose of the BCP, outlines the scope of the plan, and sets clear goals. It also involves identifying the critical functions of your organization and determining the resources required to maintain them during a disruption. One key consideration is understanding what is the goal of a business continuity plan, which is to minimize operational disruption and ensure long-term sustainability.
It’s essential to assign clear roles to the business continuity team to ensure that everyone knows what’s expected of them. Your plan should outline the following:
This step solidifies the business continuity team's roles and responsibilities required for effective execution.
Most modern organizations depend heavily on IT infrastructure. In your business continuity plan, you’ll need to ensure that your technology stack (cloud systems, mobile devices, networks, etc.) is included. The plan should address:
Clear, concise communication is essential during a crisis. Your business continuity plan should outline how you will communicate with internal teams, customers, and stakeholders. This includes setting up emergency contact lists and protocols for ensuring smooth communication channels are maintained.
Your business continuity plan is a living document that must be regularly tested and updated. Simulation exercises help ensure that the plan works when needed and that all stakeholders know their responsibilities.
A business continuity plan is only as effective as the people who implement it. Defining the business continuity team's roles and responsibilities with clarity ensures that every team member knows exactly what to do before, during, and after a disruption.
This level of coordination is crucial for reducing response time, minimizing confusion, and maintaining operational control during a crisis. In this section, we outline the critical roles that make up a strong business continuity team and how each contributes to the overall success of your plan.
Creating an effective business continuity plan requires a structured, methodical approach. Each step builds upon the last to form a plan that’s not only comprehensive but also practical during real-world disruptions. Here’s how to develop a business continuity plan that aligns with your organization’s operational priorities and risk profile:
Start by identifying potential threats to your operations, which could include cyberattacks, supply chain disruptions, natural disasters, or internal system failures. Evaluate how each scenario could impact your core functions, revenue, compliance obligations, and customer service.
A Business Impact Analysis (BIA) quantifies these risks and highlights which disruptions would have the most serious consequences, helping you prioritize your planning.
Once you understand the risks, determine which business functions are essential to sustain operations. These are your non-negotiable processes that must remain operational or be quickly restored, such as customer support, payment systems, data access, or manufacturing lines.
For each function, identify the minimum service levels acceptable during a disruption and the dependencies they rely on (for example, IT systems, personnel, vendors).
With critical functions identified, outline how you’ll keep them running or restore them as quickly as possible. Your recovery strategy may include:
The goal is to restore operations within your acceptable Recovery Time Objective (RTO) and Recovery Point Objective (RPO).
Even the best-documented plan can fall short if it hasn’t been tested. Regular testing through tabletop exercises, simulation drills, or live scenario walkthroughs validates the effectiveness of your plan and highlights any gaps. It also makes sure team members understand what business continuity is and their responsibilities.
By leveraging workflow integrations with platforms like email, collaboration suites, and real-time messaging apps, teams can maintain access to the latest files, updates, and templates without jumping between systems.
A solid communication strategy should outline:
Having pre-defined templates and documents synced across integrated systems ensures that messages are consistent, accurate, and quickly deployable, both internally and externally. This reduces confusion and keeps all stakeholders aligned when it matters most.
A plan is only effective if people know how to use it. Conduct ongoing training sessions to familiarize employees with emergency procedures, their specific responsibilities, and the tools available to them. This builds confidence and speeds up response times when real incidents occur.
Your business continuity plan should be regularly updated to reflect changes in your organization. Aim to review it at least once a year, or whenever there are major changes, like new technologies, regulatory updates, or shifts in operations. Keep contact details, vendor agreements, and key documentation up to date so the plan remains practical and ready to use when needed.
A well-built BCP requires the proper infrastructure to support it. Here’s how leading teams apply continuity best practices using Egnyte:
Continuous optimization: Your BCP should evolve with your business. Egnyte’s cloud content platform enables this with real-time visibility into file access patterns, risk exposure, and compliance gaps. Hence, making it easier to spot vulnerabilities and adapt proactively.
Cross-functional readiness: Continuity isn’t an IT-only exercise. Egnyte’s centralized data governance framework enables departments such as IT, legal, HR, and compliance to collaborate securely from anywhere, ensuring everyone operates from the same version-controlled, policy-governed content.
Smart automation: Through automated backups, access controls, and content lifecycle management, Egnyte helps teams minimize downtime and reduce the burden of manual oversight during a disruption.
Secure, scalable cloud access: Egnyte’s cloud architecture ensures employees can securely access critical files, whether they’re in the office, remote, or across regions. Built-in ransomware detection and zero-trust access models further protect continuity without compromising flexibility.
Business continuity is a critical part of your organization’s resilience strategy. A well-crafted business continuity plan ensures that no matter what disruptions occur, you’re prepared to keep your business running smoothly.
By focusing on the essential elements like strategy, roles, technology, and communication, you can confidently face any challenge that comes your way.
Platforms like Egnyte can significantly ease the process by providing reliable cloud-based solutions that support remote work, data recovery, and seamless collaboration for businesses. With such platforms in place, your enterprise business continuity efforts will be more effective, scalable, and adaptable to future challenges.
While disaster recovery focuses specifically on restoring IT systems and data after an incident, business continuity takes a broader view. It ensures that all essential business functions, personnel, processes, infrastructure, and communication remain operational or recover quickly in the event of a disruption.
Ownership should start at the leadership level. While IT plays a major role in execution, senior leadership must drive the plan to align it with strategic priorities. Specific roles—from operations to compliance should be clearly defined within a cross-functional team.
A business continuity plan should be reviewed at least annually, or any time your organization undergoes significant changes, such as adopting new technologies, expanding operations, or entering regulated markets. Regular testing through simulations or drills is essential to ensure the plan remains effective and actionable.
Integrated platforms streamline access, communication, and data governance across departments. By enabling real-time file access, automated backups, and cross-functional collaboration, these tools reduce manual overhead and improve response speed, making continuity plans more resilient and easier to execute.

How Egnyte helps teams stay productive during disruptions with remote access, mobile tools, and offline sync.

Learn how global IT leaders are reshaping file sharing, collaboration, and governance for a post-COVID world.

Learn the core backup principles—from retention planning to encryption—to protect data and speed recovery ...
Can your team find every critical document when it matters most?
During audits, mergers, or rapid expansion, disorganized systems and missing records can cause costly delays. +Without a formal document retention policy, regulatory risk grows unchecked. For example, SEC rules require accounting firms to retain audit records for seven years. Failure to comply has resulted in settlement penalties reaching hundreds of millions of dollars.
A strategic document retention policy transforms this exposure into an operational strength. It closes compliance gaps, streamlines workflows, and helps you maintain control during periods of scrutiny or change.
Let’s jump in and learn:
A document retention policy establishes systematic protocols that govern how organizations capture, store, access, and dispose of business records. This strategic framework defines precise retention periods for different document categories. It ensures compliance with regulatory mandates while optimizing storage resources.
Effective document retention guidelines encompass three components. Classification systems categorize documents by business function. Retention schedules specify preservation periods. Disposal procedures ensure the secure destruction of expired records.
A clear document retention policy ensures records are stored systematically, retained for required durations, and easily retrievable during audits, investigations, or litigation.
Without it, organizations face the risk of non-compliance, costly penalties, and delayed legal responses. Regulatory bodies like the SEC and GDPR demand strict recordkeeping standards, and failure to comply can lead to severe consequences.
With a structured policy in place, legal teams gain faster access to relevant documents, enabling accurate, timely responses and reducing exposure during legal reviews or regulatory inquiries.
Developing an effective document retention policy requires systematic analysis. Follow these essential steps:
Data governance platforms streamline policy creation through automated classification capabilities.
Non-profit organizations face unique retention challenges. They must balance regulatory compliance with resource constraints and donor accountability:
Successful policy implementation requires phased deployment strategies. These minimize operational disruption while ensuring comprehensive coverage.
Data retention policy best practices emphasize automated platforms that enforce schedules without continuous human intervention.
Smart document retention does more than check compliance boxes. It compounds value across your organization by tightening governance, reducing overhead, accelerating decision-making, and strengthening legal defensibility. In fact, the U.S. Supreme Court (Arthur Andersen LLP v. United States, 544 U.S. 696, 704 (2005)) affirmed that managers can and should enforce document retention policies, even if those policies limit disclosure.
This is a legally supported strategy. A robust retention policy acts as both a legal safeguard and an operational asset, enhancing organizational agility and long-term resilience.
Egnyte makes this strategy actionable. Its intelligent platform empowers organizations to automate retention schedules, classify sensitive data, enforce compliance policies, and generate audit-ready reports without adding administrative burden.
DeBacco Law, an Ohio-based litigation firm, struggled with paper-heavy workflows that slowed down document retrieval, strained productivity, and increased storage costs. Managing sensitive legal files across criminal defense, personal injury, and contract cases became increasingly inefficient.
To address this, the firm implemented Egnyte’s cloud-based document management platform, streamlining access to case files and reducing operational overhead.
Key Outcomes:
With Egnyte, DeBacco Law now spends less time managing documents and more time delivering high-quality client service.
Read the full case study here.
In today’s regulatory and risk-aware landscape, document retention is a cornerstone of operational resilience, legal readiness, and strategic control. From protecting sensitive records to enabling faster audits and reducing overhead, a strong retention policy drives efficiency and trust across the organization.
Egnyte makes this easy. Its intelligent platform automates classification, enforces retention rules, and delivers audit-ready visibility across your entire content lifecycle. For organizations ready to simplify governance and scale with confidence, Egnyte turns retention into a strategic advantage.
Tax returns, financial statements, employment records, and client communications require seven-year retention under federal regulations. This includes IRS documentation, SEC filings, and payroll records.
The IRS requires a minimum retention of three years for tax returns and supporting documentation. Six-year retention applies to significant income underreporting. Seven years apply for bad debt deductions.
GAAP mandates permanent retention of general ledgers, financial statements, and audit reports. Supporting documentation requires a seven-year minimum retention. Transaction records need three to seven years based on materiality.
Retention periods vary by document type and industry. Business records typically require 3-7 years. Corporate formation documents need permanent retention. Healthcare records require 6+ years.
A standard retention policy defines systematic document lifecycle management. It includes classification systems, retention schedules, and disposal procedures. Effective policies encompass all information formats, including digital files and cloud-stored data.

A comprehensive guide to understanding data retention laws, industry regulations, lifecycle management, and the practical steps ...

Everything you need to research regulations, categorize data, implement controls, and maintain a secure, compliant retention ...

Understand how fallback retention is applied, what date it uses, and when it takes precedence.
For federal agencies and their partners, data is a mission-critical asset. From national infrastructure to public-facing services, secure and uninterrupted access to sensitive information underpins every function. However, in today’s evolving threat landscape, traditional security methods no longer suffice.
To meet rising expectations around risk mitigation and regulatory compliance, organizations must adopt a unified, standards-based cybersecurity approach. FedRAMP compliance provides a structured framework to validate security posture and ensure readiness to serve the federal market.
This blog explores how aligning with FedRAMP requirements not only strengthens security controls but also positions your organization to operate with greater confidence, credibility, and access to high-value federal opportunities.
Let’s jump in and learn:
The Federal Risk and Authorization Management Program (FedRAMP) is a standardized cybersecurity framework for cloud service providers working with U.S. federal agencies. It streamlines cloud adoption by replacing redundant agency-specific assessments with a unified authorization process, enabling faster, secure deployment across government entities.
FedRAMP mandates rigorous security assessments, continuous monitoring, and standardized authorization processes for cloud service providers.
Key elements of the program include:
Select either the Agency ATO route or the Joint Authorization Board (JAB) P-ATO path, depending on your federal market strategy and sponsor engagement.
Create the System Security Plan (SSP) and other required documentation that outlines your cloud system’s architecture, controls, and risk posture, mapped to NIST 800-53 controls.
Partner with a FedRAMP-accredited Third Party Assessment Organization (3PAO) to conduct an independent security assessment.
The 3PAO performs penetration testing, vulnerability scans, and control testing to produce a Security Assessment Report (SAR).
Address any findings or gaps identified in the SAR. Document your remediation actions and update the security package accordingly.
Submit the complete security package (SSP, SAR, POA&M) to the authorizing body (Agency or JAB) for review and approval.
If approved, you receive an Agency Authority to Operate (ATO) or Provisional ATO (P-ATO) from the JAB, allowing you to serve federal customers.
Begin ongoing compliance activities, including monthly vulnerability scans, annual security assessments, incident reporting, and system updates to maintain your authorization status.
FedRAMP compliance is mandatory for all Cloud Service Providers that handle federal data on behalf of U.S. government agencies. This includes:
FedRAMP authorized cloud service providers who must maintain ongoing compliance through continuous monitoring and periodic reassessment
Successful organizations approach FedRAMP authorization with strategic planning and early coordination. This reduces delays and strengthens long-term compliance readiness.
To achieve and maintain FedRAMP authorization, CSPs must complete the following:
Prepare mandatory documents like the System Security Plan (SSP), which outlines how your system meets FedRAMP controls. Use FedRAMP templates for consistency.
Categorize your information system’s security impact level (Low, Moderate, or High) under FIPS 199 guidelines, which determines the scope of security controls required.
Engage a Third-Party Assessment Organization (3PAO) to review your system for compliance gaps. This ensures you're prepared for the full authorization process.
Address any identified vulnerabilities or control deficiencies. Outline remediation steps and timelines in the POA&M document.
Choose either the Agency-sponsored or JAB (Joint Authorization Board) path. Undergo formal security assessment, submit results, and obtain a FedRAMP Authorization to Operate.
After authorization, submit monthly security reports, scan results, and incident reports. Continuous monitoring ensures ongoing compliance and risk mitigation.
Modern document management systems streamline compliance documentation by automating version control, access tracking, and audit trails required for FedRAMP authorization.
Automated data governance platforms accelerate compliance preparation by automatically classifying data, tracking access patterns, and generating audit reports required for FedRAMP authorization.
FedRAMP outlines three impact levels based on the potential impact of a security breach. Each level maps to specific controls and assessment procedures aligned with the sensitivity of the data and systems involved.
Impact Levels and Requirements:
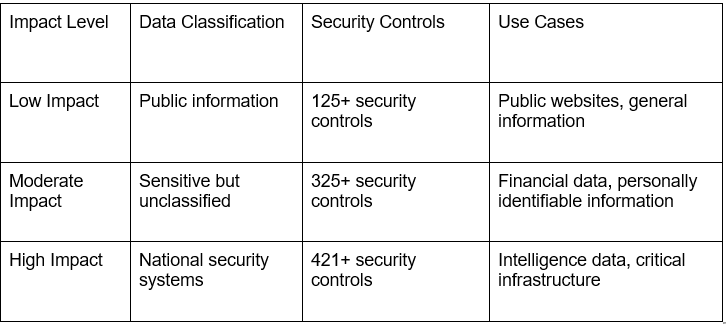
Organizations processing highly sensitive data should consider FedRAMP High authorization requirements, which provide the most comprehensive security protections available under the framework.
Achieving FedRAMP compliance is a strategic enabler. Once authorized, cloud service providers can serve multiple government agencies without redundant approvals, significantly expanding their market reach and contract eligibility. This cross-agency trust model streamlines procurement, speeds up deployment timelines, and builds a foundation for long-term federal partnerships.
Egnyte accelerates this journey with its secure, compliant-ready content platform. With granular permission controls, robust encryption, audit-ready reporting, and data residency support, Egnyte helps providers align with FedRAMP controls from day one.
For federal customers, Egnyte delivers an intuitive, integrated environment to manage unstructured content securely, whether it's sensitive documents, project data, or collaborative files.
FedRAMP compliance solutions do more than help you meet requirements. They show you're equipped to lead in high-trust federal environments. It's not just about eligibility. It's about demonstrating you're built for the highest level of operational readiness.
Turn FedRAMP compliance into a strategic advantage with Egnyte’s unified governance platform. Proven across federal environments, our solutions simplify authorization and automate ongoing compliance for long-term efficiency and security.
FedRAMP compliance means your cloud service has undergone rigorous security assessment and received government authorization to process federal data.
Organizations can pursue Agency Authorization through specific federal departments or Joint Authorization Board approval for government-wide use.
While designed for federal agencies, FedRAMP compliance enables access to lucrative government contracts and demonstrates security leadership.
The certification process includes readiness assessment, documentation preparation, third-party security evaluation, and authorization decision requiring 12-24 months.
Major FedRAMP authorized cloud service providers include Amazon Web Services, Microsoft Azure, Google Cloud Platform, and specialized solutions.

Explore the core NIST-aligned security requirements that form the foundation of federal cloud trust.

FedRAMP provides a unified security standard that accelerates cloud adoption and ensures consistent protection across government ...

Egnyte has earned FedRAMP Moderate Equivalency and joined the FedRAMP Marketplace, enabling secure collaboration for DoD ...
Your enterprise holds a wealth of data, but without proper governance, much of its potential remains unrealized. Disconnected oversight and inconsistent data quality continue to cost organizations time, money, and trust. This is no longer a back-office issue. Gartner projects that by 2027, 60% of organizations will underperform on key business outcomes due to weak data governance. That kind of gap puts competitiveness at risk.
Data stewardship provides the foundation for turning raw data into reliable, strategic insight. It ensures information is accurate, accessible, and compliant across systems. More than a checkbox, stewardship is an ongoing commitment to maintaining and improving data integrity throughout the organization.
By clearly defining ownership, enforcing governance standards, and promoting data management collaboration across teams, businesses can turn scattered data into consistent intelligence. The result is smarter decision-making, greater operational efficiency, and a clear path to long-term resilience.
Let’s jump in and learn:
At its core, data stewardship bridges the gap between strategic goals and day-to-day data operations by assigning clear responsibilities to data stewards across departments.
A strong data stewardship model outlines roles and enforces policies that uphold data integrity throughout its lifecycle. These responsibilities typically include:
Depending on business complexity, there may be different types of data stewards, such as business stewards, technical stewards, and operational stewards, each tasked with specific governance duties aligned to their domain expertise.
Data stewards function as the critical bridge between raw information and strategic business value. The data steward approach emphasizes accountability and ownership rather than passive maintenance. Stewards actively champion data initiatives, evangelize best practices, and ensure that information assets support business objectives.
Organizations without dedicated stewards typically experience fragmented data landscapes, inconsistent quality standards, and reactive problem-solving approaches. These limitations compound over time, creating technical debt that becomes increasingly expensive to remediate as data volumes grow.
Successful data stewardship programs require structured frameworks that define roles, establish processes, and measure outcomes. The data stewardship model should align with organizational maturity levels while providing clear pathways for continuous improvement and scalability.
Here are some common data stewardship activities carried out to maintain data quality and governance across an organization:
Data quality monitoring: Ensures accuracy, completeness, and consistency of data
Metadata management: Maintains clear context and lineage of data across systems
Policy enforcement: Applies data stewardship policies for compliance and standardization
Data classification and tagging: Organizes data for better governance and access control
Issue resolution and data cleansing: Identifies and fixes inconsistencies or errors in data
Stewardship reporting: Tracks stewardship effectiveness and highlights data governance metrics
Role-based access oversight: Ensures appropriate access rights across users and departments
Collaboration with data owners: Aligns on data ownership vs stewardship responsibilities
Modern enterprises generate and store data across dozens of systems, making governance more complex than ever. This is where the data steward steps in, serving as both a record keeper and a strategic enforcer of data trust. Think of them as the digital data sheriff: They ensure that data is accurate, properly classified, securely shared, and fully compliant with internal and external policies.
But policy alone is not enough. Execution demands the right tools.
Data stewardship is only as effective as the tools that support it. While policies and roles define the framework, platforms like Egnyte enable real execution at scale.
Egnyte enables organizations to operationalize data stewardship through a governance framework that centralizes control over unstructured content. By embedding policy enforcement directly into everyday workflows, Egnyte empowers data stewards to move beyond passive oversight and take an active role in managing compliance, privacy, and data quality. It provides unified visibility across repositories, applies automated classification and retention policies, and enforces access controls at scale.
A major healthcare network struggled with disparate data systems across multiple facilities, creating compliance risks and hindering patient care coordination. Manual data quality processes couldn't scale with their growth, leaving critical information gaps that impacted operational efficiency.
By implementing Egnyte's enterprise data governance platform, the healthcare system automated data discovery, classification, and quality monitoring across all facilities. The integrated stewardship tools enabled the organization to:
This transformation positioned the healthcare system as a leader in data-driven patient care while significantly reducing compliance risks and operational costs.
As the volume and complexity of information grow, so does the risk of poor data quality, non-compliance, and missed opportunities. A robust data stewardship model transforms fragmented datasets into trusted assets that fuel intelligent decisions and regulatory confidence.
With role-based dashboards tailored to different types of data stewards, Egnyte makes stewardship a measurable, enterprise-wide function, aligning governance with business agility.
A data steward is typically a business analyst in the finance department who ensures customer transaction data meets quality standards for regulatory reporting. They monitor data accuracy, resolve discrepancies, and coordinate with IT teams to maintain compliance with financial regulations.
Data stewardship responsibilities include establishing data quality standards, monitoring compliance with governance policies, resolving data-related issues, and facilitating communication between technical and business teams to ensure information assets support organizational objectives effectively.
APN (Application Performance Network) monitoring provides data stewards with visibility into how applications handle data processing, enabling them to identify performance bottlenecks and quality issues that could impact stewardship effectiveness and business operations.
The data stewardship definition centers on proactive accountability for data quality. Unlike data ownership vs stewardship, where owners control access, stewards focus on accuracy, governance, and aligning data with business goals.
Fair data stewardship ensures that data governance practices balance stakeholder needs while maintaining ethical standards. It involves transparent policies, equitable access controls, and consistent application of quality standards that serve both business objectives and broader societal interests.

A concise guide to building a scalable, business-aligned data governance strategy that grows with your organization

A beginner-friendly overview of data governance and its role in building secure, compliant, and efficient data ...
An easy-to-follow guide covering core features, automation benefits, compliance needs, and questions that help you compare ...
As your IT environment expands, so does the need for smarter oversight. Managing systems manually is simply not scalable, and that’s where Remote Monitoring and Management (RMM) proves its value.
RMM gives you a centralized way to monitor system health, automate routine maintenance, and respond to potential issues before they disrupt operations. It helps you maintain a stable environment and keeps your team focused on strategic priorities.
Whether you’re leading internal IT or delivering services as a Managed Service Provider (MSP), RMM helps you stay ahead of the curve. In this guide, we’ll break down what RMM is, what it enables, and how it drives more efficient, reliable IT operations.
Let’s jump in and learn:
The RMM solution is designed to help IT administrators and MSPs remotely monitor, manage, and maintain IT infrastructure from a centralized console. This includes everything from servers and endpoints to networks and mobile devices.
With an RMM agent installed on each asset, real-time performance data is continuously fed to a central dashboard, enabling technicians to detect issues early, automate routine tasks, and resolve problems without needing to be on-site.
The best remote monitoring software combines a robust set of capabilities designed to automate workflows, enhance security, and streamline IT operations. These features work seamlessly to provide full visibility and control across your environment.
Deploying an RMM requires careful planning. To ensure a successful implementation, you should consider the following:
When selecting the best remote monitoring software, prioritize platforms that offer a robust and integrated feature set. Look for a solution that combines:
These capabilities are essential for maintaining secure, efficient, and resilient IT environments, whether you're managing internal infrastructure or supporting clients at scale.
Remote Monitoring and Management is a strategic approach to IT operations. It transforms reactive, chaotic IT support into a proactive, efficient, and resilient function. The right RMM solution gives teams visibility into issues before they escalate and the ability to resolve them remotely, ensuring business continuity, security, and scalability.
That’s exactly what Egnyte delivers.
With Egnyte, Managed Service Providers (MSPs) gain centralised oversight, automated governance, and cloud-first control, all from a single platform. It empowers teams to enforce compliance, manage risks, and deliver seamless support no matter where endpoints or users are located.
For Kinetix, a managed service provider focused on biotech, consistent access and uptime weren’t just expectations; they were requirements. With Egnyte, the team gained centralized control, automated governance, and a streamlined approach to IT operations. It gave them the confidence to support their clients reliably and stay ahead of compliance demands.
Biotech-focused MSP Kinetix turned to Egnyte to modernise its IT operations. The results speak volumes:
When 70% of organizations face serious disruption after a data breach, it’s clear that reactive fixes and limited visibility aren’t enough. IT teams must stay ahead of issues, and that’s exactly what Remote Monitoring and Management (RMM) makes possible. With real-time insights and remote control, RMM helps resolve problems before they impact users or operations.
But system health is only half the story.
Your data is the other half, constantly in motion across devices, clouds, and endpoints. If it’s not governed, it’s exposed.
That’s where Egnyte comes in. With unified content governance, Egnyte brings proactive control to your data layer. It secures unstructured content, simplifies compliance, and ensures visibility across your environment.
RMM protects your infrastructure. Egnyte protects your data. Together, they help you stay secure, compliant, and ready for what’s next.
Yes, when properly configured. Reputable RMM solutions use strong encryption, multi-factor authentication, and role-based access controls to secure remote connections, ensuring that IT management is performed safely.
Absolutely. A cloud based RMM is highly scalable and cost-effective, allowing small businesses to automate IT tasks and receive enterprise-level support without the need for a large, dedicated IT staff.
Evaluate your specific needs. Look for a tool with robust automation, real-time alerting, seamless integrations, and strong security features. Comparing options to find the best remote monitoring software for your environment is key.
The RMM definition covers broad IT infrastructure like servers and desktops, focusing on performance and maintenance. MDM (Mobile Device Management) focuses specifically on securing and managing mobile devices like smartphones and tablets.
RMM is focused on the health and performance of IT assets. UEM (Unified Endpoint Management) is a broader concept that unifies the management of all endpoints (desktops, mobile, IoT) under a single set of policies, often with a stronger focus on user profiles and security compliance.

See how automated rules, alerts, and dashboards maintain high-quality, reliable data.

File server management software centralizes file storage, sharing, permissions, and oversight so teams can securely access ...

A secure way for users to access internal networks, apps, and files from anywhere using authenticated, ...