What Is Data Protection? A Complete Guide for Businesses
The more data a business handles, the greater the risk it carries. Financial records, customer profiles, and identity-linked information are no longer just operational assets. They are high-value targets for cybercriminals and subject to intense regulatory oversight. Yet in many organizations, the protection of this data remains fragmented, often treated as a technical issue rather than a business-critical function.
Regulatory frameworks such as the Data Protection Act demand far more than baseline compliance. At the same time, the cost of breaches is growing, not only in terms of financial penalties but also reputational damage and loss of stakeholder trust.
This article outlines what financial data protection really involves, why it deserves cross-functional attention, and how organizations can build safeguards that protect sensitive information without compromising business performance.
Let’s jump in and learn:
- What Is Data Protection and How Does It Relate to Privacy?
- Why Data Protection Matters for Businesses and Customers
- Top Data Protection Technologies and Software for Security
- Data Protection Regulations and Compliance Standards
- Challenges To Data Protection and How to Address
- The Egnyte Advantage: From Compliance Risk to Data Control
- Case Study:
- Conclusion
- Frequently Asked Questions
What Is Data Protection and How Does It Relate to Privacy?
Data protection refers to the systems and practices that secure sensitive information from unauthorised access, loss, or misuse. This includes encryption, access controls, secure storage, and compliance with frameworks like GDPR or HIPAA. Its goal is to keep data accurate, secure, and available.
Data privacy, on the other hand, governs how personal information is collected, used, and shared. It demands transparency, consent, and minimal data usage.
Protection secures the infrastructure. Privacy ensures ethical handling. Together, they reduce regulatory risk, support business continuity, and strengthen customer trust.
Why Data Protection Matters for Businesses and Customers
- Prevents unauthorised access to sensitive business and customer data.
- Reduces the risk of financial loss due to data breaches.
- Ensures compliance with data protection regulations like GDPR and HIPAA.
- Maintains operational continuity by protecting critical information assets.
- Preserves customer trust through responsible data handling.
- Safeguards intellectual property and proprietary business information.
- Minimises reputational damage following security incidents.
- Supports secure digital transformation and cloud adoption.
- Enables data availability and integrity for informed decision-making.
- Aligns cybersecurity with business risk management strategies
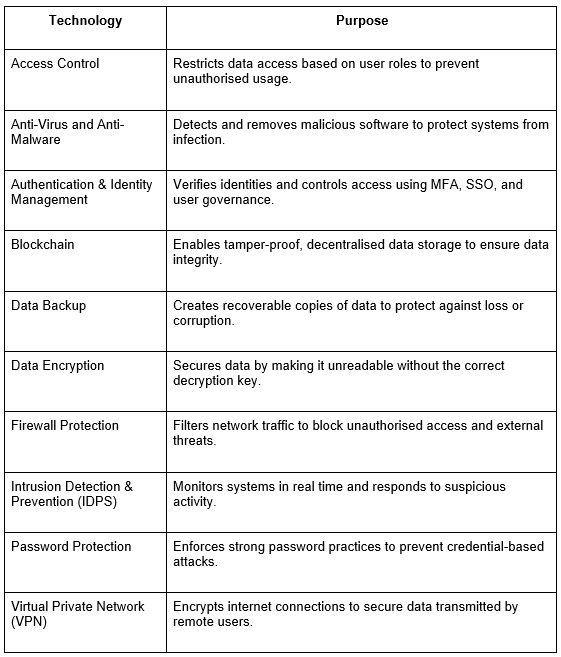
Top Data Protection Technologies and Software for Security
Modern data protection solutions rely on a layered approach that combines multiple technologies to prevent unauthorised access, detect threats, and ensure data resilience. Below are key tools that support a comprehensive protection strategy:
Data Protection Regulations and Compliance Standards
- Federal Data Protection Regulations: HIPAA protects patient health data, FERPA student records, and GLBA financial data.
- State Data Protection Legislation: The California Consumer Privacy Act lets you see and delete your data. Virginia's CDPA offers privacy rights similar to those provided by federal laws.
- Industry-Specific Data Protection Legislation: In the US, hospitals follow HIPAA, banks use GLBA, and schools follow FERPA. In the EU, GDPR keeps online data like names and emails safe.
- Global Data Protection Legislation: Europe's GDPR is strict. It gives people control over their data. Singapore uses PDPA to protect info, too.
Challenges To Data Protection and How to Address
- Evolving threats make it difficult to keep security measures up to date.
- Poor access controls increase the risk of unauthorised data exposure.
- Insider misuse or negligence can lead to critical data leaks.
- Data silos limit visibility and weaken protection efforts.
- Unencrypted data is vulnerable during transfer or storage.
- Third-party vendors can introduce security gaps.
- Complex regulations create compliance and operational pressure.
- Budget and resource constraints slow down security investments.
- Shadow IT bypasses enterprise-level data protection controls.
- Slow incident response increases the impact of breaches
The Egnyte Advantage: From Compliance Risk to Data Control
Egnyte Intelligence is the heart of a unified platform built for enterprise-scale file collaboration and governance. It helps organizations not only share content securely but also manage the entire lifecycle of unstructured data with precision. By combining secure collaboration tools with AI-driven content governance, Egnyte enables businesses to reduce compliance risk, gain real-time visibility, and maintain control over sensitive information, regardless of location.
Egnyte Intelligence uses advanced machine learning to automatically classify sensitive content, detect policy violations, and identify unusual behaviour before they escalate into breaches. The AI Copilot and configurable AI agents simplify natural-language search, summarise documents, extract metadata, and trigger automated workflows. These features move organizations from reactive rule enforcement to proactive, insight-driven governance.
Case Study:
Optimal Risk Strengthens Client Trust with Enterprise-Grade Data Security
Optimal Risk Group, a consultancy that safeguards highly sensitive global assets, needed a scalable system for managing unstructured data, satisfying ISO 27001 compliance, and offering verifiable proof of security to its clients. Legacy tools such as SharePoint no longer met the mark.
Egnyte was the solution. With its rich security suite and intelligent governance engine, it delivered:
- Role-based access control and secure link sharing
- Automated lifecycle policies to keep data exposure minimal
- Full audit trails tracking every file interaction
- Real-time dashboards exposing governance gaps
- Built-in ISO 27001–aligned compliance monitoring
Optimal Risk now delivers demonstrable security to its high-stakes clientele, winning trust, securing contracts, and simplifying internal workflows. Egnyte has become a core pillar of the company’s ability to manage risk, ensure data integrity, and drive business growth through transparency and confidence.
Conclusion
Safeguarding sensitive business data is a fundamental requirement for operational resilience. In a landscape shaped by rising cyber threats and complex regulations, data protection is no longer optional. The cost of a single breach extends far beyond compliance fines, often impacting brand credibility, stakeholder trust, and business continuity. Robust protection ensures that critical information remains secure, accessible, and aligned with regulatory standards at every stage.
Egnyte provides exactly that. Its platform secures files across locations and devices, intelligently identifies sensitive content, and enforces compliance with evolving regulations. Whether it is a targeted attack, system failure, or simple human error, Egnyte helps you prevent data loss and recover critical assets quickly. With AI‑enhanced classification, search, and automation, Egnyte transforms compliance from a burden into a strategic advantage, allowing businesses to focus on growth with confidence.
Frequently Asked Questions
Q. Why Should Businesses Care About Data Protection?
If a business fails to protect people's data, it can lose trust, face legal trouble, and incur significant fines.
Q. What Is the Purpose or Main Goal of Data Protection?
The main goal is to keep personal information safe from being stolen, misused, or lost. It ensures data remains private and is only accessible to the right people.
Q. What Are the Consequences of Not Having Data Protection?
This can cause identity theft, money loss, and legal actions. People may stop trusting the company.
Q. Who Is Responsible for Data Protection?
Everyone in a company is responsible, but the business owners, managers, and IT teams bear the primary responsibility. They must follow laws and use tools to protect data.
Q. What Are My Rights Under Data Protection?
You have the right to know how your data is used, to ask for a copy of it, to fix wrong details, and to ask for your data to be deleted. You can also complain if your data is misused.
Additional Resources

Financial Privacy Guide
Explore the financial data covered under privacy laws, what CFPA and GLBA require, and how to ...

What Is a DPO
Learn what DPOs do, when they’re required under laws like GDPR, and how they help ...

What Is GDPR: Complete Guide
Learn how GDPR works, who it applies to, key data rights, compliance steps, and what organizations ...