Federal Information Security Modernization Act (FISMA) Compliance
Every federal mission depends on the ability to transform data into action. From national programs to public-facing services, decision-making is only as strong as the systems that govern the information behind it. When data is secured, structured, and aligned across environments, it becomes a strategic asset, driving clarity, coordination, and measurable impact.
This makes the question “What is FISMA?” more relevant than ever. Between 2020 and 2023, just 60% of federal agencies were found to have effective information security programs, according to the Council of Inspectors General on Integrity and Efficiency. FISMA provides the framework to close that gap, offering federal leaders a clear path to strengthen cyber resilience, manage risk, and safeguard the integrity of the nation’s most sensitive digital infrastructure.
To meet the growing demand for secure, compliant, and mission-ready data environments, federal leaders must fully understand the scope and significance of FISMA. This article breaks down what FISMA is, explores the core FISMA compliance requirements, and outlines actionable FISMA compliance solutions that help agencies modernize cybersecurity programs and protect high-value information assets.
Let’s jump in and learn:
Why FISMA Exists and Its Purpose
What does FISMA stand for? The Federal Information Security Modernization Act sets the foundation for cybersecurity governance across federal agencies. FISMA sets standardized frameworks to protect government information systems from evolving threats. It also promotes consistent security practices across agencies and their contractors.
The federal information security management act FISMA modernized outdated compliance approaches by shifting focus from basic documentation to measurable effectiveness. This transformation addresses escalating cyber threats that target government infrastructure, ensuring agencies maintain robust defenses while supporting mission-critical operations.
Who Must Comply with FISMA?
FISMA compliance oversight operates through coordinated federal authorities that ensure consistent implementation across government agencies:
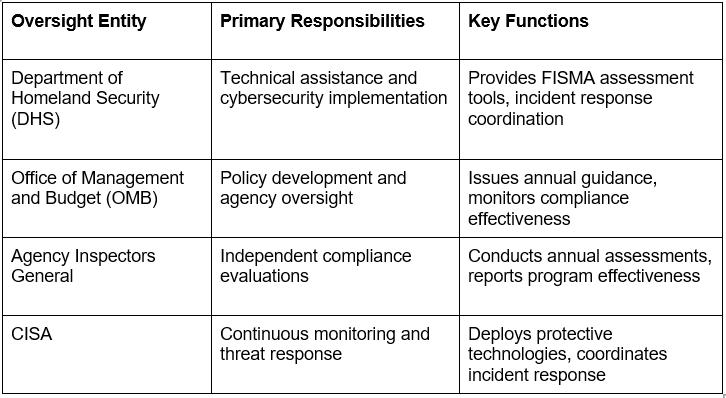
FISMA Compliance Requirements
Federal agencies are expected to meet rigorous security standards to protect sensitive systems and data. That’s where clarity around what is FISMA compliance becomes essential. Aligned with the NIST Cybersecurity Framework, it follows a structured and risk-based approach to securing federal information systems.
At its core, FISMA focuses on five key functions:
- Identify – Manage system and data risks
- Protect – Implement safeguards
- Detect – Monitor for threats
- Respond – Contain and mitigate incidents
- Recover – Restore operations efficiently
This foundation also aligns with complementary frameworks such as the Cybersecurity Maturity Model Certification (CMMC) and FedRAMP Compliance, further strengthening an agency’s overall federal security posture.
To meet FISMA compliance requirements, agencies must apply security controls across critical domains such as:
- Risk management
- Configuration management
- Identity and access management
- Incident response
- Contingency planning
Each domain is assessed for maturity to ensure continuous improvement and program effectiveness.
How to Become FISMA Compliant?
FISMA assessment processes require a systematic evaluation of security controls using established maturity models. Organizations must achieve Level 4 (managed and measurable) effectiveness across core security functions to demonstrate compliance adequacy.
Implementation begins with a comprehensive inventory of information systems to identify all assets that require protection. Risk assessments then categorize each system based on potential impact, which helps determine the level of security controls needed:
- Low: Limited adverse effect on operations or assets
- Moderate: Serious adverse effect on operations or assets
- High: Severe or catastrophic adverse effect on operations or assets
Continuous monitoring is followed to maintain compliance and quickly address emerging threats.
Best Practices for FISMA Compliance
Leading organizations implement FISMA certification through proven methodologies that integrate security into operational workflows. Executive leadership commitment provides the necessary resources and backing for effective program implementation. It also reinforces organizational support at every level.
Key practices include automated security control monitoring, regular vulnerability assessments, incident response planning, and continuous staff training.Data governance platforms provide integrated capabilities that streamline compliance documentation while maintaining real-time visibility into security posture.
Can Security Ratings Support Compliance?
Security ratings provide objective measures of organizational cybersecurity posture that complement FISMA assessment requirements. These metrics enable continuous monitoring of security effectiveness while identifying areas requiring additional attention or investment.
Modern security rating platforms integrate with existing FISMA compliance processes to provide real-time visibility into control effectiveness. Secure cloud storage solutions leverage these capabilities to maintain continuous compliance while supporting operational requirements.
Penalties for FISMA Compliance Violations
Noncompliance with FISMA can lead to significant consequences, including funding restrictions, operational setbacks, and increased legal exposure. Agencies that fail to maintain effective security programs may face increased oversight from Congress and inspectors general. They also risk public scrutiny, which can damage their reputation and affect their ability to fulfill their mission.
Security failures can expose organizations to cyber threats that put sensitive data, critical operations, and public trust at risk. The Federal Information Security Management Act reinforces accountability by requiring agencies to prioritize information security and allocate the resources needed to maintain a strong and compliant posture.
Conclusion
FISMA compliance is a strategic opportunity to build a resilient, secure foundation for mission-critical operations. Agencies that approach compliance proactively gain more than audit readiness. They strengthen governance, accelerate decision-making, and foster long-term trust across stakeholders.
Egnyte helps federal organizations turn compliance into a catalyst for efficiency and agility. With a unified platform for secure file sharing, content lifecycle management, and policy-based governance, Egnyte simplifies the complexity of federal data security requirements.
Powered by Egnyte Intelligence, agencies can automatically classify sensitive information, enforce retention policies, detect risks in real time, and generate audit-ready reports, all while maintaining control across hybrid and cloud environments.
For federal teams seeking to modernize their security posture without disrupting operations, Egnyte delivers the clarity, control, and confidence needed to meet FISMA standards and scale securely.
Frequently Ask Questions
Q. What Are the 3 Levels of FISMA?
FISMA categorizes systems into Low, Moderate, and High impact levels based on potential damage from security breaches, determining appropriate security control requirements.
Q. What Happens If FISMA Is Violated?
FISMA violations result in funding restrictions, operational limitations, congressional oversight, inspector general investigations, and potential legal liability for security failures.
Q. Is FISMA the Same as FedRAMP?
FISMA establishes overall federal cybersecurity requirements, while FedRAMP provides specific cloud service authorization processes that comply with FISMA standards.
Q. Whose Rights Are Covered by FISMA?
FISMA protects all individuals whose personal information is processed by federal agencies or contractors, ensuring the privacy and security of government-held data.
Q. How Can You Monitor FISMA Compliance?
FISMA compliance monitoring requires continuous assessment of security controls, regular inspector general evaluations, automated security monitoring, and comprehensive reporting through established frameworks
Additional Resources

GDPR Compliance, in a Click
Learn more about GDPR for cloud in order to secure personally identifiable information (PII) of EU ...
What Is the NIST Cybersecurity Framework?
Understand the NIST Cybersecurity Framework’s core functions and maturity levels, and learn how it helps ...

What Is Data Compliance
Learn how data compliance ensures organizations follow global regulations like GDPR, HIPAA, and CCPA to protect ...