Ransomware Detection and Recovery
Rapidly detect and respond to ransomware attacks and protect your sensitive data with behavioral and signature-based detection—all in a single platform
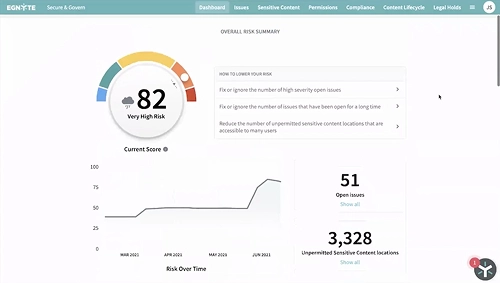
All-in-One Solution to Detect and Mitigate Ransomware Risk
Reduce Content Exposure
Centralize visibility and access to sensitive data
- Two-factor authentication
- Geo-IP controls
- Minimize data exposure
- Data-driven access
Protect Against Variants
Detect both new and known ransomware signatures
- Unusual behavior detection
- Presence of ransom-notes
- Zero-day monitoring
- Ransomware signatures
Cut Back on Downtime Costs
Bounce back faster with less disruption
- Breach reporting
- Data classification (contracts and regulations)
- Metadata descriptions
The Egnyte Solution
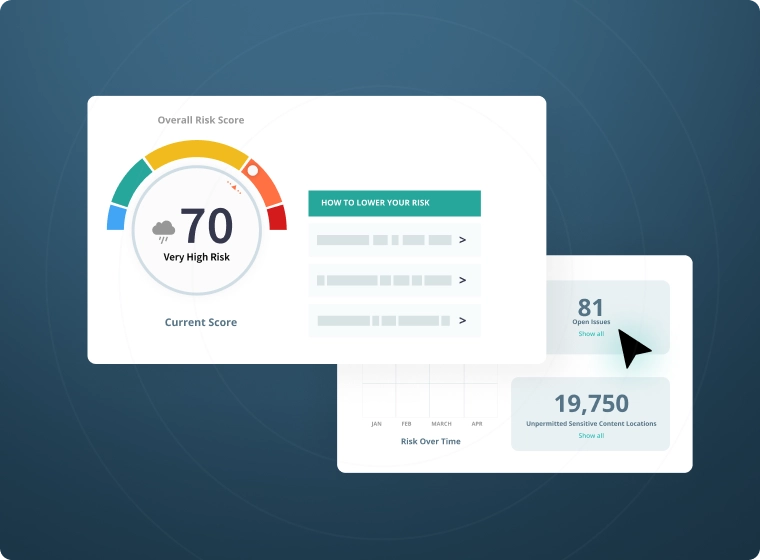
Prevention Against Ransomware
- Lock down file access with granular, least-privilege permission controls, and two-factor authentication
- Apply out-of-the-box classification patterns to locate and classify files containing sensitive information
- Minimize traffic flows to sensitive data in advance, with only a few clicks

Detect Ransomware
- Utilize signature-based detection to scan your folders and flag files and patterns associated with ransomware
- Identify previously unknown ransomware variants with behavioral analytics
- Access the latest, cloud-based release without worrying about maintenance
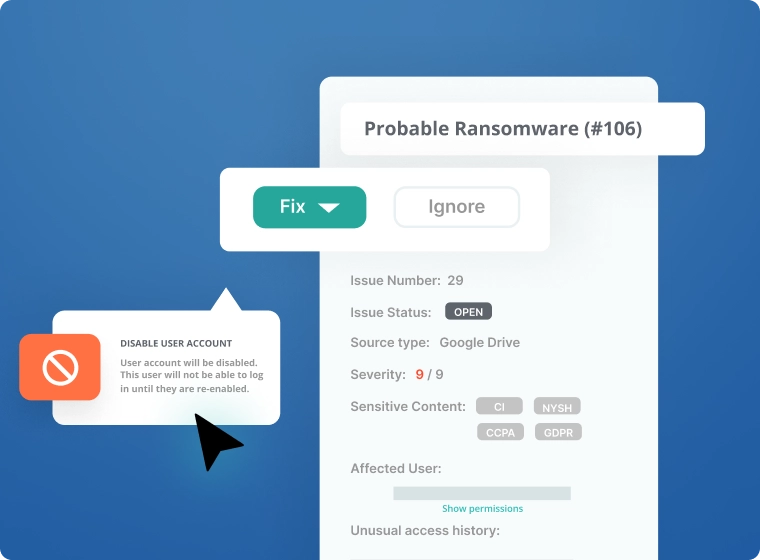
Recover from Ransomware
- Speed investigation and simplify recovery with an audit trail of compromised users, files, and data subjects/sensitive data
- Recover smarter -- roll back access judiciously across your entire organization
- Comply with GDPR notification requirements with built-in breach reporting
An Expert Team Behind You
- Count on the latest advances in data protection and ransomware detection with a dedicated team of experts
- Leverage proprietary machine learning models designed and trained specifically to fight ransomware
- Rely on fast-acting partners that ensure a smooth recovery
Faster Time to Value
Powered by Egnyte AI
Learn more about Egnyte’s content intelligence engine, which includes:
- GPT-powered models allowing users to "converse" with private data sets in natural language
- Predictive models for content classification, entity extraction and unusual behavior detection
- Connected workflows such as automated labeling, security issue remediation, and human-driven review/approval tasks
The Power of Many Tools In One Turnkey Platform
Egnyte has a complete solution for ransomware prevention, detection and recovery, but the real difference is that it’s pre-integrated with dozens of other tools your business needs for content collaboration, data privacy, compliance, insider threat prevention, and more.
See Full Pricing BreakdownBusiness
- Secure file sharing
- Ransomware protection
- Integrations with leading apps
- Real-time co-editing on web, desktop and mobile
Ultimate
Everything in Business, Including:
- AI Copilot, AI Search, and AI Workflow
- PDF markup and e-signature
- Sensitive data classification
- Snapshot & recovery (90-days)

