Compliance Audit Guide
Organizations today face mounting pressure to comply with a complex web of regulations and industry standards. A regulatory compliance audit helps organizations expose vulnerabilities, verify adherence to standards, and avoid legal or financial setbacks. It’s a practical way to check whether processes, policies, and documentation are doing what they’re supposed to, that is, keeping the business secure, efficient, and on the right side of the law. In certain cases, you may find a compliance audit referred to as a “compliance assessment,” particularly when cybersecurity experts refer to the Cybersecurity Maturity Model Certification (CMMC) for U.S, Department of Defense contractors and subcontractors.
Let’s jump in and learn:
- What Is a Compliance Audit?
- What Is the Purpose of a Compliance Audit?
- Types of Compliance Audits
- Benefits of Compliance Audit
- Compliance Audit Criteria
- Participants in a Compliance Audit
- How to Conduct a Compliance Audit
- Compliance Audit Challenges
- Compliance Audit Management and System
- How Egnyte Supports Compliance
- Egnyte’s Audit Capabilities in Action
- Conclusion
- Frequently Asked Questions
What Is a Compliance Audit?
A compliance audit process is a methodical evaluation of how well your organization follows internal policies, laws, and industry standards. It examines systems, controls, procedures, and documentation to verify compliance with relevant regulations. When asked, “What is compliance audit?” the definition covers reviews of legal documents, security controls, and processes to identify gaps and confirm adherence
What Is the Purpose of a Compliance Audit?
A legal compliance audit has clear goals:
- Assess if policies and systems meet requirements
- Flag deficiencies and recommend corrective steps
- Verify remediation efforts after issues arise
- Ensure consistency across ongoing operations
Understanding the purpose of a compliance audit helps organizations see it as more than a checkbox. It becomes a tool for operational improvement and ongoing compliance.
Types of Compliance Audits
Organizations face different types of compliance audits based on their needs and risk:
- Internal IT compliance audit: Conducted by in-house teams to test controls and align systems with regulations.
- External compliance audit: Managed by independent auditors or agencies like the Environmental Protection Agency (EPA), Food and Drug Administration (FDA), or PCI Security Standards Council (PCI SSC).
- Governance and compliance audit: Focuses on corporate policies, board oversight, ethical culture, and risk frameworks.
- Specialized audits and assessments: These include CMMC, ISO 27001, GxP, GDPR-CCPA compliance, and golden thread safety compliance, each tailored to specific regulatory and operational requirements.
Benefits of Compliance Audit
Here are the key benefits of compliance audit:
- Protects against penalties and legal problems
- Reduces risk from data breaches or faulty processes
- Builds trust with stakeholders
- Fuels continuous improvement
- Supports transparent reporting and documentation
- Prevents operational disruptions
- Maintains a good brand reputation
- Provides a safe working environment
Compliance Audit Criteria
Compliance auditing standards use clear benchmarks to measure compliance against laws such as the General Data Protection Regulation (GDPR) or industry norms like ISO 27001. Auditors look for controls that are measurable, well‑defined, objective, and reliable.
They verify that your organization:
- Understands current regulations
- Maintains effective controls
- Takes corrective action when issues arise
The criteria for a compliance auditor include having the ability to:
- Identify audit and reporting requirements
- Obtain sufficient evidence to make a determination of compliance
- Perform procedures to ensure that organizations address gaps
- Report on whether the entity complies with the level specified in the compliance audit requirements
Participants in a Compliance Audit
Compliance auditing participants include three key parties:
- Auditor: Collects evidence, assesses compliance, and delivers a report.
- Responsible party: The regulator or internal team setting the audit scope.
- Intended users: Stakeholders such as executives or boards who rely on the audit findings.
Internal IT compliance audit teams include subject matter experts and compliance staff. External compliance audit teams include certification bodies, legal advisors, or specialized auditors.
Third parties are sometimes brought in to support the project for internal and external compliance audits. This is done for a variety of reasons, including:
- Lack of internal resources to manage the compliance audit
- Need for specific expertise that’s required for an assessment
- Desire for independent observations or oversight
How to Conduct a Compliance Audit
These compliance audit documentation steps show how to conduct a compliance audit effectively. They turn compliance into a live and dynamic system, rather than a static exercise.
Here is a clear view of the compliance audit procedures in actionable steps:
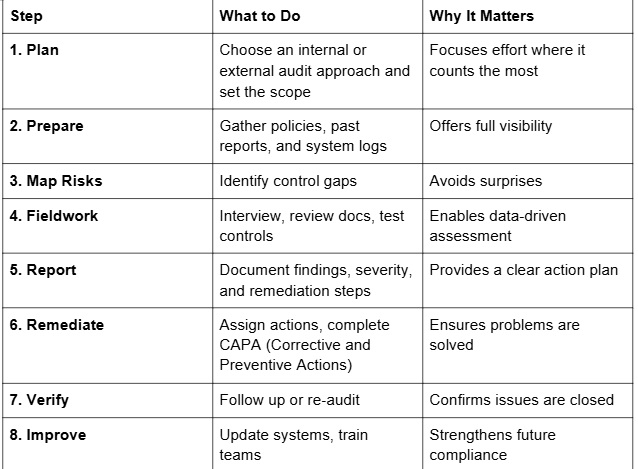
Compliance Audit Challenges
Common hurdles in compliance audit include:
Confusion Between One‑Time and Continuous Audits
Some compliance audits (such as PCI-DSS) take place once a year when an auditor reviews controls and documentation. Other compliance audits (such as SSAE 16/18, Sarbanes-Oxley) require that controls operate consistently over a period of time and that the organization maintain proof of that.
Poor Follow‑Up on Corrective Actions
Corrective and Preventive Action (CAPA) is key to a successful compliance audit. Creating and executing policies for remediation ensures that issues are rectified, and any compliance audit follow-up by external auditors will go smoothly. A lack of follow-through on remediation can result in a loss of trust not just with the auditor, but with employees and customers.
Blame Culture Instead of Lesson Learning
Rather than focusing on blame, it's more effective to understand why an issue happened and how to prevent it from happening again. Often, a flagged issue points to broader weaknesses, and resolving it can reveal and fix related problems elsewhere.
Inconsistent Documentation
Records and documentation should be consistent and clearly show dates, times, and details that prove compliance requirements were met. Most of the red flags raised by auditors are related to missing or inconsistent documentation.
Weak Leadership Support
Strong support from management is essential for building a culture of compliance across the organization. Since audits touch many departments, everyone should understand their role and why compliance matters. Leadership plays a key role by providing the resources and involvement needed to meet audit requirements.
Poor Audit Governance
Before a compliance audit, it’s important to review risks and spot any gaps. This helps avoid surprises and gives the organization time to fix issues or prepare a plan to address them. Skipping this step reflects poor audit governance and can lead to missed problems or unprepared teams.
Risk Oversight Gaps
Someone with no conflicts of interest should oversee and/or make decisions related to compliance and compliance audits. This ensures that ongoing oversight and evaluations are unbiased and identify all compliance audit risks or gaps.
Compliance Audit Management and System
Effective compliance audit management relies on a solid compliance audit system. Such a system captures evidence, tracks issues, schedules re‑audits, and streamlines documentation. It supports real-time visibility and automates reminders for review deadlines.
Regular audits keep you ahead of changing rules. They signal that you treat compliance as central, not optional.
How Egnyte Supports Compliance
Egnyte offers tailored solutions to help with commonplace compliance challenges:
- CMMC compliance: Supports DoD contractors through full file governance
- GxP compliance: Enables life sciences firms to meet FDA and EMA standards
- Golden thread safety compliance: Helps manage building safety documents
- ISO 27001 compliance: Meets global information security standards
- GDPR ‑ CPRA compliance: Enables global data privacy protection
Each solution provides secure collaboration tools, visibility into controls, and automated reporting. They help integrate compliance into daily workflows.
Egnyte’s Audit Capabilities in Action

Challenge
Tilt Creative + Production needed stronger control over file access to meet the security demands of high-profile clients like Audi and Walmart. Their old system used a fixed permissions structure that couldn’t support detailed access levels. This made it hard to meet compliance standards like ISO-27001 and TISAX. The complexity of moving large volumes of data to a new platform was also a concern.
Solution
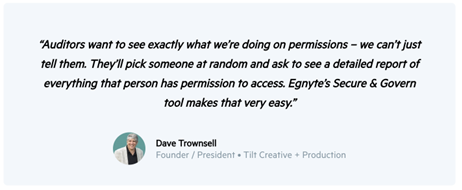
Tilt switched to Egnyte with help from its project management team. The migration was easier than expected thanks to Egnyte’s user-friendly tools. Once in place, Egnyte gave them better control over who could access what content. They could easily manage permissions at every level and run reports for audits using Egnyte’s Secure & Govern feature.
Results
- Easier internal and external audits
- Improved compliance with ISO and TISAX standards
- Faster system performance with fewer disruptions
- Fewer support requests from users
- Smoother quality control using file activity alerts
- Better client satisfaction and stronger data oversight
Conclusion
A compliance audit is far more than a review. It is a strategic tool for ensuring operational strength, legal compliance, and governance integrity. By embedding effective processes, real‑time systems, and strong leadership, compliance becomes a competitive advantage.
It also builds confidence among partners, customers, and regulators. Regular audits help organizations stay ahead of new rules and identify areas for improvement that might otherwise go unnoticed. Over time, this creates a more resilient, transparent, and well-managed business with strong data security and compliance.
Frequently Asked Questions
What are compliance audit guidelines?
Compliance audit guidelines are the rules or steps that help auditors review whether an organization meets required laws and standards. They cover how to check systems, documents, and controls. These guidelines also define how to report findings and what to do if there are gaps. They ensure the audit is fair, consistent, and thorough.
What is a compliance audit checklist?
A compliance audit checklist is a list of items to review before and during an audit. It helps teams prepare by highlighting key areas like policies, records, and security controls. The checklist ensures nothing important is missed and gives auditors a clear view of how the organization meets its compliance goals.
How to prepare for a compliance audit?
Start by reviewing policies, controls, and past audit results. Make sure all records are organized and up to date. Identify any gaps or risks and fix them before the audit. Train key staff on what to expect. Good preparation helps the audit go smoothly and shows that compliance is taken seriously.
What is ISO compliance audit?
An ISO compliance audit checks if an organization follows ISO standards, like ISO 27001 for information security. It involves reviewing processes, controls, and documentation to make sure they meet the required framework. These audits can be internal or performed by outside experts to earn or maintain certification.
Additional Resources

Get Ready for Your CMMC Assessment
A clear path to achieving and maintaining CMMC compliance so your organization can continue winning DoD ...
CMMC Assessment: Key Requirements Explained
A quick overview of what a CMMC assessment is, who needs it, and how organizations working ...

CMMC 2.0 Compliance
Egnyte supports DoD contractors in meeting CMMC 2.0 cybersecurity requirements to protect sensitive defense data.