
Maximizing Content Security: Considering User Experience
In developing any content platform, it’s important to strike a balance between usability and security. We always have our ears open for new features our customers want and are always looking for ways to adapt emerging technology for our stack.The main question that prompted the creation of our new security infographic was, “after we put in all the bells and whistles for IT, what are end users really doing?” Beyond that, we saw an opportunity to share insights from our customers on how to prioritize data security: how do customers compare to industry benchmark? What were their peers doing? What security features might they not be aware of?Egnyte Connect’s security features run the full gamut, from features that require active participation from users like two factor authentication to features that require no user participation at all, like end-to-end encryption. Which security features were turned on the most by our customers? Which were used the least? And why?Those were our research questions. But as is often the case, the data told its own story.There are two or three really important takeaways you can find in our infographic. A lot of IT admins, first, use security features more sparingly if they have a high impact on user experience. It’s illuminating that, when given a choice, IT admins prefer to remove obstacles to productivity.

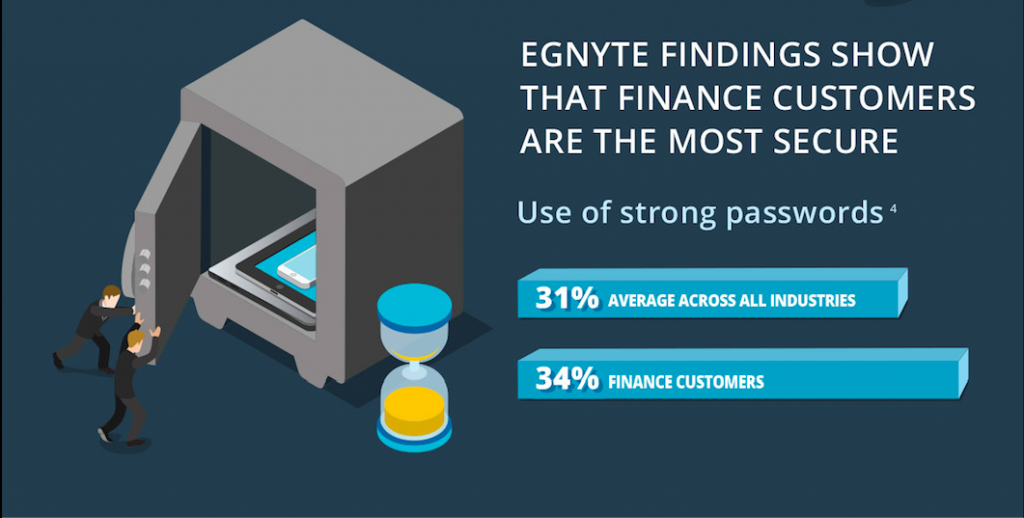
Take the security features that strongly impact UX, for instance. These are some of the most complex security technologies available. Given the fact that we are always looking to leverage new technologies, we make sure to incorporate all these features into our offerings, yet fewer than 10% of IT admins deploy some of them.Features that do not directly impact users’ workflow (and, by extension, do not impact productivity) enjoy much greater adoption. While certain features make the sign-on process more comprehensive and secure, they also increase the level of complexity and user dissatisfaction. As a result, IT admins opt to strengthen the credentials instead, with features like strong password requirements.And when a feature runs invisibly in the background, like end-to-end encryption, its deployment is universal.While a lot of our findings weren’t surprising--financial companies being among the most protective of their data, for instance--some were. My perspective on the tug-of-war was that security should trump almost everything else. I personally would rather jump through a few hoops to make sure my company intellectual property is protected. What this research suggests, instead, is that it may be confusing or even unproductive for users who are not well versed in IT to struggle with advanced security features.
When security is prioritized above all else, features with high user impact can create more problems than they solve. Consider the example of password reuse. Some companies require users to change passwords every 180 days. Others require passwords to be changed every 90 days.If you use this feature in conjunction with a ‘can’t reuse last x passwords’ rule, you force users to go to greater lengths to keep their constantly-changing passwords straight. An IT admin can impose extremely complex, secure password requirements, only for a hapless end user to write down their passwords on paper easily spotted on their desk.On the list of outcomes the IT admin hoped for, ‘fostering pen-and-paper shadow IT’ is probably nowhere to be found. Yet that’s our biggest takeaway, and the most surprising one. When leveraging security features, businesses used to believe more is always better. Today, they are learning to be surgical.To learn more about the growing costs of a data breach, download the full infographic.





