FedRAMP Compliance Requirements & Process for Cloud Service Providers
For federal agencies and their partners, data is a mission-critical asset. From national infrastructure to public-facing services, secure and uninterrupted access to sensitive information underpins every function. However, in today’s evolving threat landscape, traditional security methods no longer suffice.
To meet rising expectations around risk mitigation and regulatory compliance, organizations must adopt a unified, standards-based cybersecurity approach. FedRAMP compliance provides a structured framework to validate security posture and ensure readiness to serve the federal market.
This blog explores how aligning with FedRAMP requirements not only strengthens security controls but also positions your organization to operate with greater confidence, credibility, and access to high-value federal opportunities.
Let’s jump in and learn:
- What is FedRAMP?
- FedRAMP Program Basics
- FedRAMP Objectives
- The FedRAMP Process
- Who Must Comply with FedRAMP?
- FedRAMP Authorization Best Practices
- What Are FedRAMP Compliance Requirements?
- FedRAMP Compliance Checklist
- What Are the Categories of FedRAMP Compliance?
- Cross-Agency Security Expands Opportunities
- Get Started with Egnyte
- Frequently Asked Questions
What is FedRAMP?
The Federal Risk and Authorization Management Program (FedRAMP) is a standardized cybersecurity framework for cloud service providers working with U.S. federal agencies. It streamlines cloud adoption by replacing redundant agency-specific assessments with a unified authorization process, enabling faster, secure deployment across government entities.
FedRAMP Program Basics
FedRAMP mandates rigorous security assessments, continuous monitoring, and standardized authorization processes for cloud service providers.
Key elements of the program include:
- Standardized Security Requirements: Based on NIST 800-53 controls, ensuring a consistent approach across agencies.
- Three Authorization Paths: Joint Authorization Board (JAB), Agency Authorization, and CSP Supplied Package.
- Baseline Impact Levels: Low, Moderate, and High—defining the sensitivity of data handled.
- Continuous Monitoring: Ongoing oversight to maintain compliance and mitigate emerging threats.
- Marketplace Listing: Only FedRAMP authorized cloud service providers appear on the FedRAMP Marketplace, signaling trustworthiness and readiness for federal use.
FedRAMP Objectives
- Standardize cloud security assessments across federal agencies.
- Reduce duplication of effort through a “do once, use many times” authorization approach.
- Ensure consistent implementation of NIST-based security controls.
- Promote secure cloud adoption in the federal government.
- Streamline procurement and authorization for cloud service providers.
- Enhance risk management and visibility across cloud environments.
- Support continuous monitoring and real-time threat mitigation.
- Build trust and transparency between federal agencies and cloud providers.
- Lower costs and timelines associated with compliance and cloud integration.
- Drive innovation securely by enabling the use of commercial cloud services.
The FedRAMP Process
Step 1: Choose Authorization Path
Select either the Agency ATO route or the Joint Authorization Board (JAB) P-ATO path, depending on your federal market strategy and sponsor engagement.
Step 2: Prepare Security Documentation
Create the System Security Plan (SSP) and other required documentation that outlines your cloud system’s architecture, controls, and risk posture, mapped to NIST 800-53 controls.
Step 3: Engage a 3PAO
Partner with a FedRAMP-accredited Third Party Assessment Organization (3PAO) to conduct an independent security assessment.
Step 4: Complete the Security Assessment
The 3PAO performs penetration testing, vulnerability scans, and control testing to produce a Security Assessment Report (SAR).
Step 5: Remediate Risks
Address any findings or gaps identified in the SAR. Document your remediation actions and update the security package accordingly.
Step 6: Submit for Authorization
Submit the complete security package (SSP, SAR, POA&M) to the authorizing body (Agency or JAB) for review and approval.
Step 7: Receive ATO or P-ATO
If approved, you receive an Agency Authority to Operate (ATO) or Provisional ATO (P-ATO) from the JAB, allowing you to serve federal customers.
Step 8: Continuous Monitoring
Begin ongoing compliance activities, including monthly vulnerability scans, annual security assessments, incident reporting, and system updates to maintain your authorization status.
Who Must Comply with FedRAMP?
FedRAMP compliance is mandatory for all Cloud Service Providers that handle federal data on behalf of U.S. government agencies. This includes:
- CSPs offering IaaS, PaaS, or SaaS solutions to any federal agency
- Third-party vendors partnering with government contractors who use cloud services
- Federal agencies themselves, which must ensure any cloud product they use is FedRAMP authorized
FedRAMP authorized cloud service providers who must maintain ongoing compliance through continuous monitoring and periodic reassessment
FedRAMP Authorization Best Practices
Successful organizations approach FedRAMP authorization with strategic planning and early coordination. This reduces delays and strengthens long-term compliance readiness.
- Consult 3PAOs early to identify potential gaps.
- Align internal stakeholders across key functions.
- Maintain clear and complete documentation.
- Enable continuous monitoring for control validation.
What Are FedRAMP Compliance Requirements?
To achieve and maintain FedRAMP authorization, CSPs must complete the following:
Compile Initial FedRAMP Documentation
Prepare mandatory documents like the System Security Plan (SSP), which outlines how your system meets FedRAMP controls. Use FedRAMP templates for consistency.
Conduct a FIPS 199 Assessment
Categorize your information system’s security impact level (Low, Moderate, or High) under FIPS 199 guidelines, which determines the scope of security controls required.
Perform a 3PAO Readiness Assessment
Engage a Third-Party Assessment Organization (3PAO) to review your system for compliance gaps. This ensures you're prepared for the full authorization process.
Develop a POA&M (Plan of Action & Milestones)
Address any identified vulnerabilities or control deficiencies. Outline remediation steps and timelines in the POA&M document.
Follow the Authorization Process
Choose either the Agency-sponsored or JAB (Joint Authorization Board) path. Undergo formal security assessment, submit results, and obtain a FedRAMP Authorization to Operate.
Maintain Continuous Monitoring
After authorization, submit monthly security reports, scan results, and incident reports. Continuous monitoring ensures ongoing compliance and risk mitigation.
Modern document management systems streamline compliance documentation by automating version control, access tracking, and audit trails required for FedRAMP authorization.
FedRAMP Compliance Checklist
- Conduct Gap Analysis: Evaluate current security posture against FedRAMP requirements
- Document SOPs: Establish standard operating procedures for all security controls
- Configure IAM Controls: Implement identity and access management systems
- Engage 3PAO: Select qualified assessment organization early in the process
- Establish Patch Management: Deploy automated systems for security updates
- Schedule Re-Assessments: Plan ongoing compliance validation activities
- Train Personnel: Ensure staff understand FedRAMP requirements and procedures
Automated data governance platforms accelerate compliance preparation by automatically classifying data, tracking access patterns, and generating audit reports required for FedRAMP authorization.
What Are the Categories of FedRAMP Compliance?
FedRAMP outlines three impact levels based on the potential impact of a security breach. Each level maps to specific controls and assessment procedures aligned with the sensitivity of the data and systems involved.
Impact Levels and Requirements:
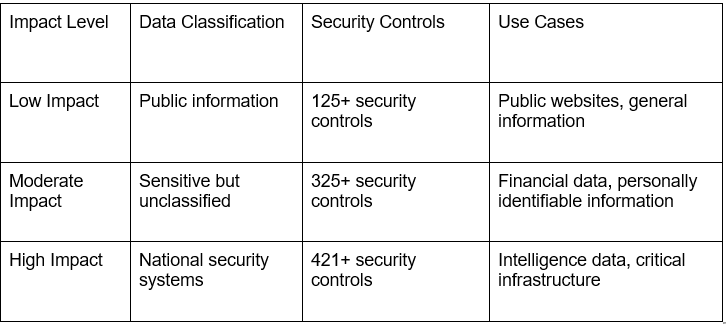
Organizations processing highly sensitive data should consider FedRAMP High authorization requirements, which provide the most comprehensive security protections available under the framework.
Cross-Agency Security Expands Opportunities
Achieving FedRAMP compliance is a strategic enabler. Once authorized, cloud service providers can serve multiple government agencies without redundant approvals, significantly expanding their market reach and contract eligibility. This cross-agency trust model streamlines procurement, speeds up deployment timelines, and builds a foundation for long-term federal partnerships.
Egnyte accelerates this journey with its secure, compliant-ready content platform. With granular permission controls, robust encryption, audit-ready reporting, and data residency support, Egnyte helps providers align with FedRAMP controls from day one.
For federal customers, Egnyte delivers an intuitive, integrated environment to manage unstructured content securely, whether it's sensitive documents, project data, or collaborative files.
Get Started with Egnyte
FedRAMP compliance solutions do more than help you meet requirements. They show you're equipped to lead in high-trust federal environments. It's not just about eligibility. It's about demonstrating you're built for the highest level of operational readiness.
Turn FedRAMP compliance into a strategic advantage with Egnyte’s unified governance platform. Proven across federal environments, our solutions simplify authorization and automate ongoing compliance for long-term efficiency and security.
Frequently Asked Questions
Q. What Does It Mean to Be FedRAMP Compliant?
FedRAMP compliance means your cloud service has undergone rigorous security assessment and received government authorization to process federal data.
Q. What Are the Different Paths to Achieve FedRAMP Compliance?
Organizations can pursue Agency Authorization through specific federal departments or Joint Authorization Board approval for government-wide use.
Q. Is FedRAMP Only for the Government?
While designed for federal agencies, FedRAMP compliance enables access to lucrative government contracts and demonstrates security leadership.
Q. What is the Process to Get FedRAMP Certified?
The certification process includes readiness assessment, documentation preparation, third-party security evaluation, and authorization decision requiring 12-24 months.
Q. Which Cloud Providers Are FedRAMP Certified?
Major FedRAMP authorized cloud service providers include Amazon Web Services, Microsoft Azure, Google Cloud Platform, and specialized solutions.
Additional Resources

Understanding FedRAMP Controls
Explore the core NIST-aligned security requirements that form the foundation of federal cloud trust.

Egnyte & FedRAMP Compliance
FedRAMP provides a unified security standard that accelerates cloud adoption and ensures consistent protection across government ...

Egnyte Achieves FedRAMP Moderate Equivalency
Egnyte has earned FedRAMP Moderate Equivalency and joined the FedRAMP Marketplace, enabling secure collaboration for DoD ...