
Empower Users to Securely Access and Share Data
If the past several years of technology advancements, pandemic adjustments, and increased cyber threats has taught us anything, it’s that data security and governance are the responsibility of the entire corporate team.
Of course, the primary responsibility rests with the executives and the CISO or security team they’ve empowered, but the scope and scale of protecting critical data assets is too large for any single business unit to tackle. It requires a team effort that depends on every single employee at your company.
In this blog, we’ll highlight why you need everyone engaged in content security and governance. Then, we’ll review the types of considerations that will impact your approach, and we’ll provide practical tips for getting everyone onboard.
Why Data Security and Governance Requires a Team Effort
A company-wide approach to data security and governance is more clearly understood when you consider that data sprawl is a major challenge for IT and security leaders. Egnyte’s 2022 "Cybersecurity Trends for Mid-sized Organizations" report found that 86% of organizations manage between six and 15 disparate data repositories.
To add to this data sprawl concern, the CIOs and IT leaders surveyed estimate that 49% of their company files contain sensitive information such as personally identifiable information, credit card numbers, and other regulated sensitive data, according to the 2021 Egnyte Data Governance Trends Report. And more concerning, that same report found 65% of respondents suspect employees are storing files and documents with sensitive data directly to their personal devices.
On top of all that, companies today face so many different security and governance challenges that they’re split on what to prioritize with their limited resources, as the chart below illustrates. Taken collectively, it’s clear that businesses need everyone to pitch in.
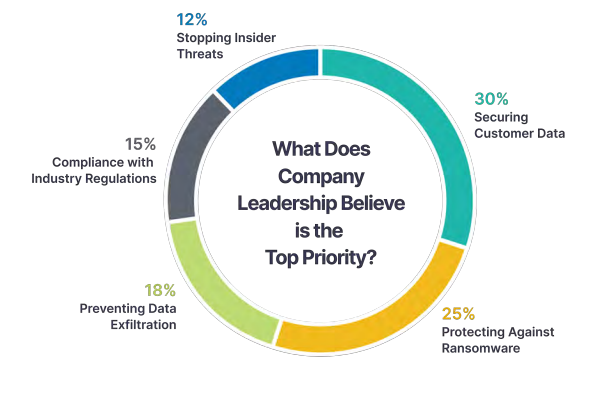
The good news is there are some trends working in your favor. End users are more digitally savvy than ever. Meanwhile, IT is no longer seen as just a blocker to other users—increasingly, IT is an enabler and partner with the rest of the business. By making cybersecurity and governance a team effort, you have a great opportunity to leverage those changing dynamics to improve productivity and cyber protections for everyone.
How to Empower Users to Securely Access and Share Data
Define Your Team
Your team approach to data security and governance will differ based on:
- Your company size. The number of resources, budget size and supporting technology will change how you approach your team. What is important is that you engage everyone and communicate the importance of data security.
- Any relevant regulations. Every business is subject to at least some data privacy law, and more are coming
- Your risk posture. If you haven’t defined this, now is a good time to do so
Regardless of your company size and risk position, your data security and governance plan will include technology, people, and processes to determine data accessibility, security, ownership, quality and management.
The people or team aspect of your plan should take into consideration the roles that you have or will need to define within your company:
- Data Officer. These individuals often have overall responsibility and accountability for your organization’s data governance program.
- Data Governance Council. This group is typically made up of execs from all business units. They set data policies, standards, and resolve issues.
- Data Governance Team. A data governance manager usually heads up this team, which may include data architects and governance specialists.
- Data Stewards. These are your subject matter experts (SMEs) that oversee data sets and are in charge of implementing governance policies and monitoring compliance with them.
- Advocates and Evangelists. While IT and executives are the main drivers, designated business users can help carry your message with their peers and provide important feedback on what is and isn’t working.
Engage, Train, and Coach the Team
Once you’ve identified your team, they need to take the lead in getting company-wide adoption of cybersecurity best practices. Here are some key techniques you can implement—and continually reinforce—to get the best out of everyone.
Get Everyone Trained
Just as it is with any good team, practice is vital. And cybersecurity training is becoming a bigger focus for companies, with 63% of respondents to Egnyte’s 2022 cybersecurity trends report currently conducting training on at least a quarterly basis. The team needs to understand what data security is, why it is important to your company, and how they can participate to protect sensitive data.
Utilize Policies to Guard Against User Apathy
This is where technology is paired with people and processes to ensure your employees are doing things the right way. Inevitably, your team will forget their training or do whatever workaround easiest for them. And in some situations, they will be the insider threat to your data as they attempt to take data before they leave your company, or share it with someone outside your company.
One of the best ways to empower your users is to put in guardrails that give them the confidence to effectively protect data. Data security policies such as these will help you to remind and even enforce your data protection:
Content Safeguards. Define what data is sensitive through data discovery and categorization technology. Then, apply rules for external sharing based on these categorizations. These rules should enable you to perform tasks like:
- Restrict sharing of defined data
- Require passwords for file sharing
- Allow previews only
- Restrict downloads
- Send encrypted data that only specified recipients can decrypt and view
Make sure files are shared through links, so these safeguards can be properly applied; don’t send the actual documents.
Content Lifecycle Policies. Data gets stale or duplicative, but the sensitive data within the files still needs to be protected. Increase your ability to protect data by creating content lifecycle policies to automatically archive, delete, or retain data based on location, project type, file age, and metadata tags.
Insider and External Threat Monitoring. Despite your best efforts, there will still be insider threats and external breach, usually due to negligence. To detect these threats, apply policies such as suspicious-login detection and unusual-access monitoring.
- Utilize technology that detects login attempts from IP addresses outside of whitelisted ranges, outside of normal access periods, or attempts that are miles and countries apart from normal user access points.
- Behavioral algorithms can alert you to unusual access by monitoring user behavior for which files are accessed, when they are accessed, how many files are accessed.
Recovery from Ransomware or Malicious File Deletion. Even with policies in place, you will likely experience ransomware encryption or malicious file deletion that can leave your company crippled. Your team must be able to recover from these events by rolling impacted files, directories, or even the entire file structure back to the way it was before the ransomware encryption or deletion.
Ensure Data Is Appropriately Accessible Across the Organization
Make sure to empower your SMEs across business units as part of your data security and governance plan. Enable them to perform scheduled data permission reviews to ensure only approved and necessary personnel have access to sensitive data. This allows you to enforce a business-need-to-know model.
Set Up End Users for Success
People are more likely to do their part when they have skin in the game, which is why it’s so important to empower your end users to participate in the protection of your company’s sensitive data. You shouldn’t expect them to be cybersecurity experts, nor should you give them free rein. But, with the proper guardrails in place, they can have some leeway to make the right decisions. You can even add warnings about the implications of sharing data, without actually preventing them from doing so. That way, users will be understand the risk while still being able to do more without having to put in special requests to IT.
Ultimately, if you get users more involved, they’re more likely to understand why certain decisions are made and why you’re promoting certain behaviors. This can foster better partnerships, so end users are more inclined to help instead of getting annoyed and trying to find ways to work around IT.
Learn More
Data security and governance is getting harder as insider threats and external bad actors up their game to target your data—specifically, the sensitive data that you collect, store, and use. And the rules for maintaining this sensitive data will only get more complex amid mounting momentum for a federal privacy law.
Small, medium, and large companies alike need effective technology, appropriate processes, and the support of a trained and governed team to protect their critical and sensitive data. Your security or IT team can’t do it on its own. To learn more about how companies are adapting to these shifting demands, follow the link below to read the 2022 cybersecurity trends report discussed throughout this article.






