Cybersecurity Maturity Model Certification Framework
The CMMC framework is a set of best practices and processes created by the United States Department of Defense (U.S. DoD), which was first introduced in 2020 and significantly refined in 2021. By approximately March 2025, any organization that provides products or services to the DoD will be required to certify compliance with the CMMC framework.

| “CMMC stands for ‘Cybersecurity Maturity Model Certification’ and is a unifying standard for the implementation of cybersecurity across the Defense Industrial Base (DIB). The CMMC framework includes a comprehensive and scalable certification element to verify the implementation of processes and practices associated with the achievement of a cybersecurity maturity level.” —The Office of the Under Secretary of Defense for Acquisition & Sustainment Cybersecurity Maturity Model Certification |
What Is the CMMC Framework?
The CMMC framework incorporates federal guidelines used by other agencies outside of the DoD, such as:
- The National Institute of Standards and Technology Special Publication 800-171 (NIST SP 800-171) Rev. 2
- NIST SP 800-172
- 48 Code of Federal Regulations 52.204-21 (48 CFR 52.204-21), commonly referred to as the FAR Clause or FAR 52.204-21: Basic Safeguarding of Covered Contractor Information Systems
The CMMC framework is designed to ensure that defense contractors and sub-contractors, also known as the defense industrial base (DIB), can be trusted to safeguard controlled unclassified information (CUI) and federal contract information (FCI).
The CMMC framework details specific cybersecurity requirements to qualify for DoD contracts and drive security standards throughout the DoD’s multi-tiered supply chain.
Consolidated into three maturity levels, the CMMC framework details specific security criteria that must be met to achieve certification:
1. CMMC Level 1 contains 15 requirements that are aligned with FAR 52.204-21.
2. CMMC Level 2 contains 110 requirements that are aligned with NIST SP 800-171 Rev. 2.
3. CMMC Level 3 contains the 110 NIST SP 800-171 Rev. 2 requirements that are referred to in the Level 2 description above, along with 24 additional requirements from NIST SP 800-172.
NIST Cybersecurity Framework Maturity Levels
National Institute for Standards and Technology (NIST) published version 1.0 of their Cybersecurity Framework (NIST CSF) in February 2014, in response to Executive Order 13636 as part of its efforts to improve critical infrastructure cybersecurity. Conformity to the NIST cybersecurity framework maturity levels is measured according to four tiers. Those tiers provide a standard to describe the level to which an organization is prepared to detect, identify, and respond to cyberattacks.
- Tier 1—Partial
The lowest of the NIST cybersecurity framework maturity levels is Tier 1. At this level, cybersecurity risk management has not been formalized or documented. Threats are addressed on a reactive, ad-hoc basis. Organizations categorized as Tier 1 are at significant risk of a successful cyberattack, because of their limited ability to recognize and effectively respond to cyber-threats. Simply put, they do not lack advanced technical and administrative cybersecurity controls. - The good news is that there’s always room for improvement. This Egnyte blog provides you with several key steps you can take now to improve data security.
- Tier 2—Risk-Informed
At Tier 2 of the NIST cybersecurity framework maturity level, the organization’s stakeholders are aware of the deficiencies and risks. However, risk management systems and processes may not be implemented organization-wide. Tier 2 organizations have some controls and policies in place to protect digital assets, and risks are addressed reactively in an ad-hoc manner. - Tier 3—Repeatable
At Tier 3 of the NIST cybersecurity framework maturity level, organizations have established repeatable processes to identify and respond to threats. These organizations also have formal risk-management processes in place, along with well-defined cybersecurity policies. Tier 3 is the recommended minimum level for most organizations because it ensures that they have an effective defense against new and emerging threats. - Tier 4—Adaptable
The highest of the NIST cybersecurity framework maturity levels is Tier 4. Organizations at Tier 4 continuously improve and adapt their security posture to thwart new and emerging threats. To reach Tier 4, organizations regularly conduct risk assessments and adjust security policies and procedures to take advantage of new solutions and remediate vulnerabilities to new threats. At Tier 4, cybersecurity systems rely heavily on a steady stream of security-related data that’s processed with advanced analytics to gain insights and hone systems and processes.
Cyber Maturity Assessment Framework
There are different types of security maturity models, most of which use similar approaches. To effectively use a security maturity model framework, organizations need to embrace their potential and use the models to better understand and identify security weaknesses.
Security maturity models can also be used as a path to metrics and measurement from which improvements to security programs can be more easily communicated and visualized. Cyber maturity assessment frameworks collect cybersecurity best practices and provide a benchmarking tool that organizations can use to evaluate their cybersecurity preparedness. Several reasons why organizations should use a security maturity model framework are that they:
1. Provide a view of the organization’s current security posture
2. Benchmark against industry requirements
3. Help prioritize cybersecurity investment
4. Balance the company’s cybersecurity portfolio
5. Inform security strategy and roadmap decisions
6. Help CISOs to communicate the importance of security to executives and the Board of Directors
7. Facilitate protection of systems and data
8. Facilitate compliance with applicable laws and regulations
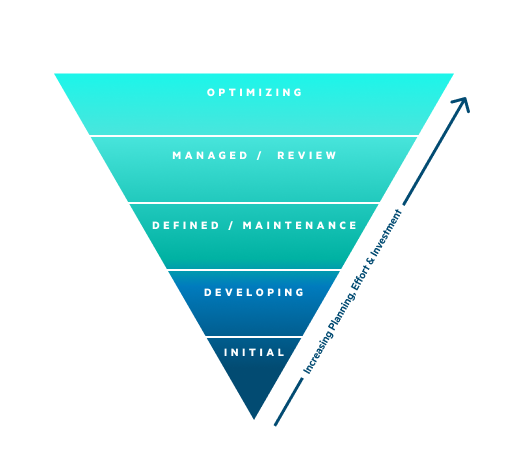
Five Security Maturity Model Framework Levels
Another type of cyber maturity assessment framework defines five distinct maturity levels, which indicate the degree to which an organization has optimized security systems and processes. During the progression from level one to level five, an organization will develop, refine, and enhance its cybersecurity posture. This approach is similar to the framework that we explored earlier in this article.
Key process areas characterize each level. When considering the cyber maturity assessment framework levels, it is helpful to keep these key process areas in mind.
- Commitment to perform
- Ability to perform
- Activities performed
- Measurement and analysis of results
- Verification of process implementation
Level 1: Initial
- Ad-hoc decision-making
- No formalized processes in place
- Reactive processes
- Undocumented processes and decision-making
Level 2: Repeatable
- Basic inventory of processes
- Some process documentation
- Some processes are more regular
Level 3: Defined
- Formal and standardized approach
- More consistent practices
- Processes are established and defined
Level 4: Managed
- Integrated with organizational decision-making
- Processes measured, refined, and adapted
- Understanding of current risk environment
Level 5: Optimizing
- Processes automated and analyzed
- Cybersecurity is part of the overall organizational culture
- An understood link to the larger organization
CMMC Framework Brings Positive Changes to DoD Supply Chain
While some organizations initially see frameworks as a time-consuming item on an already long to-do list, most come to see the CMMC framework as a benefit that extends beyond meeting the DoD’s requirements. The CMMC framework is widely seen as a powerful tool in IT and security teams’ ongoing efforts to defend their organizations against persistent cyber threats. In addition, the fact that the CMMC framework is aligned with proven governmental standards (e.g., NIST SP 800-171, NIST SP 800-172, and 48 CFR 52.204-21, or FAR 52.204-21) gives it credibility. This alignment and the organization of the CMMC framework have won it support and praise from users and industry experts alike.
Egnyte has experts ready to answer your questions. For more than a decade, Egnyte has helped more than 16,000 customers with millions of customers worldwide.
Last Updated: 21st November, 2024