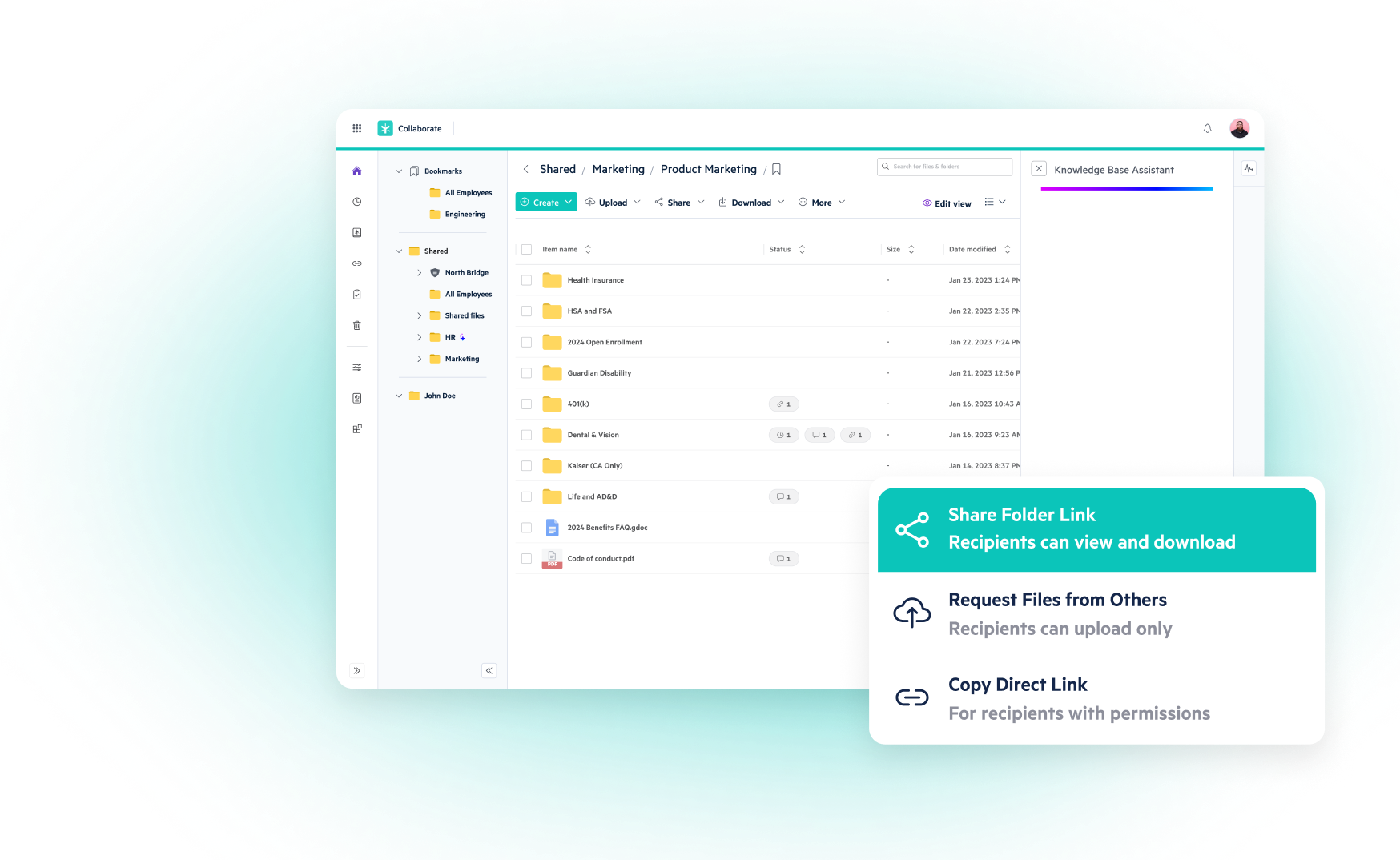
Comprehensive Strategies for Effective CUI Protection Across All Digital and Physical Assets
Every federal contract carries a hidden risk: Data exposure.
Controlled Unclassified Information (CUI) now sits at the center of procurement decisions, audit readiness, and long-term vendor trust. Yet too often, it's treated as a background IT problem rather than a business-critical priority.
In reality, the ability to identify, govern, and demonstrate CUI data protection across environments has become a defining factor in contract performance and revenue continuity. Organizations engaging with federal agencies must address this holistically. Executives are expected to understand not just where CUI resides, but how effectively it is protected, audited, and governed.
This blog explores practical strategies for how to protect CUI from initial identification to policy enforcement. It provides a roadmap for aligning technical safeguards with business priorities, enabling scalable, cost-effective, and audit-ready CUI data protection.
Let’s jump in and learn:
- TL;DR: Effective CUI Protection for Digital & Physical Assets
- What Qualifies as Controlled Unclassified Information?
- Why CUI Protection Is a Strategic Business Imperative
- Steps to Identify Controlled Unclassified Information
- How to Protect the Confidentiality of CUI?
- Myths That Undermine Effective CUI Protection
- Conclusion
- Frequently Asked Questions:
TL;DR: Effective CUI Protection for Digital & Physical Assets
- CUI requires structured protection under federal mandates, even though it is not classified.
- Failing to protect CUI can result in contract loss, failed audits, and regulatory exposure.
- Identification and classification of CUI must be the first step in any protection strategy.
- Compliance with CMMC and NIST frameworks demands layered technical and procedural safeguards.
- Myths about labeling, storage, and cloud use often lead to critical oversights.
What Qualifies as Controlled Unclassified Information?
Controlled Unclassified Information refers to federal data that is sensitive but not classified. This information is created by, or on behalf of, the government and is not intended for public release. CUI protection applies to any system or environment where this data is processed, stored, or transmitted.
Examples of CUI include:
- Internal contract deliverables
- Engineering blueprints and technical documentation
- Project schedules, system logs, or compliance reports
- Research data governed by export controls
- Sensitive test results or configuration files
This type of data may not carry a "classified" label, but the CUI protection requirements are formalized through federal regulations and must be addressed at the enterprise level.
Why CUI Protection Is a Strategic Business Imperative
While CUI does not fall under classified information protocols, it is governed by standards such as NIST SP 800-171 and enforced under frameworks like CMMC. For organizations engaged in federal work, protecting CUI data is tied directly to operational continuity and eligibility for future contracts. However, many companies struggle to answer a basic question: How do you protect CUI when it exists across disconnected systems, shared repositories, or legacy tools?
Understanding what qualifies as CUI determines:
- The scope of compliance obligations
- The resources required for audit readiness
- The risks tied to exposure or mismanagement
- The investment needed in data governance and security architecture
Key compliance points include:
- CMMC Level 2 applies to contractors who manage CUI and includes 110 security controls.
- These controls focus on access restrictions, encryption, monitoring, and incident response.
- CUI data protection must extend across physical, digital, and hybrid infrastructure.
Failing to meet these requirements can result in failed audits, contract disqualification, and reputational damage.
Steps to Identify Controlled Unclassified Information
Many organizations fail to protect CUI not because they lack controls, but because they cannot accurately locate or classify the data.
Here are the steps to institutionalize CUI discovery:
- Operationalize CUI Identification
Work with business unit leaders to understand which processes generate or receive government-regulated data. Focus on contracts, supply chains, engineering documentation, bid proposals, and inter-agency communications.
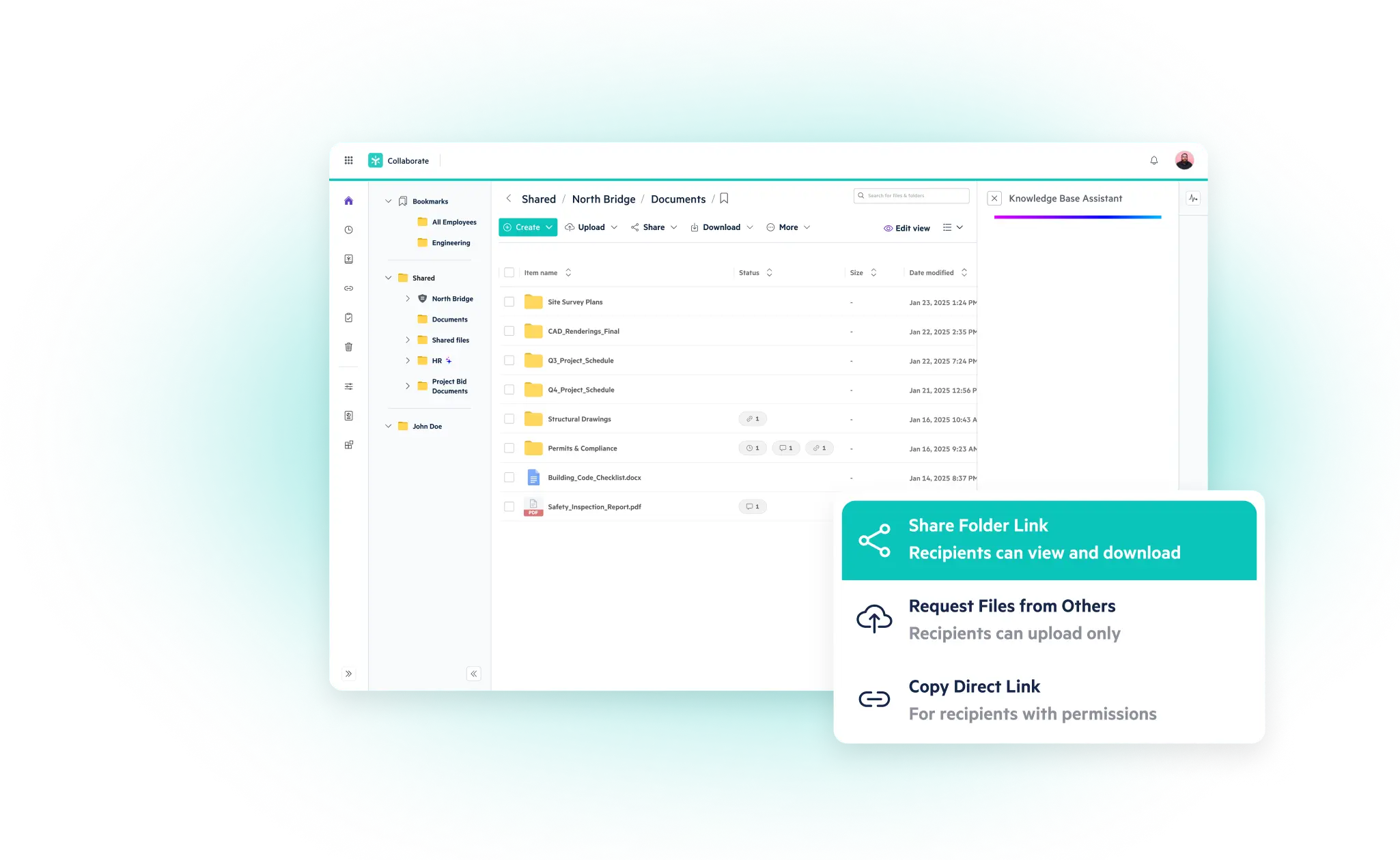
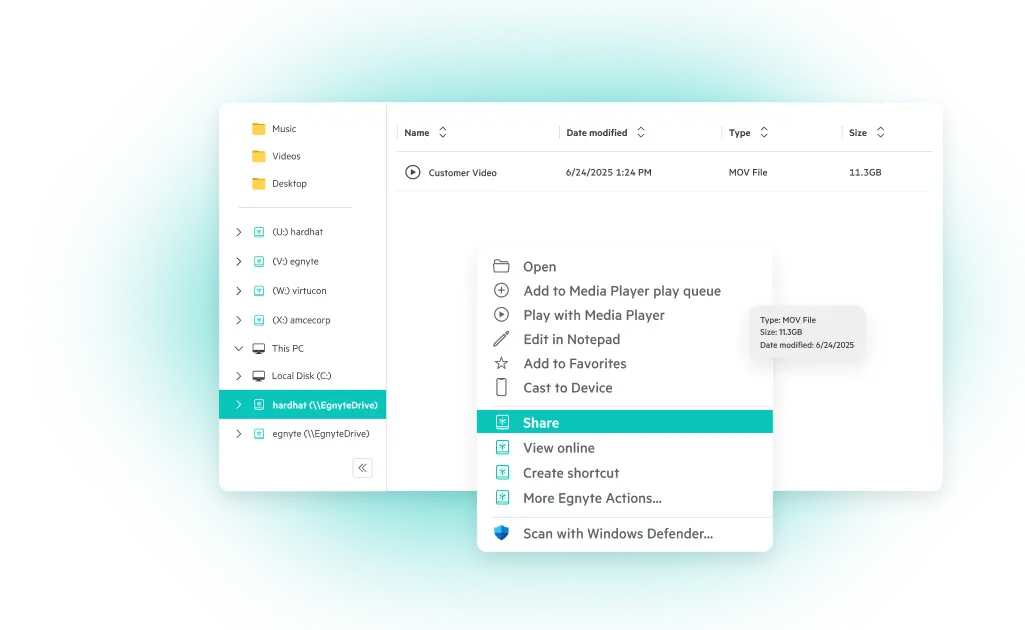
- Use Centralized Discovery Tools
Invest in platforms that scan across cloud repositories, emails, file systems, and collaboration platforms. Tools like Egnyte support automated classification using rule-based detection aligned with the NARA CUI Registry.
- Tag, Label, and Apply Metadata
Once identified, apply machine-readable tags. This facilitates downstream access controls, encryption, and auditability.
- Map CUI Locations to Access Roles
Every CUI asset should have a defined owner and a documented set of access roles. This ensures accountability and simplifies audit trails.
Accurate discovery is not just a compliance step. It reduces the scope of remediation, enables targeted investment, and limits overprotection (which inflates security costs unnecessarily).
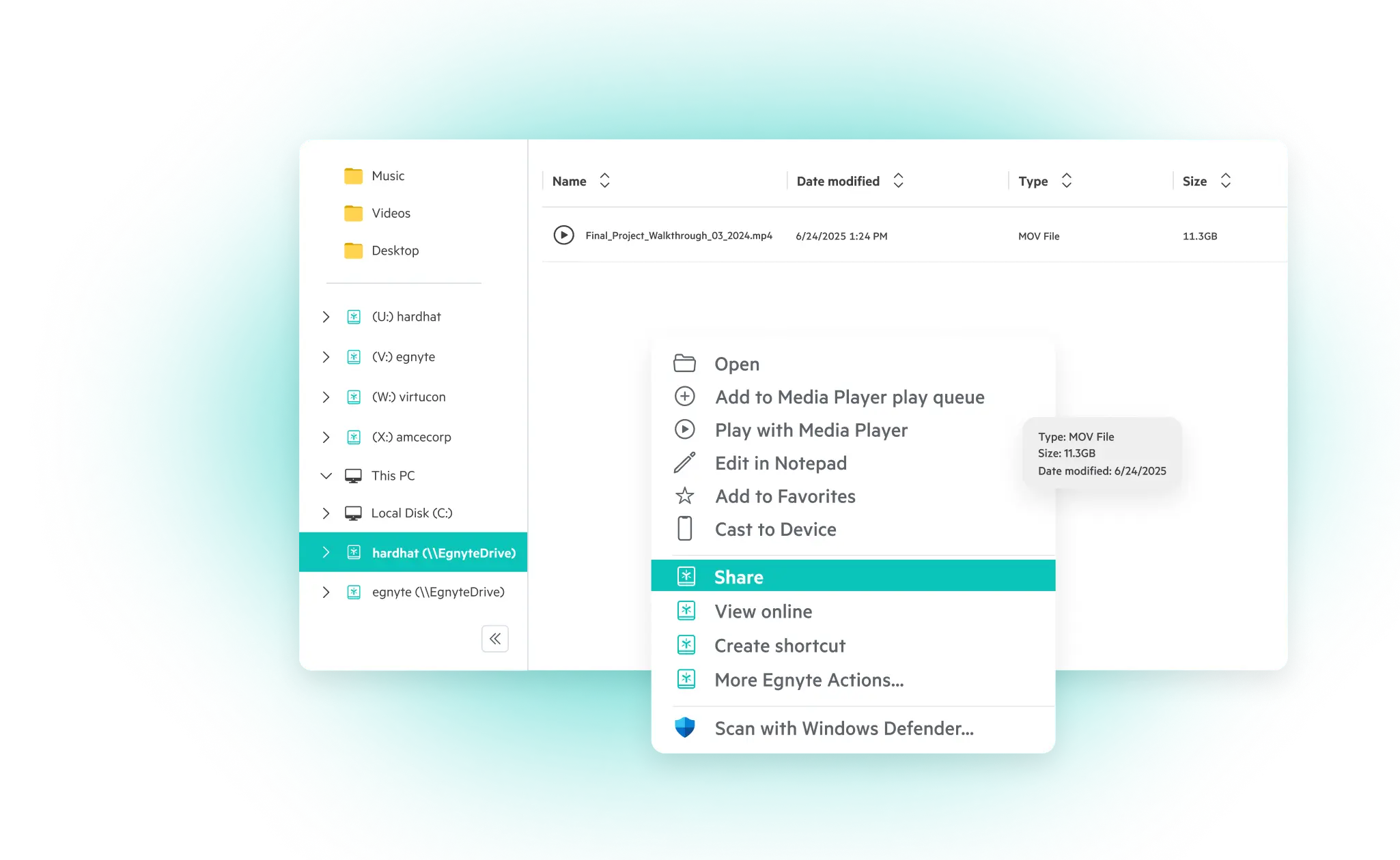
How to Protect the Confidentiality of CUI?
Protecting CUI is a layered process. No single technology solves the problem. Organizations need an integrated framework that combines policy, tooling, and operational discipline.
- Access Controls: Enforce least-privilege access. Tie roles to job functions, not departments. Avoid blanket permissions or shared credentials.
- Authentication Protocols: Deploy multifactor authentication (MFA) and periodic credential rotation.
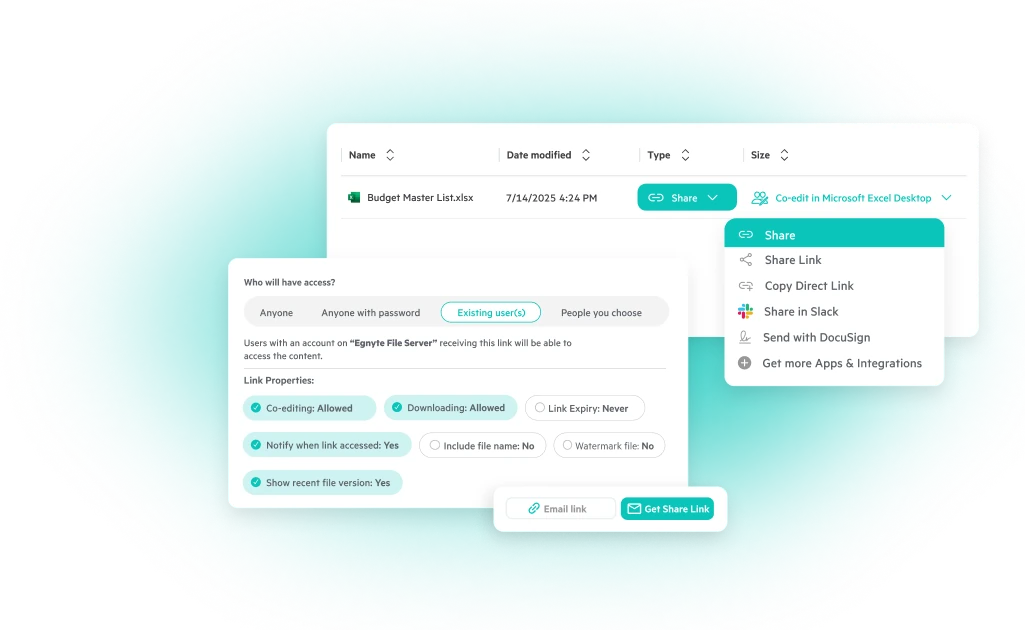
- Encryption Standards: Encrypt CUI both in transit and at rest. Choose solutions that meet FIPS 140-2 standards.
- Activity Monitoring: Implement real-time anomaly detection and audit logs for every system that touches CUI.
- Data Backup and Recovery: Maintain secure, air-gapped backups with routine restoration drills.
- Endpoint Protection: Ensure all user devices have threat detection, patch management, and secure configuration baselines.
- Physical Security: Control physical access to data centers, file rooms, and any off-site storage handling CUI.
Myths That Undermine Effective CUI Protection
Misconceptions about CUI create gaps in enterprise compliance and increase operational risk.
Conclusion
CUI protection is no longer the sole responsibility of the IT department. It is a cross-functional issue that intersects with revenue, operations, procurement, legal, and security.
Organizations that treat CUI protection as a strategic initiative, rather than a tactical fix, are better positioned to win long-term contracts, pass audits with confidence, and maintain a low risk profile in an increasingly regulated environment.
Egnyte enables this enterprise-level discipline. Egnyte’s governance platform brings structure to CUI protection by offering discovery, classification, permission enforcement, and real-time monitoring across hybrid environments. It aligns directly with the technical and policy requirements of CMMC Level 2 and NIST 800-171, helping organizations reduce audit fatigue, maintain trust with federal partners, and demonstrate consistent data stewardship at scale.
Frequently Asked Questions:
Q. What is not considered Controlled Unclassified Information (CUI)?
Public-facing content, such as agency press releases, published research, or data accessible under the Freedom of Information Act, is not CUI. However, when in doubt, refer to the NARA CUI Registry.
Q. Who is responsible for protecting CUI?
Responsibility lies with the prime contractor and any subcontractor who creates, processes, stores, or transmits CUI under the terms of a federal contract.
Q. How does Egnyte help organizations protect and manage CUI securely?
Egnyte offers automated classification, access control enforcement, real-time monitoring, and compliance reporting. It integrates across cloud, on-premises, and hybrid environments, aligning with NIST and CMMC requirements.
Q. How can organizations ensure compliance with CUI regulations?
Establish a governance framework with written policies, use validated security tools, conduct regular internal audits, and ensure employee training is aligned with contract obligations.
Q. What are the risks of not protecting CUI properly?
Risks include disqualification from contracts, breach-related fines, reputational loss, loss of market share, and regulatory penalties. Mishandling CUI also increases exposure to insider threats and third-party risk.
Additional Resources

Controlled Unclassified Information (CUI) - What You Need to Know
Learn what CUI means, why it matters for DoD contractors, and how Egnyte can help you ...

CUI Risk Analysis: Find & Secure Sensitive Data
Quickly find and assess your CUI exposure.

CMMC Requirements: What You Need to Comply
Understand CMMC levels, requirements and compliance standards for DoD contractors.
Data Loss Prevention (DLP): Strategies, Tools, and Best Practices for 2025
In 2025, data is everywhere, and so are the risks around it. Even with the AI-powered containment, the global average cost of a data breach has dropped only 9% to $4.44 million in recent years, where nearly 95% of breaches still stem from human error. That means something as small as sending the wrong file or misconfiguring cloud access can hurt your business in a big way.
This is where Data Loss Prevention (DLP) comes in. It’s a smart safety net, spotting sensitive content before it slips out, steering users back on track, and keeping tight control. DLP helps ensure your important data stays private and your team stays productive, without silencing creativity or slowing you down. In this blog, let us discuss what is data control in detail. Let’s start.
Let’s jump in and learn:
- TL;DR: Data Loss Prevention (DLP) Strategies for 2025
- What Is Data Loss Prevention (DLP) and Why It Matters in 2025?
- How Data Loss Prevention Works: Key Concepts and Mechanisms
- Types of Data Loss Prevention and Their Use Cases
- DLP Best Practices for Effective Protection
- Enforcing DLP Policies Across Systems and Teams
- 2025 Trends in Data Loss Prevention: What’s Next?
- Frequently Asked Questions:
TL;DR: Data Loss Prevention (DLP) Strategies for 2025
- Data Loss Prevention (DLP) is now expected by regulators, customers, and business leaders.
- Endpoint, network, and cloud DLP each cover unique risks; the best approach is layered.
- Automating data loss prevention best practices, like labelling and coaching, reduces friction and risk.
- Modern DLP trends include AI-aware controls, contextual policies, and compliance-ready reporting.
What Is Data Loss Prevention (DLP) and Why It Matters in 2025?
Losing control of this data can result in fines, lawsuits, damage to reputation, or even project shutdowns. That is why data loss prevention (DLP) is a shield for your business’s most valuable asset: Information.
Growing Influence of CISOs in Data Loss Prevention
Ten years ago, the Chief Information Security Officer (CISO) often stayed in the background. Today, they sit in the boardroom because every leak or ransomware attack has a direct impact on business growth.
CISOs now shape DLP strategies to make sure companies don’t just survive audits but also win customer trust. They collaborate with finance, HR, and legal teams to establish data protection as a company-wide discipline.
Compliance Requirements and Stringent Penalties in Data Loss Prevention
Global laws, such as GDPR, HIPAA, and PCI, make data leakage prevention not just good practice but a legal necessity. Penalties can include multi-million-dollar fines and strict reporting obligations. The safer route is to map every policy to a framework and lean on data protection and governance for evidence.
The Impact of Data Explosion on Data Loss Prevention
In 2025, unstructured data is projected to account for over 80% of all enterprise information. This “data sprawl” means sensitive content often hides in unexpected places. With DLP, they can classify, monitor, and protect the right data at the right time, keeping order in the chaos.
How Data Loss Prevention Works: Key Concepts and Mechanisms
DLP generally follows a five-step loop:
- Discover: scan for sensitive files across repositories.
- Classify: assign labels (for example, confidential, internal).
- Monitor: watch file movements like uploads, shares, or prints.
- Enforce: block, encrypt, or warn.
- Report: provide dashboards and audits for compliance.
Types of Data Loss Prevention and Their Use Cases
There are three kinds of data loss prevention as follows:
Endpoint Data Loss Prevention
Endpoint DLP protects devices where sensitive data is often created. It can prevent files from being copied to USB drives, printed, or shared via personal emails. For design firms or financial institutions, this is critical because laptops are frequent leakage points.
Network Data Loss Prevention
Network DLP inspects traffic flowing through gateways, looking for credit card numbers, health records, or other identifiers. It is effective in email and web upload scenarios but keep pace with encrypted protocols.
Cloud Data Loss Prevention
As businesses embrace SaaS, cloud DLP becomes the backbone of modern security. It enforces policies within tools like Office 365, Google Workspace, and Salesforce, flagging unsafe file-sharing practices. Pairing this with types of data security ensures broad coverage.
DLP Best Practices for Effective Protection
- Start with risk-based priorities (for example, customer PII, financial reports)
- Label and classify sensitive documents automatically
- Apply least-privilege and just-in-time access
- Use ‘warn before block’ policies to reduce frustration
- Continuously refine policies to lower false positives
Enforcing DLP Policies Across Systems and Teams
The most successful programs unify policies across endpoint, network, and cloud. Use identity as your anchor: who the user is, what role they have, which device they’re on, and where they’re connecting from. Then let context decide the action. By linking policies to data governance solutions, organizations can show auditors a complete trail.
2025 Trends in Data Loss Prevention: What’s Next?
In 2025, DLP is becoming smarter, quieter, and more adaptive. Policies are shifting from ‘block everything’ to context-aware decisions that consider data type, user role, and the trust level of the app in use.
With more employees pasting sensitive information into GenAI tools, monitoring copy/paste and prompts is emerging as a new priority. At the same time, SaaS sprawl is pushing companies to rely on API-level visibility to catch risks in shadow IT. Privacy-by-default controls, such as disabling external sharing on restricted labels, are also moving from best practice to standard expectation.
This is precisely where Egnyte adds value. Its platform brings together secure file collaboration, intelligent data classification, governance workflows, ransomware detection, and multi-cloud controls into one place.
Frequently Asked Questions:
Q. What is an example of data loss prevention?
Blocking a spreadsheet with 500 unmasked card numbers from being emailed outside the company, the data loss prevention system detects the pattern and stops the send.
Q. What is the difference between DLP and a firewall?
A firewall manages connections, while data loss prevention inspects content. One guards the door; the other checks the package.
Q. What are DLP requirements?
Clear policy, data discovery/classification, monitoring, enforcement, reporting, and governance alignment. Begin by identifying the types of data loss prevention that align with your specific risks.
Q. What is the difference between DLP and antivirus?
Antivirus hunts malware; data loss prevention prevents sensitive content from leaving. Different goals, both needed.
Q. What are the three pillars of data protection?
Confidentiality, integrity, and availability are ensured through controls such as DLP, encryption, backup, and access governance.
Q. How Does Egnyte Help with Construction Engineering Technology?
By unifying project files, enforcing sharing rules, and applying content governance across offices and sites. Integrations with design tools, plus large file collaboration with added security, keep teams fast while data loss prevention policies stay consistent.
Additional Resources

Why FedRAMP Compliance Matters for Egnyte Users
Egnyte’s alignment with FedRAMP standards means lower compliance burden, faster procurement, and trusted security — ideal ...

CMMC Final Rule: What You Must Know
Watch this on-demand webinar to understand the newly published CMMC 2.0 Final Rule — get clear on what's ...

The Future of CMMC 2.0 Compliance
Explore how Egnyte outlines what’s next for CMMC 2.0 — from new DoD mandates and compliance timelines ...
CMMC Compliance Deadline 2025: Critical Timeline for DoD Contractors
The defense industry has entered a make-or-break year in 2025. The CMMC (Cybersecurity Maturity Model Certification) compliance deadline is the barrier between keeping contracts and being shut out. The rule went live in December 2024, and enforcement begins just 60 days after the acquisition rule is published. That gives contractors a short runway to prove they can protect sensitive data.
Yet, reports show more than 16% of contractors report little to no readiness for CMMC. That gap is a warning that half the industry could lose eligibility overnight. This guide lays out the timeline, levels, and steps you need to take now so you don’t become another statistic when deadlines arrive.
Let’s jump in and learn:
- TL;DR: CMMC Compliance Deadline 2025 for DoD Contractors
- CMMC Timeline and Key Compliance Deadlines
- Preparing for DOD CMMC Compliance Deadlines
- Which Companies Require CMMC Compliance?
- CMMC Implementation Timeline: How to Achieve Compliance
- CMMC vs NIST SP 800-171: Understanding the Transition Timeline
- Immediate Actions to Meet CMMC Certification Deadlines
- CMMC Certification Timeline: Plans of Action & Milestones (POA&M)
- Global Impacts and Opportunities from DOD CMMC Timeline
- Conclusion
- Frequently Asked Questions:
TL;DR: CMMC Compliance Deadline 2025 for DoD Contractors
- The CMMC compliance deadline is fast approaching for all DoD contractors handling Controlled Unclassified Information (CUI).
- CMMC implementation is happening in phases, with requirements gradually becoming mandatory. So if you’re compliant with NIST SP 800-171, you're already on the right track for CMMC Level 2.
- Don't wait until the last minute. Solutions like Egnyte's Content Cloud can streamline your path to CMMC compliance.
CMMC Timeline and Key Compliance Deadlines
The CMMC framework is designed to protect sensitive unclassified information (CUI) within the defense industrial base (DIB). While the concept has been around for a few years, 2025 marks a significant point in its full implementation.
Initially, there was a pilot phase, but the DoD CMMC timeline indicates that CMMC will be a contractual requirement for an increasing number of solicitations by late 2024 and fully enforced by October 1, 2025. This means that by fiscal year 2025, a CMMC certification will be a non-negotiable requirement for many new DoD contracts.
Preparing for DOD CMMC Compliance Deadlines
Deadlines land inside solicitations. That means your CMMC compliance deadline will vary by contract, but the window shortens as phases advance. Treat the next quarter as your start line and begin remediation so you can attest or certify on time.
The DoD CMMC timeline and deadline give limited breathing room once the DFARS rule publishes. Consider these initial stages:
- Identify where your CUI resides and who has access to it.
- Conduct an internal assessment against CMMC requirements, often starting with NIST SP 800-171.
- Book a CMCC assessment slot early.
- For Level 2, plan for a C3PAO certification; for Level 1, plan annual self-assessments plus affirmation in SPRS.
- Decide on CUI hosting (enclave vs. enterprise) and MFA/SSO coverage.
- Track costs and timelines in a living POA&M.
Which Companies Require CMMC Compliance?
This is a common question, and the answer is that any company that wishes to bid on or work on a DoD contract that involves CUI will eventually require CMMC compliance. This includes both prime contractors and subcontractors at all tiers.
The level of CMMC required will depend on the sensitivity of the information handled. For most DIB companies, CMMC Level 2 will be the target, as it aligns directly with NIST SP 800-171.
CMMC Implementation Timeline: How to Achieve Compliance
Achieving compliance involves a structured approach. The CMMC implementation timeline can vary for each organization based on its current cybersecurity maturity.
CMMC vs NIST SP 800-171: Understanding the Transition Timeline
CMMC Level 2 is built on NIST SP 800-171, so DFARS 7012 work carries forward. The difference: evidence depth, assessment rigor, and award eligibility.
Immediate Actions to Meet CMMC Certification Deadlines
Given the impending CMMC certification deadline, immediate action is crucial.
- Assign a responsible individual or team to spearhead your CMMC efforts.
- CMMC requires financial investment in tools, training, and potentially third-party services for your CMMC compliance assessment.
- Consider consulting with cybersecurity experts who specialize in CMMC to guide your process.
- Utilize platforms that can assist with content governance, access control, and audit logging.
CMMC Certification Timeline: Plans of Action & Milestones (POA&M)
While the goal is to achieve full compliance before the CMMC certification deadline, the reality is that some organizations may have outstanding items. This is where a POA&M document details a plan for addressing any deficiencies identified during an assessment.
The DoD has indicated that a limited number of POA&Ms might be allowed for CMMC, specifically for CMMC Level 2. However, these will likely be for minor deficiencies that pose a low risk, and they will have strict 180-day timelines for remediation.
The ideal scenario is to have zero POA&Ms, but understanding their role in the CMMC certification timeline is important. It's a temporary measure, not a substitute for complete compliance.
Global Impacts and Opportunities from DOD CMMC Timeline
The DoD CMMC timeline doesn't just impact companies within the United States. Many international companies that are part of the DoD supply chain will also need to achieve CMMC certification. By enhancing your cybersecurity posture, you not only meet a contractual obligation but also:
- Improve overall security: Protect your own intellectual property and sensitive data.
- Gain a competitive advantage: Companies with CMMC certification will be preferred partners for DoD contracts.
- Build trust: Demonstrate a commitment to security, which can lead to new business opportunities beyond the DoD.
Conclusion
By mid-2025, over 58% of DoD contractors still remain unprepared for CMMC, with more than half feeling only slightly or moderately prepared. For many small businesses and defense contractors, this is a wake-up call that if you don’t start now, you will fall behind.
Egnyte cuts through the noise with secure, governed cloud file-sharing, automated policy enforcement, and ready-made audit evidence. It helps you find, govern, and report on CUI securely, simplifies evidence collection, supports MFA and gives guided workflows for reviews.
Frequently Asked Questions:
Q. Are there different CMMC compliance deadlines for prime contractors and subcontractors?
No, both primes and subs see the clause in their awards. Your CMMC compliance deadline depends on your contract and the level of your contract. Plan independently.
Q. How does the phased CMMC implementation timeline affect compliance deadlines?
Phase 1 starts 60 days after 48 CFR publishes with self-assessments. Later phases add third-party certification and some Level 3 over a three-year ramp. Deadlines tighten as phases advance.
Q. What is the difference between the CMMC Final Rule effective date and the compliance deadline?
The 32 CFR rule’s effective date (Dec 16, 2024) made the program active. Your enforceable deadline appears when the DFARS clause shows in a solicitation or award after the 48 CFR rule is final. That’s your CMMC certification deadline.
Q. What happens if a contractor misses the CMMC compliance deadline?
No current certification or required self-assessment in SPRS means you’re ineligible for new awards or task orders once the clauses apply.
Q. How does Egnyte help organizations achieve and maintain CMMC compliance?
Use Egnyte to find and govern CUI, automate policy enforcement, and streamline evidence for audits. Start with a guided CMMC assessment, then a scoped CMMC compliance assessment. Keep artifacts centralized, permissions tight, and monitoring continuous, so the next CMMC compliance deadline is just another date you’re ready for.
Additional Resources

Get ready for CMMC 2.0: Your Checklist Inside
Use this comprehensive checklist to map out key steps — from gap analysis to technical scope and ...

Get Ready for CMMC Compliance with Egnyte
Tap into community insights, downloadable guides, and tailored CMMC tools to streamline your compliance journey — from ...
CMMC Final Rule: What You Must Know
Watch this on-demand webinar to understand the newly published CMMC 2.0 Final Rule — get clear on what's ...
CMMC Compliance Assessment for Data Security and Automation
CMMC compliance assessment is a critical gateway to billions in federal defense contracts. The Department of Defense has established clear cybersecurity requirements. However, organizational readiness remains inconsistent across the defense industrial base. In 2025, reports show that 58% of small and mid-sized contractors still fail basic cybersecurity checks, leaving sensitive Federal Contract Information exposed.
Organizations must change the way they view CMMC assessment. It isn’t a compliance burden but a competitive differentiator that opens access to high-value government contracts, and strengthens overall cybersecurity posture. Early preparation and systematic approach to assessment readiness directly correlate with market positioning and revenue opportunities.
Let’s jump in and learn:
- TL;DR: CMMC Compliance & Data Security Automation
- What is a CMMC Compliance Assessment?
- How Do You Perform a CMMC Compliance Assessment?
- 5 Essential Tips on How Egnyte Helps You Prepare for a CMMC Security Assessment
- How Much Does a CMMC Compliance Assessment Cost?
- Benefits of CMMC Compliance Certification and How Egnyte Supports Assessments
- DoD CMMC Compliance Considerations
- Conclusion
- Frequently Asked Questions:
TL;DR: CMMC Compliance & Data Security Automation
- A CMMC Compliance Assessment verifies if your cybersecurity controls match the DoD standards.
- Level 1 means self-attestation, Level 2 means a mix of self-assessment and certified review, and Level 3 denotes DoD-led evaluation.
- All assessments revolve around Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). NIST 800-171’s 110 practices form the backbone of Level 2.
- Automation tools like Egnyte streamline evidence gathering, monitor anomalies, and cut audit prep time.
What is a CMMC Compliance Assessment?
A CMMC compliance assessment is the structured evaluation that checks whether your organization’s policies, processes, and technologies meet the Department of Defense’s cybersecurity rules. The focus stays on whether or not you can properly protect FCI and CUI. Without passing this, contractors risk losing DoD business.
What Does the CMMC Compliance Assessment Process Consist Of?
The assessment looks at your systems, documents, and day-to-day practices. It includes:
- A scope review (what systems and data are in play)
- Technical testing and interviews
- Review of security policies and evidence logs
- Confirmation of compliance against the NIST-based controls
How Do You Perform a CMMC Compliance Assessment?
A CMMC assessment takes no more than six precise steps. They are as follows:
- Step 1: Determine the Required CMMC Maturity Level
Read the DoD contract clauses. Check if you fall under Level 1, CMMC Level 2, or Level 3.
- Step 2: Identify, Assign, and Engage Internal Stakeholders
Bring in IT, contracts, HR, and leadership. Assign a compliance owner who coordinates timelines and evidence.
- Step 3: Document Where FCI and CUI Exist
Create data flow maps. Note every system, vendor, and endpoint handling sensitive data.
- Step 4: Conduct a CMMC Compliance Gap Analysis
Compare current practices against CMMC compliance requirements. Highlight missing controls and risks.
- Step 5: Measure Performance in Each Practice Area
Test policies, such as password resets, log reviews, and access permissions, in action. Record proof.
- Step 6: Create a Plan of Action and Milestones (POA&M) and a System Security Plan (SSP)
POA&M lists fixes with deadlines. The SSP documents your cybersecurity posture for auditors.
5 Essential Tips on How Egnyte Helps You Prepare for a CMMC Security Assessment
When organizations begin preparing for a CMMC assessment, the first hurdle is often complexity. This is where Egnyte steps in.
Egnyte is an intelligent content governance platform designed for regulated industries. It combines secure collaboration, AI-driven automation, compliance workflows, and real-time monitoring so that contractors can move into CMMC assessments with confidence.
Here’s how Egnyte directly supports your journey:
Data Discovery - Egnyte automatically scans your repositories to identify where FCI and CUI live.
Access Control - Egnyte enforces granular permissioning and integrates with SSO/MFA solutions so that only authorized users can access sensitive files.
Audit Trails - Egnyte’s audit logs and reporting dashboards create that evidence for you, tracking file access, downloads, edits, and sharing activities automatically.
Automation - Egnyte’s AI agents handle repetitive tasks, like tagging files, monitoring anomalies, reducing human errors, and preparing compliance reports.
Ransomware Detection - If ransomware or unauthorized activity is detected, Egnyte triggers real-time alerts and remediation workflows.
How Much Does a CMMC Compliance Assessment Cost?
Investment planning for CMMC assessment requires understanding both direct and indirect costs across compliance levels. Self-assessment at Level 1 may cost a few thousand dollars in staff time ($3,000 to $5,000). Level 2 third-party reviews often range from $30,000 to $75,000. Level 3 runs higher, given DoD oversight.
Egnyte reduces costs by:
- Centralizing evidence collection
- Automating the classification of sensitive files
- Cutting prep time for audits through reusable compliance dashboards
Benefits of CMMC Compliance Certification and How Egnyte Supports Assessments
- Eligibility: Win DoD contracts that demand certification.
- Trust: Demonstrate secure handling of sensitive defense data.
- Efficiency: Automated workflows save man-hours.
- Resilience: Stronger protection against insider risks and ransomware.
Egnyte’s platform ties all of this into a single pane of glass, helping you move from prep to certification faster.
DoD CMMC Compliance Considerations
The Department of Defense & CMMC require flow-down compliance. Subcontractors handling sensitive data must also meet the required level, and missing the CMMC compliance deadline could mean losing future contracts. With Egnyte’s unified approach, organizations not only prepare faster but also secure long-term resilience.
Conclusion
A CMMC compliance assessment is the credential that lets you bid, win, and deliver DoD work. Organizations that approach assessment preparation systematically and invest in the right technology platforms position themselves for sustained growth in defense markets. Organizations that master CMMC requirements early will capture disproportionate market share as competitors struggle with compliance gaps.
By mid‑2025, only about 46% of Defense Industrial Base contractors felt ready for CMMC Level 2 certification, even as deadlines draw near. When organizational resilience matters most, Egnyte is your industry-tailored ally, offering unified data governance, automated compliance tracking, secure access controls, and audit-ready dashboards.
Frequently Asked Questions:
Q. Who needs to complete a CMMC assessment, and at what level?
All DoD contractors. The required level depends on the type of data, such as FCI (Level 1), CUI (Level 2), or advanced (Level 3).
Q. Which organizations require third-party CMMC assessments, and which can self-attest?
Level 1 is self-attestation. Some CMMC Level 2 contracts allow self-assessment; higher-risk contracts demand third-party reviews.
Q. How often do CMMC assessments or certifications need to be renewed?
CMMC self-assessments must be renewed yearly, while third-party certifications remain valid for three years before requiring re-evaluation.
Q. How does Egnyte help customers streamline their CMMC compliance assessment process?
By automating sensitive data discovery, generating audit logs, and offering dashboards for faster reporting.
Q. How is the CMMC compliance checklist used in preparing for certification?
It serves as a roadmap, ensuring your organization maps data, closes gaps, and is audit-ready.
Additional Resources

The Future of CMMC 2.0 Compliance
Explore how Egnyte outlines what’s next for CMMC 2.0 — from new DoD mandates and compliance timelines ...

Join the Egnyte CMMC Community
Get access to expert-led webinars, a comprehensive CMMC compliance checklist, and peer insights — everything you need ...

Is Your Team Ready for CMMC 2.0?
Join the webinar to understand the latest CMMC standards, deadlines, and key compliance steps required by ...
CMMC Assessment Requirements and Certification Process
Winning DoD (Department of Defense) work now depends on showing you can protect FCI (Federal Contract Information) and CUI (Controlled Unclassified Information), not just thinking about how easy it will be. CMMC 2.0 (Cybersecurity Maturity Model Certification) turns that promise into proof through an assessment tied to your contract.
In 2025, the DoD stated that once the Title 48 acquisition rule takes effect, CMMC requirements will enter solicitations in four phases over three years. Moreover, the assessment ecosystem is growing; by June 2025, there were 70 authorized C3PAOs and 364 certified assessors, and many are booking three to six months ahead.
All of these make CMMC preparation a near-term goal, which you cannot delay or slow down. This guide walks you through what the assessment checks, how certification works, and practical steps to get audit-ready without stalling day-to-day work for contractors.
Let’s jump in and learn:
- TL;DR: CMMC Assessment Requirements and the Full Certification Workflow
- What Is a CMMC Assessment?
- Who Needs CMMC Certification?
- Levels of CMMC Compliance
- CMMC Compliance Timelines
- Preparation Makes a CMMC Assessment Easier and Improves Overall Security
- Common Challenges and Mistakes in a CMMC Assessment
- How Egnyte Helps Address CMMC Compliance Challenges
- Conclusion
- Frequently Asked Questions
TL;DR: CMMC Assessment Requirements and the Full Certification Workflow
- A CMMC assessment validates if your security controls meet DoD standards for FCI and CUI.
- CMMC 2.0 has three levels: Level 1 self-assessment, CMMC Level 2 (often third-party), and Level 3 (government-led).
- The official CMMC assessment process follows Cyber AB’s CAP model: preparation, assessment, reporting, and certification.
- The CMMC compliance deadline is phasing into DoD contracts by late 2025. Starting a CMMC readiness assessment improves bid eligibility and reduces audit pain.
What Is a CMMC Assessment?
A CMMC assessment is a formal evaluation of a company's cybersecurity practices. This is how the DoD confirms that an organization has put in place the security measures needed to protect sensitive government information.
The assessment process is carried out by a certified third-party organization (C3PAO), or, for some lower levels, a CMMC self-assessment is permitted. The goal here is to ensure that a company is actually implementing a robust and mature cybersecurity program.
Who Needs CMMC Certification?
If your organization is part of the Defense Industrial Base (DIB), you need CMMC certification. This includes any company that directly contracts with the Department of Defense & CMMC, as well as their subcontractors, suppliers, and vendors who handle CUI. Even if you only handle FCI, you will still need to meet certain CMMC requirements.
The CMMC framework applies to more than 300,000 businesses. The requirement is a critical component of the cybersecurity maturity assessment needed to be eligible for DoD contracts. The need for CMMC certification applies to contracts awarded after the CMMC compliance deadline.
Levels of CMMC Compliance
The CMMC framework has three levels, each with increasing requirements for protecting sensitive information.
Level 1: Foundational
Level 1 is for organizations that only handle FCI. The requirements here are foundational and focus on basic cyber hygiene. A CMMC Level 1 self-assessment must be performed annually.
Level 2: Advanced
Organizations that handle CUI must achieve CMMC Level 2. This level is based on the 110 security controls from NIST SP 800-171. The CMMC compliance assessment can be a third-party assessment for some contracts or a CMMC self-assessment for others, depending on the type of information handled.
Level 3: Expert
This level is for organizations that handle CUI for the highest priority programs. It requires a government-led assessment to verify that an organization has implemented the 110 controls from NIST SP 800-171 plus a subset of controls from NIST SP 800-172.
CMMC Compliance Timelines
The final rule codifying CMMC was published in October 2024. Enforcement begins 60 days later, with a three-year phase-in across contracts. By late 2025, most new contracts will include CMMC language.
Assessment Process Overview
- Preparation: Internal gap analysis or CMMC readiness assessment.
- Assessment: Self-assessment or third-party review.
- Reporting: Draft and final report, with findings and POA&Ms.
- Certification: Issued if all requirements are satisfied.
Preparation Makes a CMMC Assessment Easier and Improves Overall Security
Preparation saves money and reduces stress. Best practices include:
- Running a cybersecurity maturity assessment early.
- Conducting a mock CMMC self-assessment to validate evidence.
- Using automation to classify and protect CUI.
- Training staff to reduce user-related findings.
Organizations that treat compliance as an ongoing program, not a one-time event, to achieve faster certifications.
Common Challenges and Mistakes in a CMMC Assessment
Navigating the CMMC assessment process can be challenging. Many organizations make common mistakes, such as:
- An SSP is a live document, and failing to keep it up to date is a huge mistake.
- Just because you use a cloud service doesn't mean your data is secure. You are responsible for configuring your cloud environment securely.
- Preparing for a CMMC assessment is a big project that requires time, resources, and a dedicated team.
How Egnyte Helps Address CMMC Compliance Challenges
Egnyte’s secure content platform is an ideal tool to help you meet CMMC compliance requirements. We specialize in helping organizations protect, manage, and collaborate on sensitive data.
Our solution helps you automate key security practices, reducing the manual effort required and lowering the risk of human error. This way, you can:
- Meet many of the CMMC controls, especially those related to access control, media protection, and data security.
- With Egnyte, you can centralize your data and gain visibility, making it easier to show an assessor that you have the proper controls in place.
- Egnyte’s platform provides the detailed logging and auditing capabilities needed for a strong SSP.
Conclusion
The CMMC assessment may seem like a huge hurdle, but it's a completely achievable mission with the right approach. Yet, with the deadline approaching quickly, 70% of contractors have budgeted far less than the actual cost of a Level 2 assessment, creating a massive preparation gap.
However, a strong plan and the right tools can make all the difference. Egnyte is the industry-leading solution for secure collaboration and data governance. Our platform provides the comprehensive tools needed to manage your CUI and get your documentation in order, simplifying the entire assessment process.
Frequently Asked Questions
Q. What is the difference between a CMMC self-assessment and a third-party assessment?
A CMMC self-assessment is done internally by the contractor and affirmed by leadership. A third-party assessment is performed by a C3PAO, with independent evidence testing and higher scrutiny.
Q. How often do CMMC assessments occur?
Level 1 requires an annual self-assessment. Level 2 may involve either annual self-attestation or triennial third-party certification. Level 3 is government-led, with frequency based on contract terms.
Q. What are the costs associated with a CMMC assessment?
Costs vary by level and scope. Level 1 self-assessments are low-cost but require staff time. Third-party CMMC assessment processes can range from tens to hundreds of thousands of dollars, depending on system size and readiness.
Q. What happens if an organization fails a CMMC assessment?
You cannot receive certification and may lose eligibility for contracts. However, you can remediate gaps, update your POA&M, and request reassessment.
Q. How does Egnyte support organizations in their CMMC assessment journey?
Egnyte helps by automating CUI discovery, managing permissions, maintaining audit-ready logs, and providing continuous monitoring. These capabilities streamline preparation and reduce assessment risk.
Additional Resources

CMMC Assessment Guide
Quickly assess your DoD readiness with Egnyte’s CMMC process, focused on verifying cybersecurity controls for ...

CMMC Deadline 2025
The guide outlines key 2025 CMMC deadlines and what contractors must do to stay compliant as enforcement ...

CMMC Framework Overview
The guide breaks down the CMMC framework’s three maturity levels and core cybersecurity requirements for ...