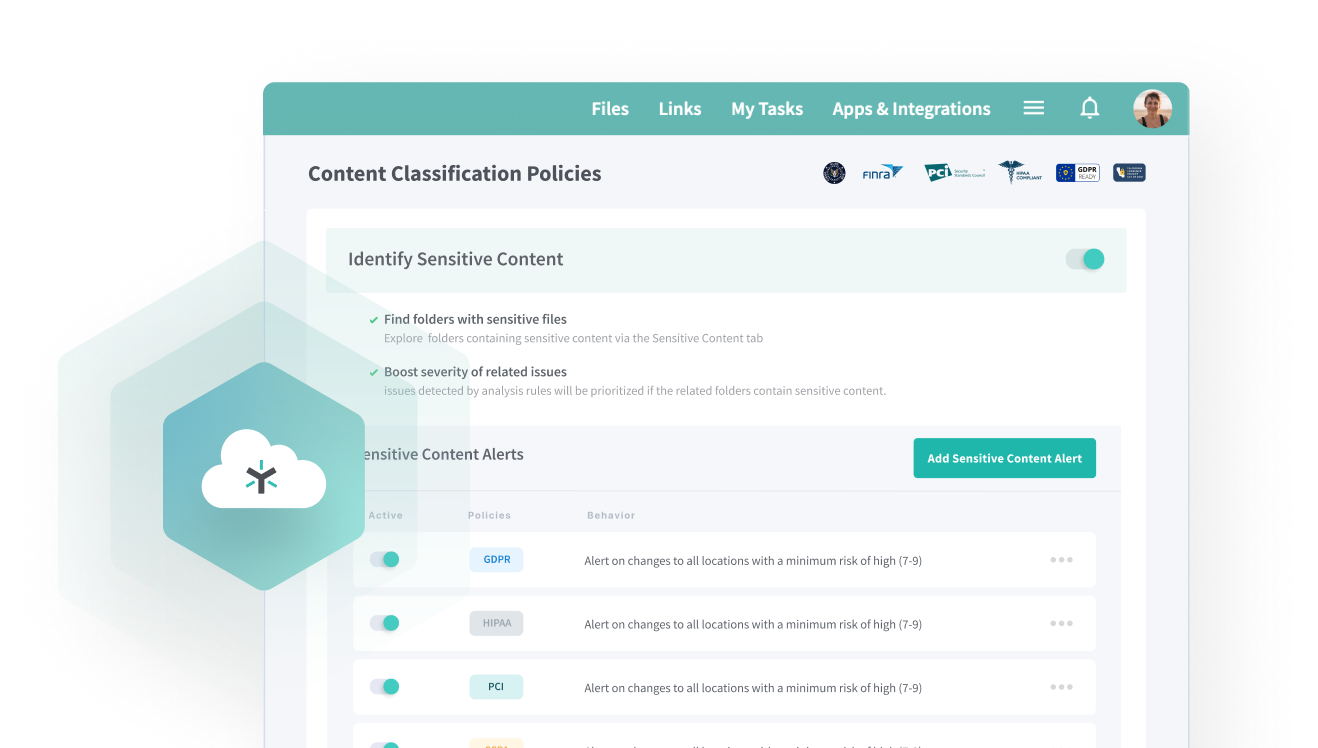
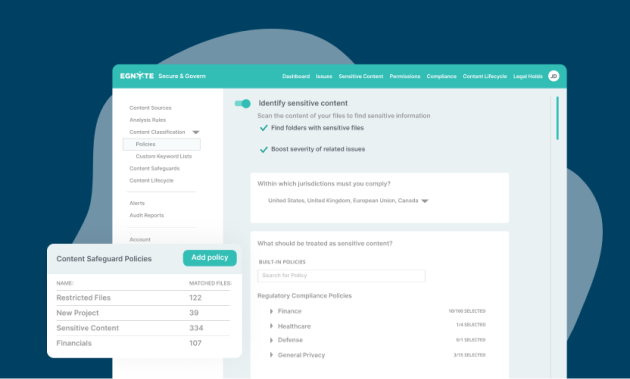
Content Intelligence
There’s More to Explore
Learn more about how Egnyte empowers distributed teams to access, share, and secure company data.
Recognized as a Leader in Security, Governance and Collaboration by G2







Learn more about how Egnyte empowers distributed teams to access, share, and secure company data.




