What is User Behavior Analytics?
User behavior analytics (UBA) are software programs that track, collect, and assess user data and activities using algorithm-driven monitoring systems to detect abnormal behavior. This could be from a malicious insider or malware.

The two main functions of user behavior analytics are to determine what normal behavior is, and then to identify anomalies. User behavior analytics tools establish a baseline for an organization’s and individuals’ normal activities.
User behavior analytics utilizes the logs of normal behavior to create a set of big data. It couples this data with pre-determined rulesets on specific behavior, then runs machine learning algorithms that can learn which activities should be considered permissible.
User behavior analytics also leverages this data and these algorithms to detect instances of malware, a data breach, or other potential risks. Using this information, user behavior analytics can trace issues back to the unusual behavior in near real-time.
The user behavior analytics system logs user activity details, such as when a user requests access to files, when those files were accessed, how often, and what actions were performed with the data in the files. It also logs when users launch applications, which networks they access, and what activities they conduct on those networks.
User behavior analytics can even track which emails are sent and read. Basically, user behavior analytics logs all usage activity, both authorized and unauthorized.
User behavior analytics systems provide cybersecurity teams with actionable insights by monitoring activities on a large scale. This enables malware detection or other possible security threats, such as data exfiltration, malicious insiders, and compromised endpoints.
Why UBA Is Important
The following review of key features explains why UBA is important.
Data Theft Reduction
User behavior analytics helps reduce data theft by detecting when users download information they are not authorized to access and by triggering an alert.
Insider Threat Identification
Insider threats are detected when employees’ usage patterns deviate from their norm. Because user behavior analytics establish baselines for individuals’ customary usage, it is able to quickly detect when something is awry, such as a user accessing the data for a longer than normal time period, or at unusual times of the day. This triggers an alert, which allows an action to be taken to minimize potential damage.
Enhanced Security Monitoring
User behavior analytics can be used to monitor organizations’ three key domains—their network, users, and assets—and establish a baseline for normal behavior. For instance, it can track the frequency of certain traffic, processes, or applications run by users. Statistical anomalies trigger alerts and a subsequent investigation. Learnings from the assessment are utilized by the user behavior analytics system to enhance their monitoring efforts.
Data Correlation Across Systems
Monitoring and analyzing events in a silo provides only limited context and inhibits incident correlation. User behavior analytics provides a holistic view and probes the aggregated data for unusual activity that could be a sign of malware or other malicious actions.
In the event of an incident, user behavior analytics can provide details that help with remediation. For example, it can identify the compromised devices, the point of entry, the amount of time spent on the network, what was done, and what data (if any) was exfiltrated.
Automation Instead of IT Staff Spurs Better Results
User behavior analytics automates and optimizes advanced analytics, leveraging supervised and unsupervised machine learning. With supervised machine learning, the analytics are coded to identify specific data types, use that as a baseline, and detect usual behavior from that data.
User behavior analytics are also capable of unsupervised machine learning. With unsupervised machine learning, algorithms infer patterns from a dataset without reference to known or labeled outcomes. User behavior analytics can automatically be trained to differentiate unusual from expected activity, which reduces false positives.
User Behavior Analytics and Malware
Although user behavior analytics is commonly associated with malicious insiders and exfiltration, it is a powerful tool for combating malware, both from internal and external threats. Because malware attacks continuously evolve, having user behavior analytics as part of the security posture is critical.
User behavior analytics can detect almost any anomaly, even if it has never been seen. In addition, user behavior analytics helps with malware defense and remediation by:
- Detecting threats based on real-time user actions
- Improving investigation efficiency
- Prioritizing security
Malware Attack Vectors that Can Trigger User Behavior Analytics Alerts
Typical malware attack vectors include:
- Connected smart devices
- Drive-by download attacks
- Email attachments
- Free and pirated software
- Infected external devices
- Internet-of-Things (IoT) devices
- Malicious advertising, also known as malvertising
- Malicious URLs
- Operating system and application vulnerabilities
- Other malware delivery methods
- Remote desktop tools
- Self-propagating viruses
- Social engineering ploys
Malware Attacks Caught with User Behavior Analytics
User behavior analytics helps mitigate the damage from malware attacks. It is able to identify the point of origin for malware that originates from a variety of sources.
Regardless of the source, user behavior analytics is a technology uniquely qualified to ferret out malicious software, where it originated, and where it goes. In addition, because user behavior analytics monitors every user and compares behavior to what should be normal, it is able to identify anomalies caused by malware and issue an alert quickly.
Malware can enter a system in a number of ways. The attackers’ objectives vary, but malware can be used to achieve various malicious purposes, including to launch ransomware attacks, access sensitive information, destroy systems, gain persistent access from which future attacks can be launched, and steal money.
Suspicious Malware-Generated Activity Detected by User Behavior Analytics
User behavior analytics can detect suspicious patterns that may indicate malware activity. Malware-generated activity that triggers user behavior analytics includes the following:
- Privileged account abuse with inappropriate use of access permissions
- Privilege escalation followed by changing users’ access credentials
- Data exfiltration, most commonly theft of sensitive data
- Anomalous behavior, including:
- Accessing external domains
- Remotely accessing high-privileged assets
- Engaging in unusual login duration, time of day, or geographic location
- Credentials compromised where accounts are taken over
- Hosts, such as a server or mobile devices, compromised
A few indications of malware activity that also trigger user behavior analytics alerts include:
- Unusual timing of activity (e.g., accessing a sensitive database at 3:00 am local time)
- Abnormal sequences of actions
- Increased downloads or data movement
The following are other system-specific malware activities that can trigger user behavior analytics to raise a red flag, alerting that there could be an attack in progress.
- Malicious code is injected into applications already installed on users’ systems (e.g., Microsoft Word, Adobe PDF Reader, a web browser, JavaScript) to take advantage of known vulnerabilities and then execute malware.
- Disguised as a legitimate file, malware loads into memory and executes a script that searches for and exfiltrates sensitive data.
- Native system tools, such as Microsoft Windows Management Instrumentation (WMI) and Microsoft PowerShell scripting languages, are often targeted to execute malware scripts that are run remotely.
How User Behavior Analytics Stops Malware
User behavior analytics can help identify users’ accounts that have been compromised by malware. Data about users’ accounts that have been infected with malware can be combined to provide a comprehensive view into the scope of the attack.
This aggregated view enables more accurate user analytics related to the malware. Alerts can be enhanced with data about the malware, including the source user or the destination user’s organization or individual account.
Types of User Behavior Analytics
Unlike many other security technologies, user behavior analytics rarely operate in isolation. Depending on what technology it is coupled with, there can be various types of user behavior analytics. Technology commonly used in conjunction with user behavior analytics includes:
- Cloud access security brokers
- Data leakage prevention
- Endpoint detection and response
- Endpoint security
- Identity access management
- Identity governance
- Intrusion detection systems (IDS)
- Security intelligence platforms, also known as threat intelligence platforms
- Security Information and Event Management (SIEM) solutions
Using user behavior analytics with complementary technologies makes it possible to increase visibility, anomaly detection, and actionable alerts.
As a standalone system, user behavior analytics reviews users’ data, IP address, applications, and network activities. After setting a baseline, it analyzes, detects, prioritizes, and responds to unusual user activity.
Added to SIEM, user behavior analytics expands monitoring to include security information and event management. In addition, it analyzes users’ behavior within the identity, access governance, and privileged access management in its workflow.
As part of a Security Orchestration, Automation and Response (SOAR) system, user behavior analytics helps to expedite remediation. The SOAR can be configured to act directly on high-risk alerts generated by user behavior analytics.
How UBA Works
To understand how UBA works, start at the heart of it—data. User behavior analytics systems collect various types of data about known users, including:
- Access privileges and permissions
- Accounts
- Geographical location
- Roles and titles
- Timestamps on normal activities
- Usual activities (e.g., logging into an application, opening shared files, downloading files, sharing data through communication tools)
This data is aggregated by mining past and current activity, such as resources used, duration of sessions, connectivity, and peer group activity. The system also automatically updates when changes are made to the data, such as a new title from a promotion, an additional or changed geographic location, and changes to permissions. User behavior analytics uses this as a baseline against which it compares anomalous behavior.
User behavior analytics does not send alerts for all anomalies. If unusual behavior is detected, it is evaluated to assess if it is a false-positive, as well as its potential impact, and scored accordingly. This allows security teams to prioritize the alerts that user behavior analytics generates.
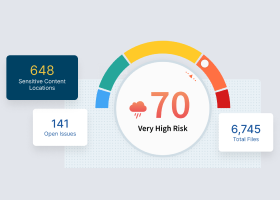
How UBA Scoring Works The risk to the system posed by a particular activity is determined using this formula: Risk = Likelihood x Impact Likelihood refers to the probability that the flagged user behavior is an anomaly. This value is calculated with behavior modeling algorithms. Impact is based on the classification and criticality of the data that was accessed, along with what restrictions have been imposed on the data. Once scored, anomalous behaviors are associated with the user. Risks based on the user’s profile and other factors are calculated and can be added to the system-based risk score. Users’ risk calculations typically include additional factors, including asset classification, access permissions, potential vulnerability of the data, user policies, and data policies. Any increase in these factors will increase the risk score of that particular user. The risk model can be tuned using customized weighting values for all the factors in these calculations. |
Using unsupervised machine learning algorithms, user behavior analytics reduces false positives and provides more accurate, actionable threat intelligence. User behavior analytics’ machine learning algorithms can not only identify and eliminate false positives, they also deliver actionable risk intelligence, update norms based on changes in behavior, and provide predictions based on the information they’ve collected.
In addition, the user behavior analytics system can be configured to automatically restrict or increase the difficulty of users’ authentication, with suspicious behavior based on the score assigned to the alert.
Following are scenarios that illustrate how UBA works.
- A user who normally does not download files is saving gigabytes of data to an external hard drive. In this case, the user behavior analytics would generate a high-risk alert about a possible exfiltration attempt.
- A user accesses a server that they have never accessed. This would cause the user behavior analytics to issue an alert for a potential endpoint attack or compromise.
- The user behavior analytics can detect any attempt to infect a system with malware or malicious activity by insiders and trigger an alert.
An IT team alone cannot accomplish the work done by user behavior analytics. User behavior analytics goes far beyond human capacity, using artificial intelligence technologies such as machine learning to monitor vast instances of user behavior with increasing accuracy. In addition, the models can be continuously trained and tuned over time.
From Marketing to Monitoring Multiplier
Behavior analysis systems were originally used to help marketing teams analyze and predict customers’ buying patterns. The core technology was co-opted by security engineers and turned into user behavior analytics tools with advanced profiling and exception monitoring capabilities to detect unusual or malicious behavior.
Focused on the who, what, when, and where of user activity, user behavior analytics tools have become a must-have in security portfolios—especially since they can be used in conjunction with other security solutions to multiply their value. In the end, user behavior analytics can generate a context-aware petabyte-scale dataset that can be leveraged with its advanced analytics to detect and deter cyberthreats.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 18th December, 2021