Office 365 Security Checklist
There are many versions of an Office 365 security checklist. The items that should be included in each version of an Office 365 security checklist vary based on the type of organization. Following are a few items that find their way onto most organizations’ Office 365 security checklist.
- Alert policies
- Application consent and permissions management
- Application protection policies configured
- Backups
- Compliance labels and policies set up
- Encryption
- Legacy authentication blocks
- Mailbox auto-forwarding to remote domains disabled
- Multi-factor authentication enabled
- Pre-set security policies implemented
- Security defaults with conditional access policies replaced
- Unified audit log enabled

With over 50 apps and three security dashboards across various license tiers, M365 can be a complex tool to master, making it easy to overlook critical security settings. Egnyte offers a complete M365 checklist to make sure all your organization’s data is secure.
Microsoft 365 Security Best Practices
Following are several common best practices to include on an Office 365 security checklist.
- Create and manage data loss prevention (DLP) policies to protect sensitive information and adhere to compliance requirements.
- Deploy an anti-malware solution that includes protection against ransomware attacks.
- Develop and enforce password protocols that require strong passwords and restrict reuse.
- Ensure that email messages shared and received internally and externally are encrypted.
- Have admins create dedicated accounts for work that requires privileged access and use another account for non-administrative tasks.
- Implement anti-phishing protection and safe attachment protection to prevent phishing attacks and block malicious attachments.
- Protect mobile devices with mobile device management (MDM) that includes security.
- Train employees on cyber security fundamentals, including how to maintain passwords, recognize phishing emails, and understand security features on their mobiles and laptops.
- Turn on advanced threat protection (ATP) to prevent malicious links and attachments from getting into users’ inboxes.
- Use multi-factor authentication to prevent unauthorized access to resources.
Microsoft Office 365 Security Recommendations
Consider the following recommendations when creating an Office 365 security checklist.
- Activate alerts for unusual activities and logging to reduce the time needed to effectively identify and mitigate risk
- Assign administrator roles using role-based access control (RBAC) and practice the principle of least privilege for all users, including administrators
- Disable legacy protocol authentication that does not support MFA features, such as Post Office Protocol (POP3), Internet Message Access Protocol (IMAP), and Simple Mail Transport Protocol (SMTP).
- Enable multi-factor authentication for administrator accounts and the accounts of regular users
- Incorporate Microsoft Secure Score to gain visibility into the organization’s security posture and identify gaps
- Integrate and correlate UAL with data from a SIEM tool
- Use Unified Audit Log (UAL) to support threat identification and investigations
Office 365 Security Features
The key features of Microsoft 365 security can be categorized into four core segments—identity access and management, threat protection, information protection, and security and risk management.
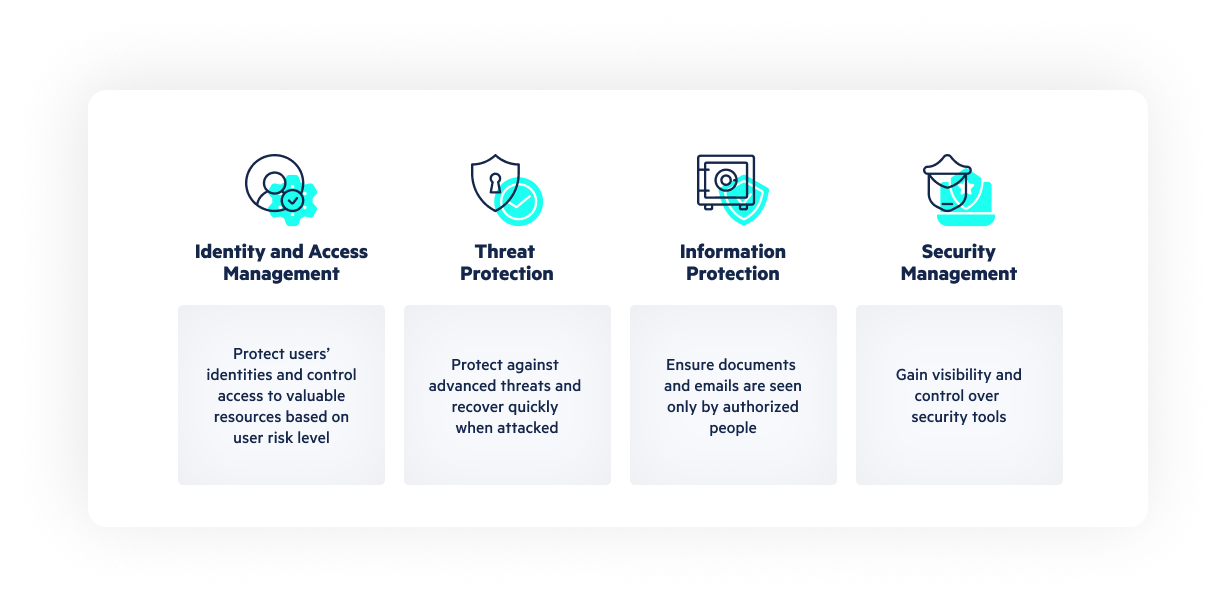
1. Identity and access management provides s a framework of policies, processes, and technology to ensure that the right people and roles in an organization (identities) can access the resources they need. Managing with user credentials and other authentication methods (e.g., multi-factor authentication) verifies that the user is who they are claiming to be. Identity and access management systems enable IT admins to manage a range of identities, including people, software, and hardware (e.g., computers, networks, applications, IoT devices). Using identity and access management helps deflect suspicious login attempts and protect user credentials with risk-based access controls, identity protection tools, and strong authentication options. Part of an Office 365 security checklist should be these identity and access management features:
- Seamless user experience
- Secure adaptive access
- Simplified identity governance
- Unified identity management
2. Threat protection includes integrated, automated security solutions to secure email, data, applications, devices, and identities. It provides defense against malware or hacking-based attacks that target sensitive data as well as monitors activity across an entire attack surface to ensure that threats are identified and neutralized quickly. An Office 365 security checklist should include these threat protection features:
- Endpoint protection
- Extended detection and response (XDR)
- Security information and event management (SIEM)
3. Information protection helps IT admins locate, organize, and protect an organization’s sensitive information across clouds, applications, and endpoints. These solutions help keep sensitive data secure at rest and in transit. Information protection systems are used to configure data security policies with sensitivity labels using rules to assign security policies to files that follow data regardless of where it goes. Features that should be on an Office 365 security checklist for information protection should be:
- Data classification
- Data loss prevention (DLP)
- Data governance
4. Security and risk management tools are available in a central portal that allows admins to quickly identify and remediate risks from malicious and unintentional activities as well as perform investigations after an incident. An Office 365 security checklist for security and risk management should include:
- Advanced audit capabilities
- Communication compliance enforcement
- Information barriers
- Insider risk Management
- Privileged access management (PAM)
Office 365 Security Standards
When compiling an Office 365 security checklist, it is important to consider compliance. Among the many security standards supported by Office 365 are:
- California Consumer Privacy Act (CCPA)
- Canadian Personal Information Protection and Electronic Documents Act (PIPEDA)
- Data processing agreements (DPAs)
- Defense Federal Acquisition Regulation Supplement (DFARS)
- Family Educational Rights and Privacy Act (FERPA)
- Federal Information Processing Standard (FIPS) Publication 140-2
- Federal Information Security Management Act (FISMA)
- Federal Risk and Authorization Program (FedRAMP)
- Financial Industry Regulatory Authority (FINRA) Rule 4511(c)
- General Data Protection Regulation (GDPR)
- Gramm–Leach–Bliley Act (GLBA)
- Health Insurance Portability and Accountability Act (HIPAA)
- ISO/IEC 27001
- National Institute of Standards and Technology (NIST) SP 800-171
- Payment Card Industry (PCI) Data Security Standards (DSS)
- Sarbanes-Oxley Act of 2002 (SOX)
- Securities and Exchange Commission (SEC) Rule 17a-4(f)
- SOC 2 Type 2
- SOC 3
- Statement on Standards for Attestation Engagements No. 16 (SSAE 16)
- System and Organization Controls (SOC) 1 Type 2
- Virginia Consumer Data Protection Act (VCDPA)
Using an Office 365 Security Checklist Helps Avoid Pitfalls
As one of the world’s most widely used productivity suites, Office 365 is used by millions of organizations. Continuous enhancements have brought Office 365 security to the highest levels of quality and breadth. To reap the benefits of the security baked into the products and the state-of-the-art security infrastructure and processes that protect Microsoft datacenters, it is important to understand that Microsoft follows a shared responsibility model with regard to security.
With the shared responsibility model, Microsoft accepts responsibility for its applications and servers. The users and organizations that run Office 365 are responsible for the data within the cloud. Creating and following an Office 365 security checklist means that Office 365 security best practices are adhered to, and risk is minimized. An Office 365 security checklist does this by helping avoid known pitfalls.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 31st January, 2023


