Content Lifecycle Management
Manage Your Content Lifecycle
Monitor Your Mission-Critical Data
Easily review the status of all of your company’s content from a single, comprehensive dashboard.
Reduce Cyberattack Surface
Delete or archive obsolete content that could be leveraged by cyberattackers or malicious insiders.
Streamline Compliance
Comply with global and regional data retention regulations that impact your business.
Content Lifecycle Management Capabilities
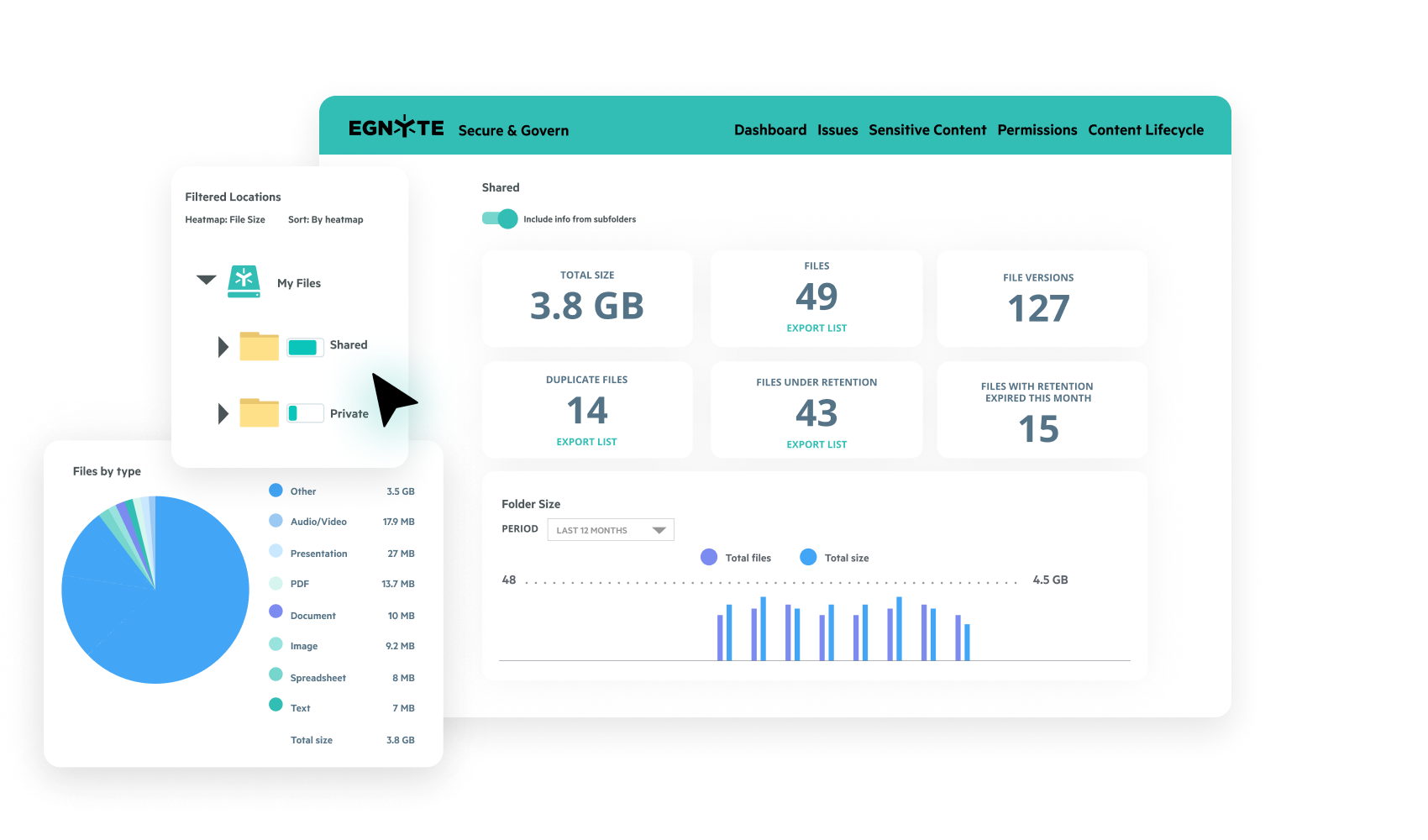
Content Lifecycle Dashboard
- See where your mission-critical content resides, across all data repositories
- Easily identify duplicate files, and files under data retention
- Take immediate action to archive or delete redundant, obsolete, or trivial (ROT) content
- Align dashboard review with security compliance management requirements pertinent to your organization
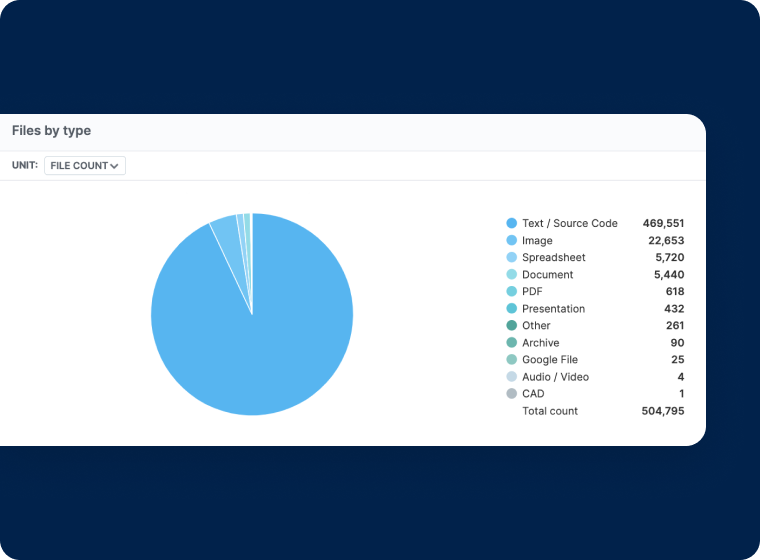
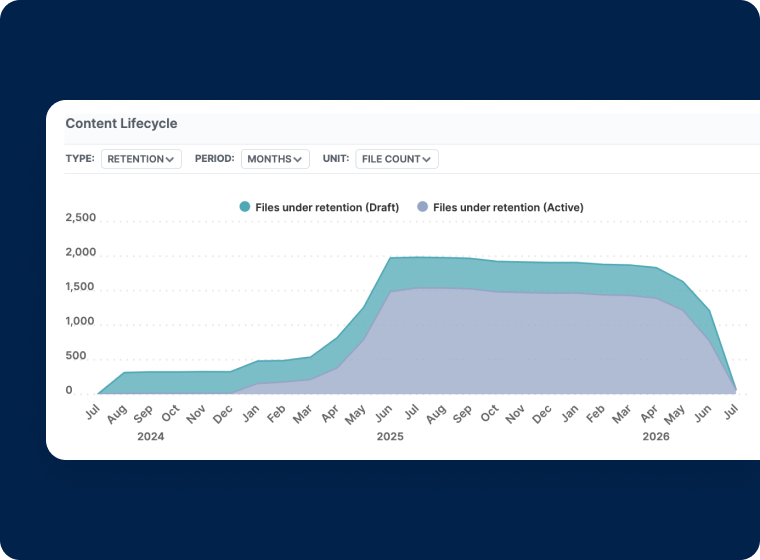
Centralized Administration
- Get a comprehensive view of stored files, by file type
- Increase productivity by giving users access to the most current data available
- Centralize retention policies organizationally to prevent accidental data deletion
- Reduce storage costs for data that isn’t actively being accessed
Compliant Data Retention and Archival
- Create retention and archival policies aligned with data lifecycle program management guidelines
- Select from numerous standard lifecycle policies or create customized policies of your own
- Leverage Egnyte's Artificial Intelligence (Al) expertise to identify content subject to important policies
- Apply and enforce policies in conjunction with regulatory and business requirements
Hear From Our Customers
See Egnyte Content Lifecycle Management in Action
Improve users’ productivity and manage mission-critical content more effectively by:
- Enabling secure collaboration
- Creating workflows for key project participants
- Proactively deleting or archiving data that is no longer needed by the business
You Might Also be Interested In
FAQs
Content Lifecycle Management (CLM) refers to the process of managing digital content from creation and users’ initial collaboration to classification, retention, and secure disposal (for example, the content’s archival or deletion). CLM ensures that data remains compliant, accessible, and organized throughout its lifecycle. Effective CLM reduces storage costs, mitigates data sprawl, and strengthens governance and data security posture, making it essential for regulated industries and enterprises that handle high volumes of unstructured data.
To explore how organizations are addressing data sprawl and improving governance, watch the on-demand webinar: Governance in a Data Sprawl World.
Organizations often struggle with data sprawl across their content storage repositories, lack of visibility into aging or redundant files, inconsistent retention policies, and non-compliance with regulatory standards. Without a centralized CLM strategy, businesses are susceptible to security breaches, excessive storage costs, and audit failures. Automating CLM helps address these challenges by enforcing retention rules, improving data classification, and promoting policy-based governance.
CLM enforces consistent retention, archival, and deletion policies across all repositories, ensuring that sensitive data is properly governed. It helps organizations meet compliance mandates such as HIPAA, the California Privacy Rights Act (CPRA), GDPR, and/or FINRA by providing auditable controls, access logs, and automated file disposition. This reduces the risk of non-compliance penalties and enhances enterprise-wide data governance.
By automating content classification and archiving obsolete files, CLM streamlines access to the most current and relevant information. Teams spend less time searching for documents and more time collaborating on active files. CLM also ensures content is appropriately shared and retained, which enhances productivity while reducing the risk of working on outdated or unauthorized versions.
When a retention policy expires, the system can automatically archive, delete, or flag files for review based on the configured rules. This reduces manual intervention, lowers storage costs, and ensures that content does not remain longer than necessary, helping meet compliance requirements and minimize legal exposure.
Only authorized administrators can create, edit, or delete retention policies within a CLM system. This ensures that governance rules are enforced consistently and prevents end users from bypassing compliance protocols. Role-based access controls and audit logs help maintain policy integrity and transparency.
Egnyte supports full document lifecycle management with metadata, version control, retention policies, and automated disposition. Organizations can track documents from creation through archival and secure deletion via a convenient content lifecycle dashboard, ensuring content is managed in accordance with business and regulatory requirements.
Egnyte provides centralized governance and retention management across departments. IT and compliance teams can define and enforce retention policies consistently for HR, legal, finance, and operational content, reducing manual effort and improving regulatory compliance.
Egnyte enables document reviews and approvals through integrated workflows and collaboration tools. Teams can route files for review, track approval status, and maintain audit trails—all within Egnyte—streamlining processes and improving accountability. In addition, Egnyte’s co-editing and version control capabilities permit users to detect specific changes to documents over time.
Egnyte supports automated folder templates and policy-driven structure enforcement. Organizations can create standardized folder hierarchies for projects, clients, or departments, ensuring consistency, easier navigation, and improved compliance across teams.
Egnyte provides content intelligence and reporting capabilities that help identify stale, duplicate, or low-value content. These insights help organizations clean up storage, reduce risk, and improve overall content hygiene. Data insights are provided via a convenient content lifecycle dashboard, so that immediate action can be taken to delete, archive, or reach out to business units for additional details.
Egnyte automates compliance with tools for classification, sensitive data detection, and policy enforcement for standards such as CPRA, GDPR, CMMC, and HIPAA. These capabilities help organizations continuously monitor content, apply appropriate controls, and reduce the need for manual compliance reviews.
Egnyte provides secure storage, version control, access restrictions, and audit logging for contracts and sensitive agreements. This ensures that only authorized users can access critical documents and that all access and changes are fully tracked. Review and analysis of complex legal agreements is simplified by Egnyte’s AI-powered Contract Analyst.
Egnyte can index and surface content across cloud, on-prem, and hybrid environments, providing a unified, searchable interface. This allows users to quickly find content regardless of where it is stored, improving productivity and reducing duplication.
Egnyte supports secure archiving with encryption, retention enforcement, and policy-based access control. This ensures sensitive files are protected long-term while meeting regulatory and legal retention requirements like CPRA, GDPR, CMMC and HIPAA.
Egnyte provides detailed sharing logs, link expiration, watermarking, and external user controls. Organizations can see who accessed what and when, revoke access instantly, and maintain full auditability for external collaboration. Links sent to external users can be further safeguarded with password protection and limitations on co-editing by external users.