Unauthorized Access: Prevention Best Practices
In today's enterprise environment, where cloud adoption, remote work, and AI-driven threats continue to expand, preventing unauthorized access has become a critical business function. It directly impacts trust, regulatory compliance, and the ability to maintain uninterrupted operations. As a result, access control becomes a core element of any security and risk management strategy.
In this blog, we explore how unauthorized data access occurs, outline modern prevention strategies, and offer actionable guidance to strengthen access controls across digital and physical environments.
Let’s jump in and learn:
- What Is Unauthorized Access?
- Understanding Unauthorized Access in Cybersecurity
- How Unauthorized Access Occurs
- Best Practices: How to Prevent Unauthorized Access
- Unauthorized Access Incident Response: NIST-Aligned and Enterprise-Ready
- How Egnyte Aligns with Modern Enterprise Strategy
- Egnyte in Action: SouthStar Bank Case Study
- Conclusion
- Frequently Asked Questions
What Is Unauthorized Access?
Unauthorized access is when a person gains entry to a computer network, system, application software, data, or other resources without permission. Any access to an information system or network that violates the owner or operator’s stated security policy is considered unauthorized access. Unauthorized access is also when legitimate users access a resource that they do not have permission to use.
This “unauthorized access definition” forms the foundation of understanding risk.
However, unauthorized data access in cybersecurity today goes beyond this definition. It extends into cloud environments, AI-targeted phishing, and insider risks as well, making classic perimeter-based definitions no longer sufficient.
Understanding Unauthorized Access in Cybersecurity
The most common reasons for unauthorized entry are to:
- Steal sensitive data
- Cause damage
- Hold data hostage as part of a ransomware attack
- Play a prank
A common unauthorized access example today is attackers exploiting cloud misconfigurations, weak identity federation, or AI-generated phishing campaigns. These tactics highlight the growing risk of unauthorized access and the limitations of relying solely on traditional network perimeter defenses.
How Unauthorized Access Occurs
Understanding how unauthorized access occurs helps guide the implementation of best practices. Many common tactics fall into two broad categories: digital and physical.
Digital Unauthorized Access Tactics:
Digital unauthorized access tactics are methods attackers use to break into systems or steal data by taking advantage of weak security settings, flaws in software, or by tricking people into giving up sensitive information.
Guessing passwords
Guessing passwords is a common entry vector for unauthorized access. Manual password guessing is done using social engineering, phishing, or by researching a person to come up with information that could be the password. In scaled attacks, software is used to automate the guessing of access information, such as user names, passwords, and personal identification numbers (PINs).
Exploiting software vulnerabilities
Some software bugs are significant vulnerabilities that attackers can exploit to gain unauthorized access to applications, networks, operating systems, or hardware. These vulnerability exploits are commonly executed with software or code that can take control of systems and steal data.
Social engineering
Cybercriminals often gain unauthorized access by taking advantage of human vulnerabilities, convincing people to hand over credentials or sensitive data. These attacks, known as social engineering, often involve some form of psychological manipulation and use malicious links in email, pop-ups on websites, or text messages. Common social engineering tactics used to gain unauthorized access include phishing, smishing, spear phishing, ransomware, and impersonation. These tactics are increasingly powered by AI to personalize attacks.
Cloud misconfiguration exploits (such as exposed S3 buckets and IAM roles)
Attackers scan for misconfigured cloud storage or weak identity settings, allowing them to access sensitive data without authentication. These errors often go undetected in complex, multi-cloud environments.
Federated identity attacks
Threat actors exploit flaws in federated identity systems to impersonate users or escalate privileges across connected applications. Weak token validation or poor implementation of protocols like OAuth and OpenID Connect are common entry points for attacks.
Physical Unauthorized Access Tactics:
Cybercriminals often breach physical spaces to steal devices or install malware. Some take laptops or phones to access data offsite, while others target network hardware directly.
Tailgating or piggybacking
Tailgating is a tactic used to gain physical access to resources by following an authorized person into a secure building, area, or room. Attackers may pose as delivery staff or blend in with employees. Most of these situations occur "in plain sight."
Fraudulent use of access cards
Access cards that are lost, stolen, copied or shared pose an unauthorized access risk.
Door propping
While incredibly simple, propping open a door or window is one of the most effective ways for an insider to help a perpetrator gain unauthorized access to restricted buildings or spaces.
Other Unauthorized Access Tactics:
Collusion
A malicious insider can help an outsider get unauthorized access to physical spaces or digital access to systems. Together, they exploit gaps in access controls.
Passbacks
Passbacks are instances of sharing credentials or access cards to gain unauthorized access to physical places or digital systems.
Best Practices: How to Prevent Unauthorized Access
Preventing unauthorized access requires a layered approach that combines identity controls, data governance, data security and compliance, endpoint security, and continuous monitoring. These best practices reflect modern enterprise needs and enhance each layer of protection.
Identity and Access Governance
Limiting access to only those who need it is one of the most effective ways to reduce risk.
- Apply the principle of least privilege to all users and systems.
- Require multifactor authentication (MFA) for all accounts.
- Implement continuous risk-based authentication that adjusts access based on context, such as location, device health, and behavior.
- Adopt zero-trust policies that verify every access request as though it originates from an open network.
Data Protection and Cloud Intelligence
Data must be protected wherever it resides or moves, especially in hybrid cloud environments.
- Continue to encrypt data during viewing, exchange, and storage.
- Use automated data classification to tag sensitive content, making policy enforcement more effective.
- Use file-access anomaly detection to flag suspicious behavior in real time.
Endpoint and Device Security
Endpoints remain a common target for attackers. Strengthening them is essential.
- Keep systems updated with security patches and run anti-malware software regularly.
- Use lock screens and shut down devices when not in use for extended periods.
- Enable single sign-on (SSO) where applicable.
- Assess device posture before granting access to sensitive resources.
- Integrate endpoint detection and response (EDR) tools to detect and contain threats early.
Insider Risk and Monitoring
Not all threats come from the outside. Monitoring internal access is just as important.
- Continue encouraging employees to report suspicious activity.
- Set up automated alerts using user behavior analytics (UBA) to detect unusual patterns or access attempts.
- Conduct regular access reviews and enforce audit workflows. This helps ensure that users retain only the access they need, minimizing exposure.
Data Lifecycle Management
Good data hygiene reduces attack surfaces and supports compliance.
- Back up data regularly and store it securely.
- Encrypt sensitive backups, especially when stored in cloud environments.
- Properly dispose of old data using cross-cut shredders for paper and certified recycling services for devices.
- Implement immutable backups that cannot be modified once written.
Use policy-driven retention and deletion schedules to manage data according to compliance requirements.
Unauthorized Access Incident Response: NIST-Aligned and Enterprise-Ready
Effective incident response starts well before a breach occurs. Organizations should align their approach with the National Institute of Standards and Technology (NIST) guidelines, specifically SP 800‑61 Revision 2, which outlines a four-phase lifecycle for handling security incidents, including unauthorized access.
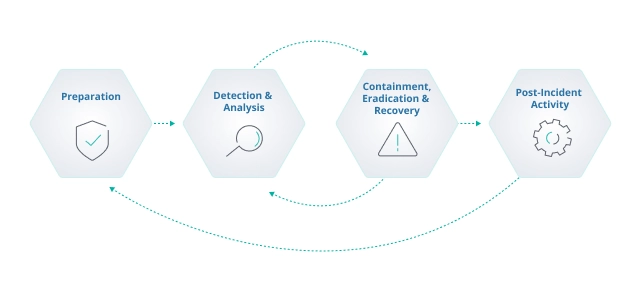
1. Preparation
Establish clear policies, roles, and responsibilities.
Develop and regularly update incident response playbooks that cover access revocation, forensic logging, and internal escalation procedures.
- Ensure that incident response teams are trained and ready to act quickly.
2. Detection and Analysis
Monitor systems continuously for unusual access patterns or behavior.
Use tools that provide timestamped audit logs and enable correlation across systems to identify the scope and severity of the incident.
- Set clear thresholds and triggers for alerts so your response team can act within minutes of detecting suspicious activity.
3. Containment, Eradication, and Recovery
- Once unauthorized access is confirmed, isolate affected accounts or systems immediately.
Remove any malicious software or compromised credentials.
- Restore affected services from secure backups and validate that all systems are fully patched and secure before resuming normal operations.
4. Post-Incident Review
Conduct a root cause analysis to understand how the breach occurred and identify any gaps in controls.
Update security policies, access protocols, and response procedures based on lessons learned.
- Document the incident and communicate findings with relevant stakeholders to improve future readiness.
How Egnyte Aligns with Modern Enterprise Strategy
Egnyte strengthens enterprise data protection through unified access governance, AI-powered behavioral analytics, and insider risk controls.
Early ransomware detection, exposure alerts for sensitive data, and continuous monitoring of user behavior help security teams act before damage occurs. Built-in safeguards like auto-quarantine and granular sharing permissions help prevent data loss without slowing down productivity.
Egnyte in Action: SouthStar Bank Case Study

Challenge
SouthStar Bank relied on a legacy on-premises file server with VPN, which caused serious issues. Collaboration slowed as only one person could edit a file at a time. They lacked visibility into where sensitive customer and proprietary data resided or who had access. Backup capacity was exhausted, risking data availability.
Solution
SouthStar implemented Egnyte to address these challenges. Key moves included:
- Implementing real-time co-editing and Microsoft Office integration, reducing bottlenecks.
- Unifying security through a centralized dashboard that surfaced real‑time alerts for unusual activity and allowed quick permission changes.
- Migrating to hybrid cloud storage, eliminating on-prem backup constraints and enabling remote access from any device.
Result Highlights
- 20,000 improperly located sensitive files were discovered and remediated, dropping to zero.
- Saved approximately $10,000 annually by consolidating and retiring legacy tools.
- User adoption was smooth. Employees retained familiar workflows with added security and responsiveness.
Conclusion
If you’re still relying on basic password hygiene or network firewalls, you misunderstand the unauthorized access meaning in modern environments. Prevention requires a proactive, governance-first strategy powered by data classification, behavioral analytics, device trust, and hybrid infrastructure integration.
Egnyte delivers on this edgeless architecture, helping you stop unauthorized access before it disrupts your business.
Frequently Asked Questions
Q. How can unauthorized access be prevented?
Prevent unauthorized access by enforcing least privilege, using multifactor authentication, keeping software updated, and monitoring user activity. Secure sensitive data with encryption and apply strong password policies. Regularly audit access rights and use automated tools to flag unusual behavior or risky permissions.
Q. How to protect a network from unauthorized access?
Use access controls based on roles and responsibilities, employ MFA for all users, and block access from unmanaged or outdated devices. Monitor data access continuously, enforce encryption, and regularly review permissions. Conduct employee training to reduce risks from phishing or credential sharing.
Q. How to detect unauthorized access?
Set up real-time alerts for unusual login patterns, file activity, or access from unfamiliar devices. Use behavior analytics to detect deviations from normal user actions. Review audit logs regularly and integrate detection tools with incident response systems to act quickly on any red flags.
Q. What is an example of an insider threat?
An insider threat can be an employee who downloads sensitive files before leaving the company or shares login credentials with unauthorized users. It can also involve unintentional actions, like clicking on phishing links or misconfiguring access settings that expose data to outsiders.
Additional Resources

Ask An Expert
We’re pleased to invite you to our “Ask An Expert” live Q&A with Egnyte’...

Protecting Against Insider Threats
Egnyte helps stop data leaks with restricted access, behavior monitoring, and alerts for unusual file activity.

Understanding Sensitive Data
A simple breakdown of what counts as sensitive information—and why context matters for protection.