Controlled Unclassified Information (CUI)
Sensitive data flows across emails, shared drives, and cloud folders are prevalent in critical business operations. The information might not be “top secret,” but if it gets into the wrong hands, the consequences can be serious: Operational disruption, reputational damage, or even national security concerns.
For organizations working with the U.S. Department of Defense, a large chunk of this sensitive data falls under a category known as Controlled Unclassified Information (CUI). This includes all information that isn’t classified, from engineering drawings and technical manuals to supply chain details.
To make sure CUI is properly protected for DoD contractors and subcontractors, the DoD introduced CMMC 2.0, a framework that helps contractors prove they can secure sensitive data throughout their supply chain. Meeting the framework’s requirements involves building trust with federal agencies like the DoD and showing that your organization takes data protection seriously.
Designed for hybrid and cloud-first environments, Egnyte’s Content Security & Governance platform and our EgnyteGov U.S. Federal Agency solutions gives you the tools to answer those questions confidently.
Let’s jump in and learn:
- What is CUI specified?
- Understanding CUI Classification: Basic vs Specified
- Where to Find the Full List?
- CUI Compliance and System Requirements
- Protecting Managed Unclassified Information
- How Microsoft 365 Supports Controlled Unclassified Information (CUI) Protection
- Best Practices for CUI Management
- CUI Labeling and Managing
- Conclusion
- Frequently Asked Questions
What is CUI specified?
CUI is sensitive information that is not classified but must be safeguarded. However, neither Executive Order 13526 nor the Atomic Energy Act classify this information. The CUI program aims to standardize the handling, marking, and dissemination of sensitive but unclassified information across federal agencies.
Understanding CUI Classification: Basic vs Specified
Understanding CUI Classification: Basic vs Specified
Within the CUI framework, there are two key categories every executive leader should understand: CUI Basic and CUI Specified.
CUI Basic
CUI Basic refers to information that requires protection but does not have additional handling requirements beyond the standard controls outlined in the federal CUI regulations (32 CFR Part 2002). This category is governed by a uniform set of rules that apply across all agencies.
For example, internal reports, draft policy documents, or general personally identifiable information may fall under CUI Basic. While such information isn’t highly sensitive, mishandling it could still result in reputational or operational risk. Standard access control processes, proper marking, and responsible dissemination are required.
CUI Specified
CUI Specified includes information that is subject to additional safeguarding or dissemination controls, as mandated by specific laws, regulations, or government-wide policies. In other words, there are defined legal authorities that dictate exactly how this data must be handled.
Examples include export-controlled data (like, under ITAR), health records protected by HIPAA, or federal tax information under IRS codes. This category often requires stricter controls, such as limited user access, enhanced encryption, or storage in controlled environments, based on the governing policy.
Key Distinction for Decision-Makers
The primary difference lies in compliance complexity:
- CUI Basic follows a standard baseline of protection.
- CUI Specified demands additional compliance tied to specific legal or regulatory frameworks.
As an executive, it’s important to ensure that your teams understand these distinctions, implement the correct controls, and remain compliant with the relevant authorities, especially during audits, data-sharing agreements, or cross-agency collaboration.
Types of Controlled Unclassified Information
Every single category of CUI is crucial for different reasons. So, mishandling any of them could expose one to legal, financial, or security risk. Here’s a look at some of the most common types of CUI:
Privacy Information
Any personal details that are protected under privacy laws like the Privacy Act of 1974 or the Health Insurance Portability and Accountability Act (HIPAA) are included. Examples are included below:
- One’s full name, Social Security number, and date of birth
- Medical records, Insurance information
- Passport numbers or driver’s license data
- Employment history or personnel files
Safeguarding personal information is crucial for maintaining privacy, complying with legal requirements, and preventing serious consequences, such as identity theft, financial fraud, or reputational damage. It not only harms individuals but can also result in significant penalties and loss of trust for organizations.
Financial Information
Applicable laws, such as the Gramm-Leach-bliley Act (GLBA) and various federal financial regulations, typically protect financial information. Below are the common data types included under the category:
- Bank account numbers
- Credit card information
- Tax returns and audit data
- Financial aid applications
- Payroll information
Protecting financial information is critical, as it’s often a prime target for fraud, identity theft, and cyberattacks. Exposure can lead to severe monetary losses, legal consequences, and damaged reputations for individuals and organizations alike. Strong security measures ensure this sensitive data remains confidential, accurate, and available only to authorized parties.
Proprietary Business Information
Sometimes referred to as “trade secrets” or “confidential business information,” this type of CUI protects competitive business data. This is especially relevant when private companies work on government contracts. Examples include:
- Product designs or schematics
- Manufacturing processes
- Marketing strategies
- Contract proposals
- Internal reports or analysis
Protecting proprietary business information is critical to maintaining a competitive edge, preserving innovation, and fulfilling contractual obligations. A leak, whether intentional or accidental, can result in financial loss, erode client trust, and compromise a company's reputation in government partnerships. Strong data governance enables this sensitive content to remain secure throughout its lifecycle.
Law Enforcement Information
Data related to criminal investigations, police operations, or any other law enforcement-related activities is listed in this category. The information types are listed as follows:
- Witness statements or evidence logs
- Surveillance reports
- Arrest records, especially in ongoing cases
- Sensitive communications between crucial agencies
Protecting law enforcement information is crucial to maintaining the integrity of investigations, safeguarding the identities of individuals involved, and ensuring public safety. Unauthorized access or disclosure can hinder active cases, compromise operational tactics, and put the lives of officers, witnesses, and victims at risk.
Critical Infrastructure Information
This category includes CUI deals with the systems and services vital to the country’s functioning, like energy, water, transportation, and communications. The Critical Infrastructure Information Act protects data related to:
- Utility systems and layouts
- Security plans for transportation hubs
- Emergency response strategies
- Technical data about dams, pipelines, and power grids
Protecting critical infrastructure information is essential to national security and public safety. If compromised, this data could be exploited to disable power grids, disrupt water supply, or paralyze transportation systems.
Export Control Information
This category includes information related to defense items or technology subject to export controls. The International Traffic in Arms Regulations and Export Administration Regulations help protect data, including:
- Military equipment specifications
- Satellite or space technology
- Software with encryption functions
- Research data related to weapons or defense
Information governed by export control laws is highly sensitive and as it has direct implications for national defense and global stability. Unauthorized access or leaks can result in severe legal penalties, compromise military operations, and put lives in danger.
Legal Information
This refers to sensitive legal documents that are not public but are still important to protect. Such legal information includes:
- Pre-decisional legal opinions or drafts
- Attorney-client communications
- Court filings under seal
- Settlement negotiations
Legal information often contains confidential advice, ongoing case details, or sensitive negotiations. Unauthorized access or premature disclosure can compromise legal strategy, breach client privilege, and impact judicial outcomes or policy decisions.
Procurement and Acquisition Information
This type of CUI includes details about government purchasing, bids, and contracts. The following types of data are protected to ensure a fair and competitive process.
- Bid proposals
- Pricing estimates
- Contract negotiations
- Technical evaluation data
Protecting procurement and acquisition data is critical to maintaining the integrity of government contracting. Exposure of bids, pricing, or evaluation details can lead to unfair advantages, legal disputes, and compromised vendor trust.
Intelligence and Defense-Related Information (Unclassified)
This defense-related unclassified data includes military strategies, logistics plans, or partner agreements. Some examples are included below:
- Deployment schedules
- Non-classified military research
- Joint exercises with allies
- Defense supply chain data
Exposure of deployment plans, research data, or supply chain details could compromise operational readiness and national security. Protecting this data helps prevent adversaries from exploiting gaps in coordination, logistics, or partnerships.
Immigration and Border Protection Data
This information applies to individuals entering or leaving the country, visa applications, and border patrol strategies. It preserves data integrity for:
- Visa interview transcripts
- Immigration case files
- Travel surveillance reports
Protecting immigration and border protection data is critical to national security and individual privacy. Mishandling this information can lead to identity theft, legal disputes, or compromised enforcement strategies. Following the confidentiality protocols upholds compliance with regulatory standards and safeguards the integrity of immigration processes and border operations.
Where to Find the Full List?
Where to Find the Full List?
A CUI Registry from the U.S government is listed with all the recognized CUI categories and the applicable laws and regulations, as well. The National Archives and Records Administration shares this online database. One can visit the registry to explore every CUI category, its definition, and the handling instructions.
Visit the CUI Registry website here: https://www.archives.gov/cui
CUI Compliance and System Requirements
Companies that deal with Federal regulations that CUI must abide by include
- The CUI program is established by Executive Order 13556.
- 32 CFR Part 2002 offers comprehensive instructions for managing CUI
Organizations must also follow the guidance below regarding safeguarding CUI:
- NIST SP 800-171: The standard focuses on strengthening cybersecurity across the government supply chain by defining clear security requirements for contractors handling CUI. It is essential to national security and mission success.
- NIST SP 800-53: It helps manage risk and protect operations, assets, and individuals from cyber threats. The framework supports compliance with federal mandates while promoting a flexible, outcome-based security approach.
- FIPS Publication 199: It requires agencies to evaluate and label systems as low, moderate, or high impact, helping prioritize security efforts. These categories guide the selection of appropriate safeguards across federal IT environments
- FIPS Publication 200: The purpose is to set mandatory, minimum security requirements for all federal information and systems, excluding national security systems. It specifies 17 key control areas such as access control, incident response, and contingency planning.
Protecting Managed Unclassified Information
Strong security measures must be implemented to protect Controlled Unclassified Information (CUI). The suggested practices are given below:
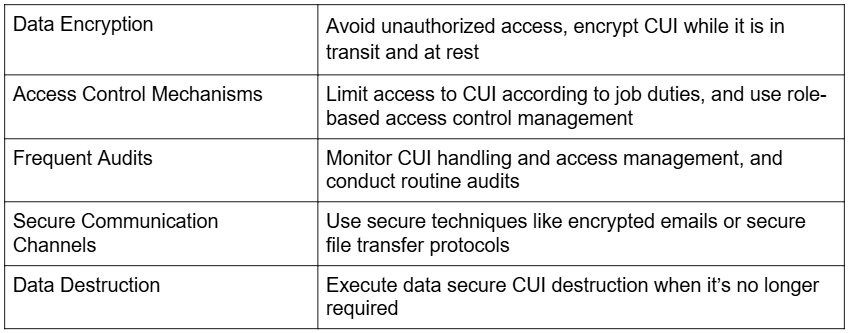
How Microsoft 365 Supports Controlled Unclassified Information (CUI) Protection
Microsoft 365 offers a suite of integrated security and compliance tools designed to help organizations identify, protect, and manage Controlled Unclassified Information (CUI) across their digital environments. These solutions integrate with Egnyte’s Governance solutions.
Here's how each feature contributes to a more secure and compliant workflow:
Data Loss Prevention (DLP)
Microsoft 365’s DLP policies help organizations automatically detect and prevent the unintentional sharing of CUI. By scanning emails, documents, and chat messages in real-time, DLP ensures that sensitive content doesn’t leave the organization without proper authorization, reducing the risk of data leaks and compliance violations. Additional information about Egnyte’s integration with Microsoft’s DLP solutions can be found here.
Information Rights Management (IRM)
IRM enables organizations to restrict access to emails and documents that contain CUI. It applies usage rights such as “read-only,” prevents forwarding or printing, and allows access only to authorized individuals. This ensures sensitive data remains controlled, even if it’s accidentally sent to the wrong person.
Azure Information Protection (AIP):
AIP provides automated classification and labeling for documents and emails, based on content sensitivity. This means CUI is consistently marked, tracked, and protected, even as it moves between users, devices, or cloud services. Labels can also trigger encryption and access control policies, enhancing security throughout the data lifecycle.
Compliance Manager
Microsoft’s Compliance Manager helps organizations assess, monitor, and improve their compliance posture. It maps controls to frameworks like NIST SP 800-171, offering actionable insights and risk-based scoring. For teams handling CUI, this tool adds measurable visibility into how well internal practices align with federal compliance requirements.
Best Practices for CUI Management
In order to effectively handle CUI, organizations need to:
- Create a CUI Program: Assign a CUI Program Manager to supervise compliance with the initiative
- Create policies and processes: Establish precise rules for managing, identifying, and protecting Controlled Unclassified Information
- Implement Security Controls: To safeguard CUI, implement administrative and technical controls
- Provide Training: Employees should receive regular training on CUI best practices and requirements, and management should make the training compulsory for users who manage CUI
- Monitor and Audit: To guarantee compliance, examine CUI handling and access on a continual basis
CUI Labeling and Managing
For compliance, CUI must be handled and marked correctly. Included are guidelines:
- Document Marking: Clearly mark documents that contain CUI with the appropriate markings
- Portion Marking: Show which sections of a document contain CUI
- Handling Guidelines: Adhere to the precise guidelines for handling various types of CUI
- Decontrolling: When the data is no longer protected, remove the CUI markings
- Destruction: When CUI is no longer needed, just securely destroy the data
Conclusion
CUI is crucial for protecting sensitive but unclassified data. The CUI program promotes information integrity by establishing consistent standards for file sharing, handling, and safeguarding. It facilitates compliance with relevant federal laws and fortifies national security. To maintain trust, lower risk, and facilitate the seamless operation of government partnerships and operations, strict adherence to CUI guidelines is still crucial.
Egnyte enables organizations to manage Controlled Unclassified Information (CUI) more intelligently by automatically identifying and classifying data across cloud and on-premise environments. It helps reduce the risk of data leaks through granular access control and secure sharing features, supporting data security and compliance. With real-time threat detection and pre-built compliance reports aligned with NIST SP 800-171, our EgnyteGov U.S. Federal Agency solutions make your CMMC journey easier.
Frequently Asked Questions
What is CUI specified?
CUI Specified refers to a type of Controlled Unclassified Information that comes with very specific rules for how it must be handled and protected. Ensuring organizational compliance with these rules is required by laws, regulations, or government-wide policies. The goal is to ensure that this sensitive information is kept safe and secure at all times.
What are the types of CUI?
CUI is diverse in categories such as Privacy Information, Financial Information, Proprietary Business Information, Law Enforcement Information, Critical Infrastructure Information, Export Control Information, Legal Information, Procurement and Acquisition Information, Intelligence and Defense-Related Information (Unclassified), and Immigration and Border Protection Data
What are the CUI system requirements?
Organizations must follow the security requirements specified in NIST SP 800-171, NIST SP 80-53, FIPS Publication 199, and FIPS Publication 200.
How do I protect Controlled Unclassified Information (CUI)?
Securing controlled unclassified information from improper access, use, or disclosure, the protection of CUI includes installing physical and electronic safeguards, implementing access control, providing recurring training, and establishing incident response measures. Content Security & Governance service providers like Egnyte can help you protect CUI.
Additional Resources

CUI Protection
Learn about the importance of CUI and how your organization can protect sensitive unclassified information.

CMMC Compliance
Your quick guide to meeting CMMC expectations—scoping, documentation, technical controls, and assessment readiness made simple.

Compliance Standards
Discover key compliance standards Egnyte supports to ensure data security and meet regulatory requirements across industries.