Bring Your Own Device (BYOD)
BYO, bring your own, has expanded from snacks and libations at social events to technology—becoming BYOD, or bring your own device. The term BYOD has several synonyms, including BYOT (bring your own technology), BYOPC (bring your own personal computer), BYOP (bring your own phone), and BYOT (bring your own tablet). BYO-X basically means that workers use their personal equipment rather than devices that are supplied by their employers.
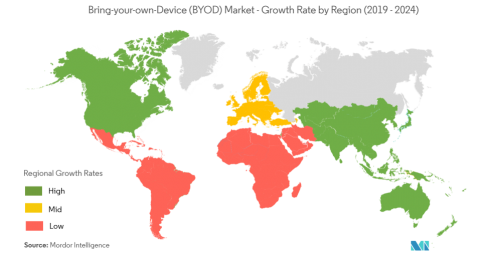
BYOD adoption varies by region and organizational type. The US and European countries, especially Ireland, Germany, Austria, and Switzerland, are currently trending in the middle of BYOD adoption. The Middle East and Africa have relatively low adoption. Asian countries and Australia have the highest rates of adoption.
What is BYOD?
Bring your own device (BYOD) means allowing employees to use personal devices for work. This includes granting access to networks, work-related systems, and data.
Included under the BYOD umbrella are mostly portable devices such as smartphones, personal computers, and tablets. The growing BYOD trend among employers is driven by a need to make workplaces more flexible and accessible by allowing employees to use devices of their choice for work.
Types of BYOD
BYOD comes in several forms, and each presents security risks that must be considered.
Bring Your Own Device (BYOD)
With BYOD, employees are responsible for their devices. IT can install agents or applications to manage security, but the device is under the management of the employee. This model gives employees control over the selection, support, maintenance, and, to some degree, security of the device.
Company-Owned, Business Only (COBO)
In the COBO model, devices are issued to employees and are meant to be used only for work. These devices can be configured with security and managed by IT security teams.
Corporate Owned, Personally Enabled (COPE)
A hybrid model, COPE, gives employees the freedom to customize and use personal apps on a device issued and managed by the employer. That model allows IT to control security protocols.
Choose Your Own Device (CYOD)
CYOD allows employees to select from approved devices and purchase from a pre-approved vendor. Typically, IT has these devices configured with security protocols and business applications.
Personally Owned, Company Enabled (POCE)
In the POCE scenario, IT sections off parts of the device for corporate use. For instance, network access would be separated from personal components of the device.
Why BYOD is Important
BYOD is important because it is becoming a default for many employees—regardless of whether their company has a policy or not. For better or worse, BYOD is here to stay.
Organizations that understand why BYOD is important are better able to manage risks associated with personal devices that are being used for work.
Another reason that BYOD is important is that employees who are allowed to use their own devices are more productive. Being able to use a device that they are comfortable with increases overall job satisfaction and has been shown to improve morale and productivity.
Advantages of BYOD
Productivity Gains with BYOD
When employees are allowed to use their own devices, productivity increases. This is attributed to their personal device being something they are more comfortable using, which makes them happier and allows them to do more, faster.
BYOD Access to Cloud
With the pervasiveness of cloud solutions, employees are able to access applications and data from anywhere. When BYOD is in place, employees have the freedom to work from any location. This results in an overall increase in employee engagement.
More Frequent Updates to BYOD Systems
Because users largely maintain their own devices, they can install updates more frequently as they are prompted to do so by the devices. This means updates are done without having to wait for or take the time of IT.
Cost Savings from BYOD
With BYOD, there is less need to invest in equipment for employees. And the expense is transferred from CAPEX to OPEX.
Disadvantages of BYOD
Data Leaks Related to BYOD
Because employees do not maintain security protocols at the same level as a workplace device, BYOD increases the chance for data leaks. One of the weakest devices, in terms of security, is also increasing in popularity—the wearable device.
Increased IT Workload for IT to Maintain BYOD Security
IT must expand security to include BYOD. New policies need to be continually created, implemented, and deployed to keep up with the changing BYOD landscape.
BYOD Data Exposure
With data accessible on multiple personal devices, BYOD dramatically increases the potential for data loss. BYOD provides more exfiltration vectors that can be used to remove data when employees leave a company.
Compatibility Across Internal Systems and BYOD Platforms
Having many different devices trying to use multiple internal systems can cause IT headaches. With each device comes new requirements that IT is expected to support.
BYOD Privacy Concerns
As IT tries to secure BYOD, it bumps up against privacy. More security inevitably leads to less privacy. When personal devices are used, the content can be left exposed to IT.
Legal Issues Related to BYOD
BYOD is problematic from a legal standpoint regarding sensitive or proprietary information. When stored on a personal device, sensitive data has a higher chance of unauthorized access.
An additional legal risk relates to hourly employees and the potential for overtime pay when they are expected to access data and applications outside of their scheduled work times.
BYOD Security
Concerns related to BYOD security include:
- Unintended exposure through other apps on devices (e.g., social media, malicious apps)
- Device loss or theft
- Vulnerability to hackers
- Inconsistent network security due to differences in devices’ operating systems
- Business and personal use on BYOD devices can create risk due to visits to non-secure sites or connections to unsecured wireless networks
BYOD security best practices include:
- Using encryption to protect sensitive information
- Requiring strong passwords for corporate applications and data stores
- Separating personal and business data
- Establishing a plan for lost or stolen devices
- Educating employees about device maintenance and IT Security
Developing a BYOD Policy
A well-designed BYOD policy is a critical part of closing the gap in personal device security. Developing a BYOD policy takes dedicated time and effort but is important for all organizations. Areas to consider are outlined here and provide an overview of proven approaches:
- Create long-term BYOD policies.
BYOD policies should be open enough to accommodate changes in devices and platforms. They should also be flexible enough to address the requirements to support internal and external users (e.g., contractors, partners). - Engage representatives of all constituents in BYOD policy development processes.
It is important to include representatives from all user groups in the process of developing a BYOD policy. This means everyone from senior managers to HR and legal to sales. Each will have their own unique needs and perspectives. Incorporating their points of view into the process will help create a policy that will work well and lead to high adoption rates. - Adjust to meet the needs of the organization.
Follow best practices, but when something is not a fit, adjust it to align with existing workflows. This will also facilitate adoption and minimize resistance. - Determine what devices can be used.
Create a list of permissible devices. Doing so in the early stages of BYOD policy development will help shape rules that fit with what devices are in use. However, try to be as inclusive as possible, and be willing to include new technology as it becomes available. - Create policies with bi-directional benefits.
BYOD policies should have benefits for the organization and its employees. Mutual benefit makes it easier to gain employee buy-in. - Develop rules and processes to separate personal and business use.
When developing BYOD policy, put clear rules in place that separate work and personal use. Work applications should be used only for work, and personal applications should only be used outside of work. This is especially important for email and calendars. - Ban storage of sensitive information on BYOD systems.
BYOD policies should unequivocally state that under no circumstances should sensitive information be stored on BYOD systems.
Implementing a BYOD Policy
The implementation phase is where security details come into play. Consider these security guidelines when implementing a BYOD policy:
- Establish minimum required security controls for devices that include data encryption and access controls.
- Determine where data created and edited on BYOD systems will be stored, and what can be stored on the device.
- Set timeout controls to lock devices after a certain period of inactivity.
- Define criteria for security applications to protect mobile devices—what they are (or should be in the future) and who decides which will be used.
- Make clear when IT is permitted to remotely wipe organizational data from a BYOD system, such as if the device is lost, an employee is terminated, or there is a security breach.
Part of implementation is establishing and enforcing acceptable use policies for BYOD. This includes defining what access is allowed and restricted from a BYOD system, such as:
- Applications
- Datastores
- Websites
- Calendars
- Contacts
- Content
Guidelines for BYOD implementation commonly include direction on how to handle the following:
- Effective communication
- Device protocols
- Restrictions on authorized use
- IT access and privacy
- Company stipend and financial reimbursement procedures
- Safety when using devices (e.g., texting and driving, or openly providing geographic location data)
- Lost, stolen, damaged, or compromised equipment
- Termination of employment
- Violations of BYOD policy
Take a Balanced Approach to BYOD
BYOD can feel unwieldy and generate security concerns, but it is here to stay. And for all the angst that it causes IT, BYOD does bring tangible benefits to organizations. Taking time to develop a BYOD policy that balances security, privacy, and access will go a long way to support employee morale and productivity, while maintaining a strong security posture.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 23rd December, 2021