Secure Document Sharing
Secure document sharing is the distribution of documents using digital processes to protect the shared data from unauthorized access. Documents may be shared between two people or groups, but these are defined as authorized to access the information.
Used mostly within organizations, secure document sharing is required to maintain confidentiality or limit the distribution of sensitive information to select individuals or groups that have a reason to view it. Secure document sharing also ensures compliance with regulations and enforces organizations’ data loss prevention (DLP) policies. Examples of when secure document sharing is used include:

- Business information (e.g., customers, partners)
- Financial transactions (e.g., contracts, IPOs, fundraising, mergers, acquisitions)
- Information legally deemed sensitive (e.g., personally identifiable information (PII), or protected health information (PHI).
- Intellectual property (e.g., formulas, processes)
- Sales information (e.g., pipelines, forecasts)
Often, secure document sharing is managed using a combination of security solutions. Two of the most commonly used are encryption and access controls. When encryption is used for secure document sharing, it is applied when files are stored and/or being transmitted.
Secure document sharing with encryption can also be done through a private network connection, such as a VPN. Access controls are also used to support secure document sharing. These restrict what can be done with a document. For instance, only specific people have the right to access, view, and download the file.
Let’s jump in and learn:
- Secure Document Storage
- Human-Based Security for Document Sharing
- Secure Document Sharing Solutions
- Secure Document Sharing and Collaboration
- Office 365 Secure Document Sharing
- Benefits of Secure Document Sharing
- Improve Security and Compliance with Secure Document Sharing
- Ensure Compliance and Protect Sensitive Information with Secure Document Sharing
Secure Document Storage
Each type of secure document storage system has different features and processes to protect sensitive data. It is important to consider technical and human-based security when evaluating secure document storage solutions.
Technical Security
The solutions software components make up the technical security. Data encryption, multi-factor authentication, and permissions management are the most commonly used security tools.
- Data Encryption
An essential function of a secure document storage system is data encryption. Specialized algorithms render the text in documents unreadable without a unique key. This is the most reliable way to protect sensitive information.
First used by the military and government for secure document sharing, encryption is now widely used to protect data while it is in storage and in transit. - Multi-Factor Authentication
Multi-factor Authentication (MFA) is an authentication method that requires two or more verification factors for a user to gain access to a resource, such as a document. These factors include:- Something you know, such as a password, passphrase, or personal identification number (PIN)
- Something you have, such as a token or smartcard
- Something you are, such as a biometric (e.g., fingerprint, facial scan)
Role-Based Access Controls
With role-based access controls (RBAC), individuals are assigned a role that comes with one or more permissions that grant access to protected documents. Access is restricted to the information necessary to perform duties effectively.
Human-Based Security for Document Sharing
Human-based security features can complement technical approaches. These features address security lapses by individuals, such as granting access to an unauthorized user, printing files, sharing documents, and lax password management. Following are several human-based security tactics used to ensure secure document sharing.
- Document Download and Printing Controls
An administrator or document creator can set rules for who has permission to download or print a document with document download and printing controls. For instance, a document could be set to “view only” with only specified users permitted to download or print it to ensure secure document sharing. - User Activity Audit Logs
Used in many secure document sharing solutions, audit logs provide a detailed record of all activity from all users. Included in audit logs are:- Dates and times users log in
- Actions are taken within the system
- Documents and files opened
- Any edits or changes made to documents or files
Digital Watermarking
For secure document sharing, digital watermarks can be used. These can be set as visible or hidden. Mostly, digital watermarking is used to remind users of the proper use of a document.
However, for highly-sensitive documents, sophisticated invisible digital watermarks can be used. These can be programmed to track who has used the document, making it easy to identify individuals who misuse it.
Secure Document Sharing Solutions
There are many secure document sharing solutions, each with different features, prices, and security protocols. The use cases in an organization usually help drive the decision based on the optimal fit based on IT and user requirements. Several types of secure document sharing solutions are as follows.
Cloud-Based Solutions for Secure Document Sharing
With cloud-based secure document sharing solutions, organizations or individual users have storage space on a server, and document access and sharing are done via the internet. These solutions give users access to documents with a connected device from any location. Depending on the sophistication of the secure document sharing solution, various types and levels of controls, security, tracking, and backup can be enabled. When managed at the enterprise level, cloud-based file sharing provides a centralized system for secure document management.
Email Providers
For better or worse, email is widely used to share documents. In some cases, email systems are set up to include tools to ensure secure document sharing. However, email can be a significant gap in secure document sharing protocols without these security systems in place.
Secure File Transfer Protocol (SFTP) for Document Sharing
While an older technology, FTP is still a standard way of sharing files for many organizations. It can be used natively with a command prompt. However, it is more common to use products that make it more user-friendly. Solution providers have developed a software wrapper that allows users to simply drag and drop files to upload them to any destination. FTP does not have encryption, but SFTP does. SFTP protects data-in-transit data using an encryption shell that is also known as SSH (secure shell protocol).
Peer-to-Peer (P2P) Networks
P2P document sharing uses software rather than a web browser to enable computers to communicate directly without hosting files on a central server. With P2P sharing, individual users connect to a distributed peers’ network to transfer over their network connections. P2P sharing poses a security risk for organizations and individuals, including inadvertent publishing of private information, exposure to viruses and worms, and spyware.
Removable Storage
When a network connection is unavailable, physical storage media can be used for secure document sharing. The key to this is to add password protection to the document to secure it if the physical media is lost or stolen.
Virtual Data Rooms (VDRs)
VDRs are so commonly used as part of financial transactions that they are often called virtual deal rooms. It offers a highly secure document sharing system for document storage and distribution and usually includes features and functionality to support financial deals in mind. Key features of VDRs are granular access control when sharing documents and sophisticated security options.
Secure Document Sharing and Collaboration
Basic secure document sharing focuses on the transfer of files. Secure document sharing and collaboration add functionality to allow multiple users to work together on documents or files.
It eliminates the lag times and version controls issues of transferring files from one person to the next. In addition, secure document sharing and collaboration files include version controls and tracking tools to create an auditable record of how a document was created and identify any authorized changes. Other features in secure document sharing and collaboration tools include:
- Ability to collaborate and share files with users outside the company firewall
- Activity feeds and alerts via message or email
- Approval workflow
- Change history of files and documents
- Capacity to easily work on and share large files
- Enforcement of security and compliance protocols
- Instant messaging
- Notifications when others are active on documents owned by another person
- Permission frameworks
- Real-time commenting
Office 365 Secure Document Sharing
With Office 365, secure document sharing can be deployed across an organization to enforce rules based on the sensitivity of the information and who can access it, such as:
- Anyone
- Any internal users
- Authorized users inside the organization
- Authorized users inside and outside the organization
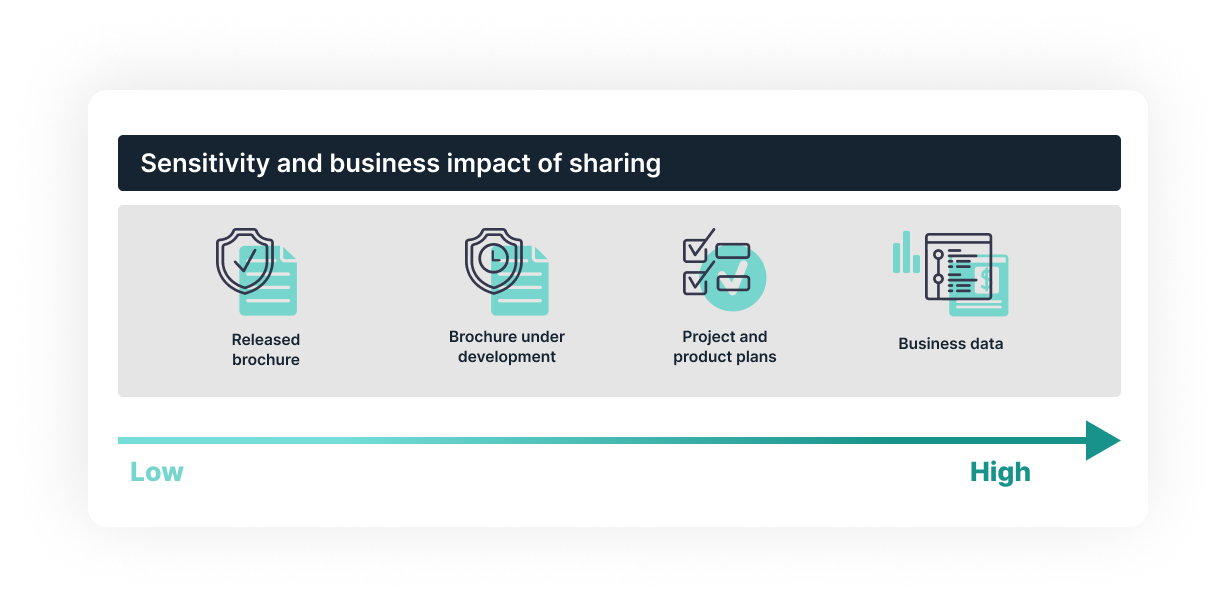
Office 365 also provides tools to manage access, sharing, and collaboration for documents with different sensitivities—baseline, sensitive, and highly sensitive. It is recommended to begin with the baseline tier and then add teams that use the sensitive and highly sensitive tiers based on secure document sharing restrictions required.
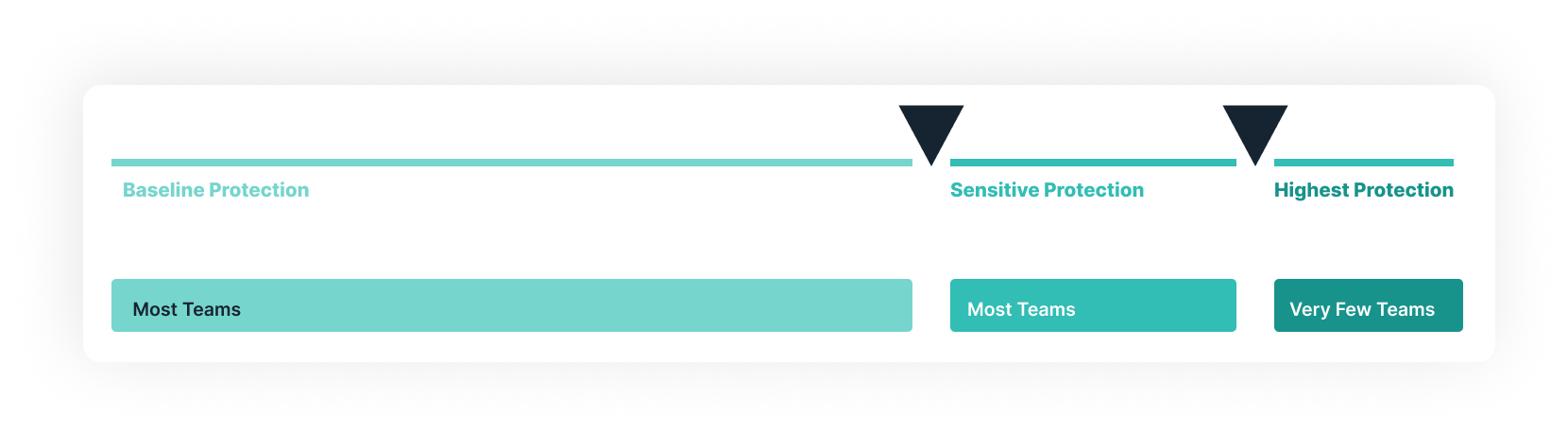
Following are recommendations for secure document sharing settings based on the type of collaboration and the level of document sensitivity. This helps enforce data governance rules and best practices to ensure optimal secure document sharing.
| Type of Sharing | Baseline tier | Sensitive tier | Highly sensitive tier |
|---|---|---|---|
| Public or private team | Either | Private | Private |
| Unauthenticated sharing | Blocked | Blocked | Blocked |
| File sharing | Allowed | Allowed | Only team owners can share |
| Team membership | Anyone can join public teams, but owner approval is required to join private teams | Team owner approval is required to join | Team owner approval is required to join |
| Document encryption | Not available | Not available | Available with a sensitivity label |
| Guest sharing | Allowed | Can be allowed or blocked | Can be allowed or blocked |
| Unmanaged devices | No restriction | Web-only access | Blocked |
Benefits of Secure Document Sharing
- Creates considerable transparency
- Easy for third parties (e.g., contractors, partners, customers) to safely share files
- Enhances efficiency across an organization
- Expedites task completion by facilitating the dissemination of documents
- Helps identify errors
- Improves responsiveness
- Increase profitability
- Keeps files up to date
- Maintains document history
- Monitors and enforces access based on controls
- Real-time collaboration on projects
- Simplifies authorized access to documents
- Streamlines the flow of information
- Tracks revisions
Improve Security and Compliance with Secure Document Sharing
Sharing documents puts organizations at risk of compliance violations when sensitive information is involved. Dozens of countries worldwide have national privacy laws that impact interactions with their citizens’ data, such as the stringent General Data Protection Regulation (GDPR). Below are some of the many laws governing data privacy in the United States.
- Bank Secrecy Act (BSA)
- California Consumer Privacy Act (CCPA)
- California Online Privacy Protection Act (CalOPPA)
- Fair and Accurate Credit Transactions Act (FACTA)
- Fair Credit Reporting Act (FCRA)
- Federal Information Processing Standards (FIPS) 140-2
- Gramm-Leach-Bliley Act (GLBA)
- Health Information Technology for Economic and Clinical Health Act (HITECH Act)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- Service Organization Control 2 (SOC 2)
- SOC 2
- Stop Hacks and Improve Electronic Data Security Act (SHIELD)
- US Privacy Act of 1974
The following tips will help ensure data security and adherence to privacy regulations.
- Avoid removable storage devices to eliminate the chances of theft or loss as well as the danger of viruses that can deliberately or inadvertently infect files
- Train users on secure document sharing best practices, such as how secure file sharing works, acceptable locations to downloading and storing documents, which documents can be shared, and why it is important
- Limit secure document sharing to only the information that an authorized user legitimately needs
- Enforce robust password protocols, including:
- Change passwords regularly
- Create strong passwords with at least 12–15 characters, using a combination of upper and lowercase letters, including special symbols and numbers, and avoiding the use of dictionary words, places, and other common words
- Do not use email addresses or names for user name
- Save password hints in a secure location
- Use password managers to create and manage passwords
Ensure Compliance and Protect Sensitive Information with Secure Document Sharing
Secure document sharing continues to play a key role in organizations’ overall security posture. Why? Simply because it works well. Secure document sharing is one of the most effective ways to prevent data loss and unauthorized access to sensitive data.
Which method is best depends on the types of information being shared and the organization. For some, FTP is sufficient, while for others, a more robust cloud-based system is needed. Regardless of the solution, training remains a crucial part of successfully implementing secure document sharing. Users must know when, how, and why to use these systems effectively.
Being able to securely share documents, while preventing oversharing or unauthorized sharing is important—not just to protect information, but also to enhance productivity. Having the right secure document sharing system in place makes this possible to efficiently implement regardless of the size of an organization or scale of documents
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 6th January, 2023