What is Data Encryption? Definition and Best Practices
Data Encryption Definition
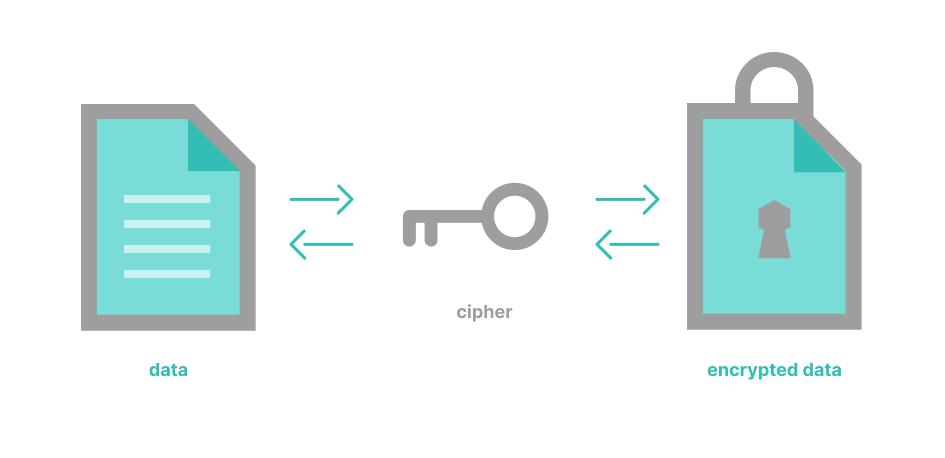
Data encryption is a process that encodes content (e.g., messages, files) to protect its confidentiality and integrity. Algorithms are used to scramble or encrypt data. To unscramble or decrypt the information, a unique key is required. Encrypted data is rendered virtually unusable without the key.

Data encryption is used to protect a wide range of content, including that included in communications, databases, IoT devices, and applications. To adhere to internal, government, and industry regulations, data encryption is used to secure sensitive information.
With data encryption, information can be protected at rest, in transit, and in use.
- Data at rest—stored data that is not being accessed (e.g., files stored on file servers, records in databases, documents on flash drives, information on hard disks)
- Data in transit—data that is being shared over a network (e.g., email, website forms, collaboration tools, instant messaging)
- Data in use—data is opened by one or more applications
Four Common Data Encryption Terms
- Ciphers or encryption algorithms—the formulas used to encode and decode messages
- Ciphertext—data in its encrypted, unreadable form
- Cryptography—the science of encrypting and decrypting information
- Plaintext—data in its original form before being encrypted
Types of Data Encryption
There are two main kinds of data encryption—asymmetric encryption and symmetric encryption.
- 1. Asymmetric data encryption, also called public-key encryption or public-key cryptography, encrypts and decrypts the data using two cryptographic asymmetric keys—a public key and a private key. The public or shared key encrypts the data. The private key, which is used for decryption, must be protected. Examples of asymmetric encryption are RSA, named for the engineers who designed it, and Public Key Infrastructure (PKI).
- 2. Symmetric data encryption uses only one secret key, which is used to encrypt and decrypt data. It requires the sender to exchange the encryption key with the recipient in order to decrypt the data. Data Encryption Standards (DES), Triple DES, Advanced Encryption Standard (AES), and TwoFish are examples of asymmetric encryption.
Data Encryption Techniques
The most common data encryption techniques are summarized below. These standards were developed to address different security requirements.
Advanced Encryption Standard (AES)
AES is an easy-to-use symmetric data encryption algorithm. In 2002, it was adopted by the United States government as its encryption standard. It is commonly used in consumer technologies worldwide.
AES is a symmetric cipher that is based on the Rijndael block cipher. Users can set the key length to 128, 192, or 246-bits, and AES supports block lengths of 128-bits for block cipher encryption. AES is considered resistant to all attacks except for those that utilize brute force.
Blowfish
An outdated data encryption algorithm, Blowfish remains effective. It is a symmetric cipher that divides messages into blocks of 64 and then encrypts them one at a time. Blowfish was succeeded by TwoFish.
Data Encryption Standard (DES)
The Data Encryption Standard (DES) was launched by the US government in 1977 and used as its standard until 2002, when it was replaced by more powerful data encryption options. Pioneering in its time, DES is now considered a low-level standard that is basically obsolete.
Elliptic curve cryptography (ECC)
ECC refers to systems in which only the two users communicating can decrypt the conversation; each of them possesses keys. Because no third-party has knowledge of the data being communicated or stored, surveillance or manipulation is impossible.
Powerful and fast data encryption, ECC is part of the SSL/TLS protocol that encrypts communication between websites and their visitors. Although it generates shorter key lengths for speed, it still meets high-security standards. (e.g., a 3,072-bit RSA key and a 256-bit ECC key provide the same level of security.)
Public key infrastructure (PKI)
PKI enables the use of technologies like digital signatures and encryption. It provides the hardware, software, policies, processes, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates, and public keys. PKI is at the heart of e-commerce and serves as the basis for Internet of Things (IoT) security.
RSA
RSA is named for the three computer scientists who invented it—Rivest, Shamir, and Adleman. It was created in 1977 to encrypt data in transit.
A public-key data encryption cryptosystem, RSA is among the most widely utilized asymmetric cryptography standard that uses public and private keys. RSA’s public key is based on three values—two very large prime numbers and one other number that combine to secure the data in transit.
Triple DES (3DES or TDES)
Called 3DES because it runs DES three times. This three-step process increases the DES key size of 56-bits to 168-bits, making it much more difficult to decrypt.
3DES is a symmetric-key block cipher that uses symmetric encryption to encrypt segments of data using a fixed block size. Even with its three layers of encryption, 3DES is no longer considered reliably secure by modern standards.
TwoFish
TwoFish can be used in many software and hardware applications, because it is free and unpatented; it also ranks among the fastest encryption algorithms. It generates keys up to 256-bits in length.
Purpose of Data Encryption
- Defend against brute-force and cyberattacks, including malware and ransomware.
- Ensure that only intended parties can access the data.
- Establish that a website’s owner owns the private key listed in the website’s TLS certificate, meaning the website is legitimate and not a malicious spoof.
- Help organizations to meet internal, government, and industry compliance requirements (e.g., CCPA, HIPAA, PCI-DSS, and GDPR).
- Prevent data breaches by protecting data at rest, data in transit, and data in use.
- Reduce liability if sensitive data is inadvertently exposed or hacked.
- Secure messages by:
- Keeping content confidential
- Verifying origin
- Protecting from tampering
- Secures data on computers, removable storage media, and mobile devices.
Process of Data Encryption
To start the encryption process, a determination has to be made as to which system (or cipher) to use (see Data Encryption Techniques above). Those algorithms are used to encrypt and decrypt data.
The strength of the encryption method is determined by the key that is generated rather than by the system. The cipher provides the engine for encryption, while the key provides directions about how data should be encoded.
Data Encryption Challenges
Despite its efficacy as a security tool, encryption does have vulnerabilities, including:
- Computer programs can break some encryption algorithms and gain access to encrypted content.
- Encrypted data in transit can be viewed if devices are infected by malware that eavesdrops or sniffs data as it moves across networks.
- Encrypted data at rest can potentially be compromised by malware or by a cybercriminal who has gained access to systems.
Additional data encryption challenges include issues with key management systems, such as:
- Overhead required to support these systems.
- Performance issues.
- Difficulty integrating with cloud-based systems.
- Issues with accessing encrypted data.
It is worth noting that data encryption can also be weaponized. Ransomware uses data encryption to lock down files until a ransom is paid.
Data Encryption Solutions
There are many data encryption solutions for general use as well as highly specialized applications. Commonly used data encryption solutions include:
- Blockchain—for cryptocurrency
- HTTPS encryption—for websites
Secure / multipurpose Internet Mail Extensions or S/MIME—for email - Pervasive encryption—for database encryption
- RSA—for data at rest
- Transport Layer Security or TLS—for data in motion
- VPNs—for data in motion
Data Encryption is Everywhere
From individual users and small companies to government agencies and large corporations, data encryption is used to protect information that is being stored, used, or sent, from financial data to health records. Without data encryption, many key industries, such as e-commerce, online banking, and telemedicine, would create intolerable vulnerabilities as they conduct business and provide their company’s services.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 3rd October, 2021